Huntress Blog
Welcome to the Huntress Cybersecurity Blog, your go-to spot for staying ahead of hackers and boosting your cybersecurity savviness. Our blog contributors have focused on making cybersecurity education engaging and accessible for everyone.



Exploitation of Windows Server Update Services Remote Code Execution Vulnerability (CVE-2025-59287)
Looking Through a Pinhole at a Qilin Ransomware Attack
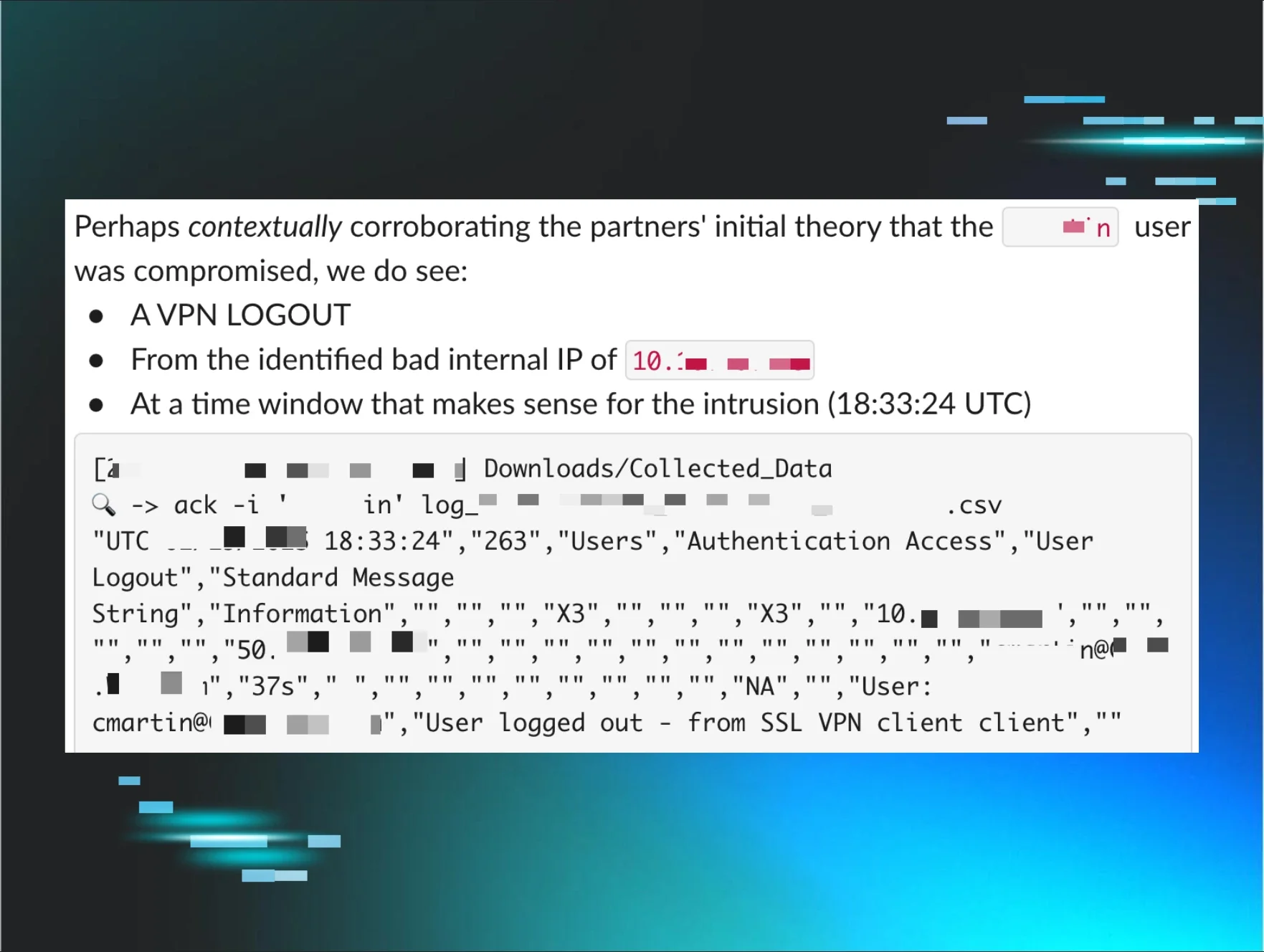
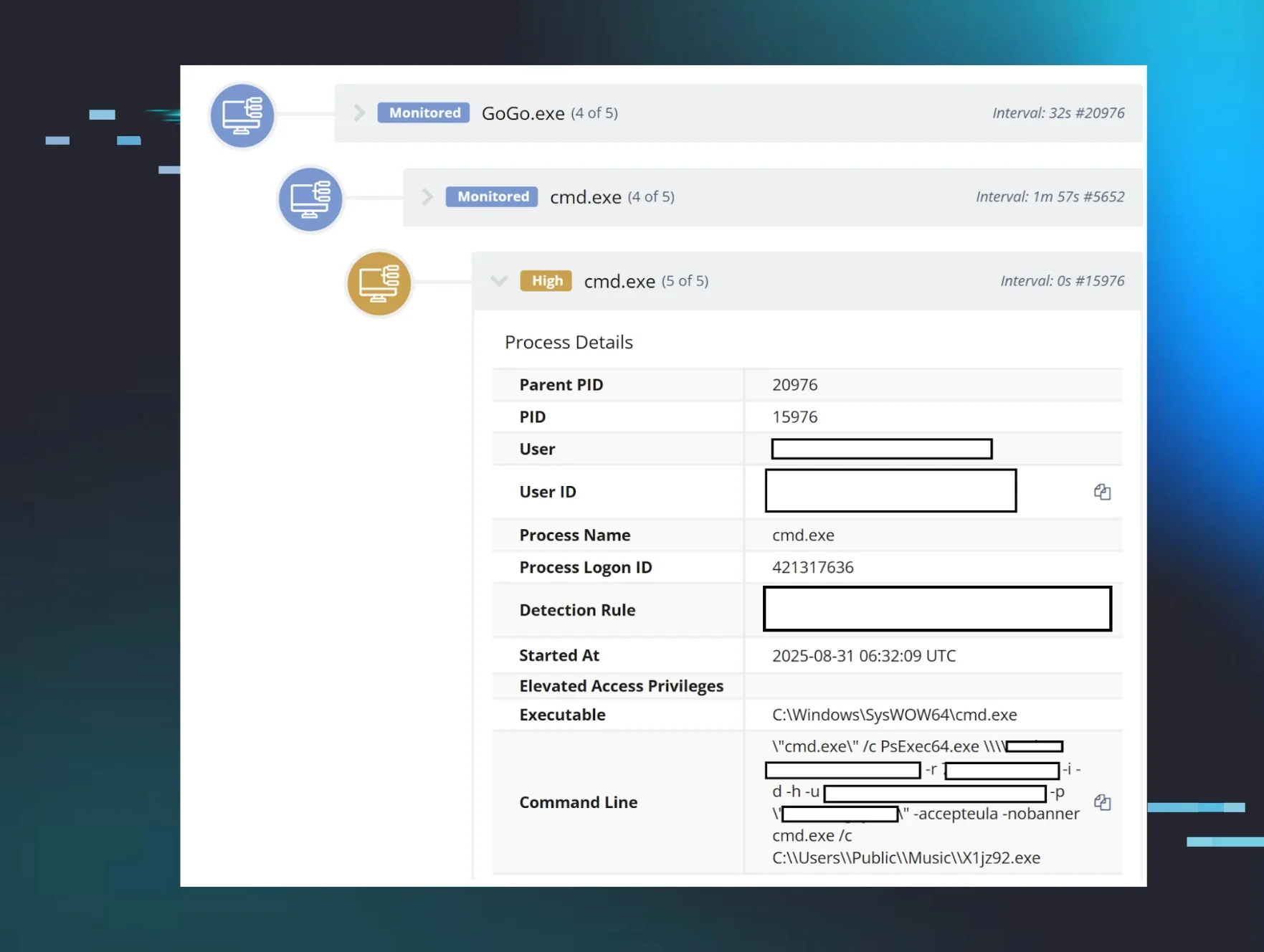
I Wish I Was a Little Bit Taller: Dealing with Imperfection in Intrusions
Dispelling Ransomware Deployment Myths
CMMC Final Rule: What DoD Subs Need to Know
Active Exploitation of Gladinet CentreStack and Triofox Local File Inclusion Flaw (CVE-2025-11371)
The Crown Prince, Nezha: A New Tool Favored by China-Nexus Threat Actors
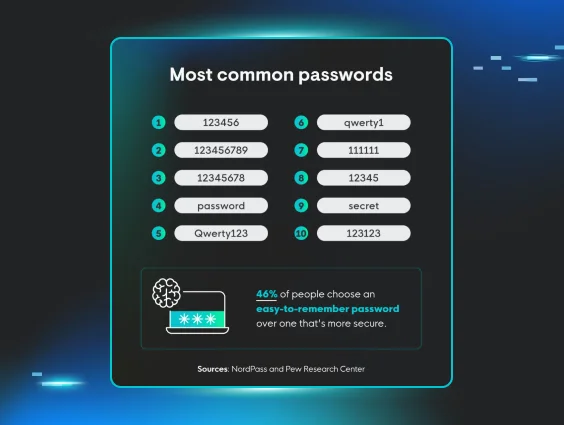
How to Offend Your IT Team: A Guide for the Security Unaware
Huntress Threat Advisory: Widespread SonicWall SSLVPN Compromise
The Lamest Cybersecurity Tips We’re Tired of Hearing (and What to Do Instead)
What Is a Security Awareness Training Program?
27 Biggest Data Breaches Globally (and Lessons Learned)
The Craftiest Trends, Scams, and Tradecraft of 2025 (So Far)
Let’s Be Offensive This Cybersecurity Awareness Month
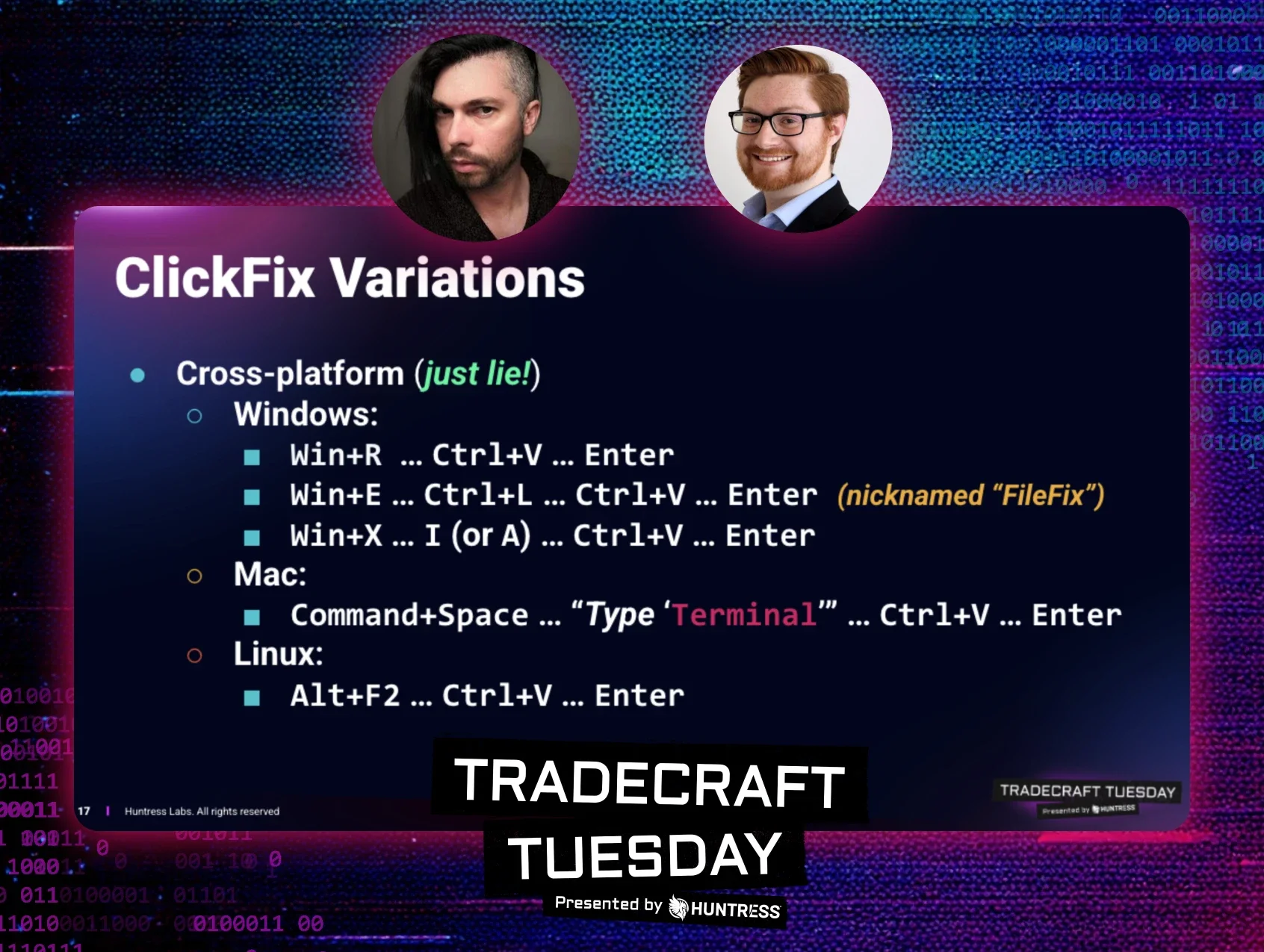
Don’t Sweat the *Fix Techniques

Sign Up for Huntress Updates
Get insider access to Huntress tradecraft, killer events, and the freshest blog updates.