In an era where cyber threats like SocGholish are becoming increasingly sophisticated, understanding and combating these attacks is crucial for digital safety. This post delves into leveraging Huntress for effectively handling SocGholish threats, outlining a step-by-step approach for IT professionals.
What is SocGholish?
SocGholish is a malware framework that uses social engineering, where cybercriminals masquerading as trustworthy entities trick users into performing harmful actions such as clicking malicious links, or in the case of SocGholish, downloading infected updates. This tactic's effectiveness lies in its deceit, often leading to significant security breaches.
The Huntress Process
Identify Suspicious Activity
Upon noticing a user running a suspicious JavaScript file named [.highlight]Update.js[.highlight], our first step at Huntress is to identify the originating browser. In this case, it’s Google Chrome.

Analyze Browser History
We then retrieve the Chrome browser history logs, and the suspicious [.highlight]Update.js[.highlight] file, to gather more context on the attack. Concurrently, we review other ongoing processes, although in this instance, it wasn't necessary.

Extract Crucial Data
Utilizing tools like SQLite3, we analyze the browser history. For those unfamiliar, SQLite is a database engine that can be easily navigated using specific commands. Within the Terminal you can open a History file by naming it with a [.highlight].sql[.highlight] extension. Once you navigate to the directory with your [.highlight].sql[.highlight] file, you can open the file with the terminal command [.highlight]Sqlite3 “file.sql”[.highlight]. Once opened, we can run [.highlight].excel[.highlight] to have our request open formatted as comma separated values (CSV). We then use the command [.highlight]Select * from downloads;[.highlight] to extract all data from the downloads table, formatted in CSV for ease of analysis.


Discovery and Reporting
Our analysis revealed the last entry in the user’s browser history as a critical point—the user downloaded the malicious file from a suspicious domain [.highlight]https[:]//racerex[.]com/its-fire-up-season/[.highlight]. Taking a scan of this website revealed a WordPress site of someone's personal blog that had been hacked to redirect users without their knowledge to the site that hosts the malicious javascript. [.highlight]assay[.]porchlightcommunity[.]org/03j7jahamOS3WsG/5UDXr6ARn6/pT8m/[.highlight] to download the malicious SocGholish file.


The domain [.highlight]assay[.]porchlightcommunity[.]org[.highlight] above hosts the heavily obfuscated script that can be seen here, https://urlscan.io/responses/c552e5662a4e516087804b653d069a41d02154053a2671b9f9b489ab4c5eefd8/.
If we de-obfuscate the script using [.highlight]https://obf-io.deobfuscate.io/[.highlight] we can see that the script then attempts to pull the next stage using these domains:
1.[.highlight]hxxps[://]assay[.]porchlightcommunity[.]org/kbI7y+qQWKL1kAH5p4oX6eLGXruziBm749dYo/TRUJT7wWSt491Vv/TASaTjkBfp9MBJpOOQAfq9kEnpq5BNp/bLGbY=[.highlight]
2.[.highlight]hxxps[://]assay[.]porchlightcommunity[.]org/Q7kAIzibY0onmzoRdYEsATDNZVNhgyJTMdxjSybaa3wpyl9FMdZuVybLckwxmywBJstyTDGbOhFvm3IBeZtjVmHE[.highlight]
3. [.highlight]hxxps[://]assay[.]porchlightcommunity[.]org/3TLWUaYQtTi5EOxj6wr6c65GsyH/CPQws1O6KKdXiTetEPpzrxDsc7lZoz2sXL4+s1ihJbtIsz2kRqMp/08=[.highlight]
We can go a little further with our analysis and research here by searching for the [.highlight]assay.porchlightcommunity.org[.highlight] on URLScan.io. With our search, we can see a list of other potential websites that may be hosting the same website and file. Over 100 potential compromised domains were seen and further research could be done into the SocGholish update file.

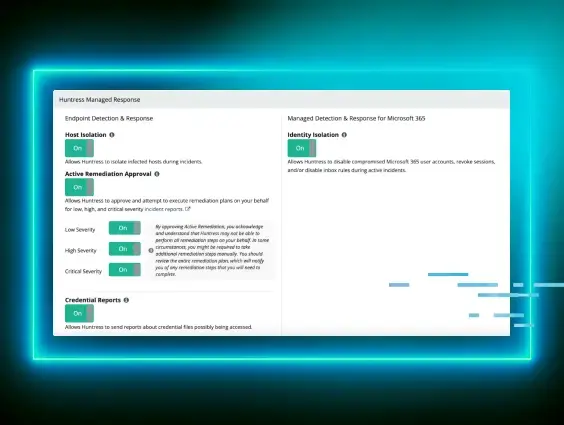
These discoveries are pivotal for our reporting process, enabling us to inform the customer with concrete evidence as seen in the report below.

Tool Suggestions and Acknowledgements
Special thanks to Tim Kasper (Senior Analyst US team Huntress) for finding me the time to write this between alerts and also helping craft it into this.
Special thanks to Jai Minton (Senior Analyst AUS team Huntress) for discovering the second stage and additional compromised domains with the URL Scans.
Special thanks to Mehtap Ozdemir (US team Huntress) for recommending the URL Revealer tool from Kahu Security. This tool, alongside running the suspicious [.highlight]Update.js[.highlight] file, can unveil the domains the file communicates with, offering a quick win in our investigative process.


Sign Up for Blog Updates
Subscribe today and you’ll be the first to know when new content hits the blog.







.svg)





.webp)