Before you pop the bubbly and count down to a new year, let’s reminisce for a moment. Looking back on the past 365 days, it was clear cybercriminals had no intention of slowing down. But neither did we. Our analysts worked tirelessly to help ensure our partners and our community could remain alert, informed, and protected. Here’s a snapshot of the milestones and lessons from 2024 that’ll guide us as we prepare for what lies ahead in 2025.
ConnectWise ScreenConnect Vulnerabilities
The year came in with a fury. In February, critical vulnerabilities in ScreenConnect emerged, allowing attackers to bypass authentication with ease. Our team responded swiftly with in-depth research, detection guidance, a hotfix, and detailed analyses to keep our community informed about post-exploitation tradecraft.
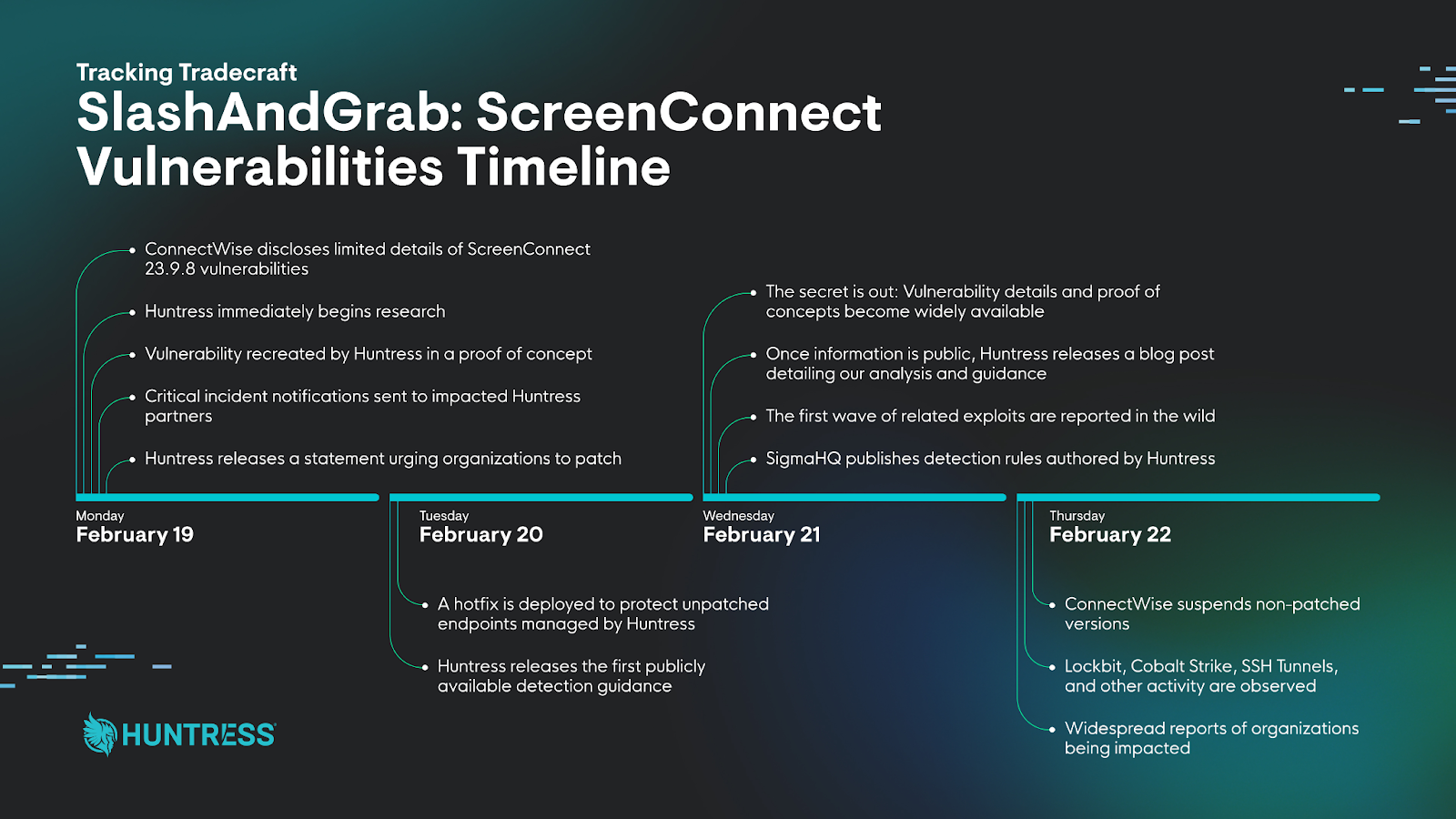
Revisit the blogs:
- Vulnerability Reproduced: Immediately Patch ScreenConnect 23.9.8
- Detection Guidance for ConnectWise CVE-2024-1709
- A Catastrophe For Control: Understanding the ScreenConnect Authentication Bypass (CVE-2024-1709 & CVE-2024-1708)
- Think Your ScreenConnect Server Is Hacked? Here’s What to Look For.
- SlashAndGrab ScreenConnect Post-Exploitation in the Wild (CVE-2024-1709 & CVE-2024-1708)
- SlashAndGrab: The ConnectWise ScreenConnect Vulnerability Explained
Revisit The Product Lab:
BlackCat Ransomware Affiliate
We also explored the tactics, techniques, and procedures of a ransomware affiliate operator who exploited a ScreenConnect vulnerability and attempted to compromise a healthcare endpoint.
Revisit the blog:
LightSpy Malware
In April, we analyzed a new variant of spyware targeting macOS devices. The detection rules we developed are available on GitHub.
Revisit the blog:
HTML Smuggling Tradecraft
May brought us a mass phishing campaign that bypassed MFA using advanced adversary-in-the-middle techniques.
Revisit Tradecraft Tuesday:
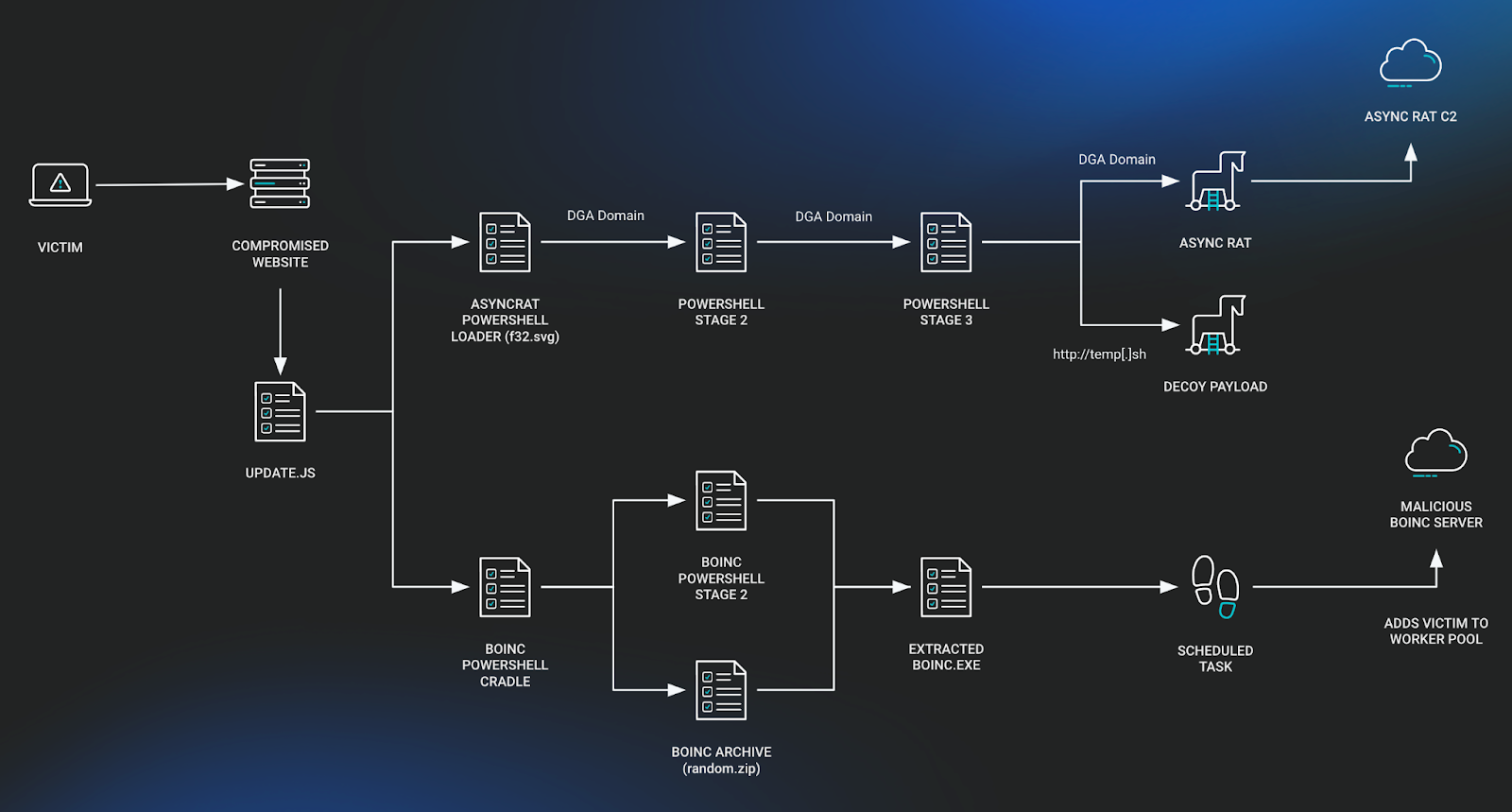
BOINC Software Exploited by SocGholish
July saw new behaviors from the malware SocGholish, including the use of the legitimate volunteer computing software BOINC. Through malicious installations, BOINC could be configured to connect to look-a-like servers to collect data, transfer files, and execute tasks, essentially operating as a C2.
Revisit the blog:
Threat Actors Targeting Human Rights Activists
August revealed that the highly resourceful (and truly heartless) APT, OceanLotus, had been targeting Vietnamese human rights defenders for over four years with sophisticated persistence methods.
Revisit the blog:
Revisit Tradecraft Tuesday:
Akira Ransomware Indicators
In September, we identified specific indicators associated with Akira ransomware infections. By detecting these indicators earlier in the attack chain, we could help organizations inhibit—or even obviate—file encryption malware deployment.
Revisit the blog:
FOUNDATION Software Breaches
September also brought us brute-force attacks on accounting software used by contractors, exposing the need for better credential hygiene across industries.
Revisit the blog:
SafePay Ransomware
October introduced a new ransomware variant with no prior reporting in the industry. By uncovering incidents where SafePay was deployed, we were able to provide analysis of the ransomware's behavior and detection opportunities.
Revisit the blog:

Cleo Software Exploitation
Closing out the year, we identified a critical threat involving Cleo’s LexiCom, VLTransfer, and Harmony software, commonly used to manage file transfers. Our team wrote extensively about this threat, and we offered a technical breakdown of a new family of malware we’ve named "Malichus."
Revisit the blogs:
- Threat Advisory: Oh No Cleo! Cleo Software Actively Being Exploited in the Wild
- Oh No Cleo! Malichus Implant Malware Analysis

A lot obviously went down in 2024, and while this was just our highlight reel, we’ve got plenty more to talk about. You can dive even deeper into what we saw by downloading our 2024 Cyber Threat Report.
As we head into 2025, we’re certain cybercriminals will continue to get craftier. But so will we. And through it all, we’ll be here with you, ready to take on whatever comes next.
Thanks for taking this stroll down memory lane with us. Now, let’s look ahead. Here’s to a new year of outsmarting the bad guys, together.