







At Huntress, we like to wreck hackers. But to take them down, we first have to understand how they operate. That’s why we created the 2025 Cyber Threat Report—an in-depth exploration of the nasty tactics, trends, and techniques reshaping cybersecurity today.
Here, we highlight key findings from the past year, offering a snapshot of the malicious strategies our analysts uncovered. Whether you’re an IT professional, cybersecurity practitioner, or business owner, these insights can provide actionable guidance to help you stay one step ahead of ever-evolving cyber threats.
Throughout 2024, Huntress' threat analysts looked at data from thousands of organizations and millions of endpoints, revealing the key trends that show how adaptable and relentless today’s malicious hackers are.
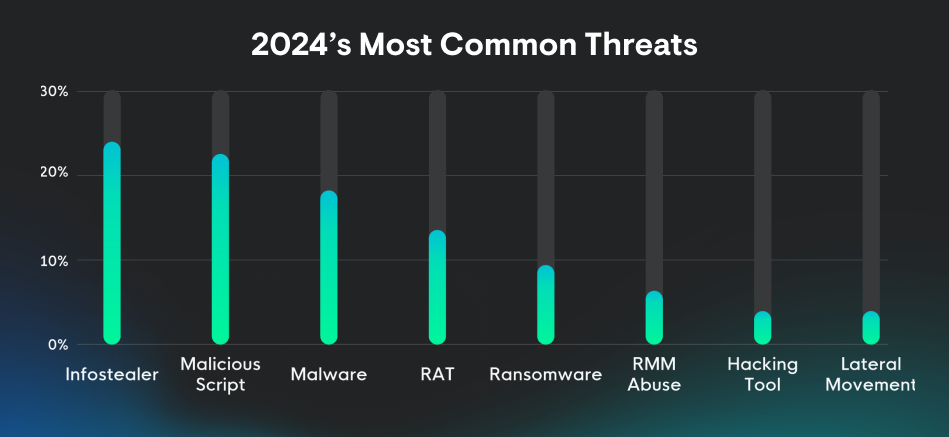
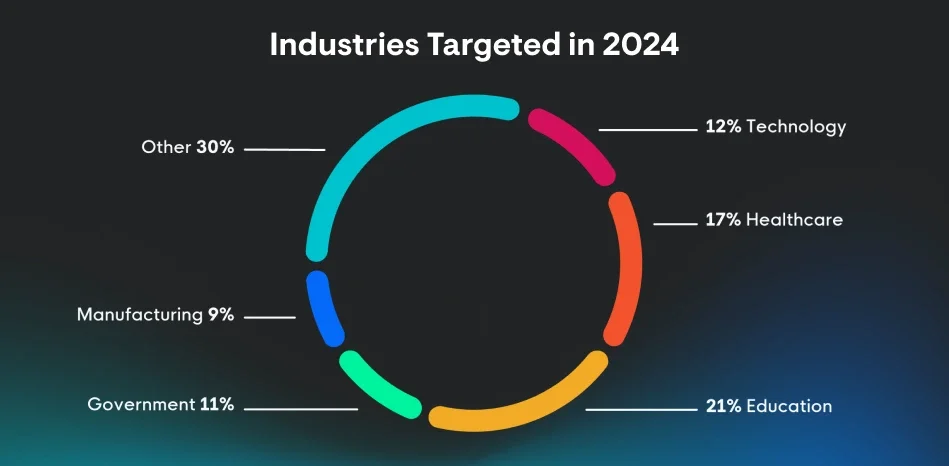
The findings from our 2025 Cyber Threat Report are grounded in real-world data with a comprehensive view of how malicious hackers operate today. Our threat analysts observed patterns across industries like healthcare, education, government, and manufacturing, and these growing trends stood out:
The 2024 cybersecurity landscape exposes a simple yet alarming truth: threat actors aren’t slowing down. Because hackers' tactics and tools are evolving, you must take a proactive approach that prioritizes awareness, preparation, and consistent upgrades to defense strategies.
Understanding the tactics outlined in this report is the first essential step. By educating your teams, using multiple layers of security, and staying informed about emerging risks, you and your organization will be ready to take on any challenges that come your way.

The insights from our 2025 Cyber Threat Report spotlight the critical need to stay ahead of malicious hackers. With tools like RMM software and phishing techniques becoming more advanced, protecting data, systems, and users is an ongoing battle—but one you can win.
While there’s no one-size-fits-all solution, embracing layered defenses, removing unnecessary vulnerabilities, and training your team to spot threats are actionable steps everyone should take right now.
Download the entire 2025 Cyber Threat Report to gain a deeper understanding of these trends and learn more strategies for keeping your organization safe.
Get insider access to Huntress tradecraft, killer events, and the freshest blog updates.
