







| LOLBin stands for "Living Off the Land Binaries," tools that are pre-installed as part of an operating system. LOLBins are not malicious in themselves but can be used maliciously by cyberattackers. |
|---|
To fly under the radar, cyberattackers need to stay one step ahead. One sneaky way hackers attempt to remain unnoticed? LOLBins, a tempting target for hackers to leverage.
LOLBins––otherwise known as “Living Off the Land Binaries”––are components native to an operating system, such as Windows or macOS. They can be leveraged and exploited by bad actors to gain additional access or permissions.
Discerning the difference between legitimate and malicious use of native utilities and exploiting these differences for detection opportunities allows cybersecurity platforms like Huntress to disrupt the threat actor’s activities much earlier in the attack chain.
Discover how LOLBins work, learn ways to identify native versus malicious LOLBins, and how to prevent future threats.

LOLBins are a significant threat to cybersecurity due to their inherent stealth and difficulty detecting malicious use. Since these tools are pre-installed and routinely used for legitimate purposes, security software may not flag their activity as suspicious.
This can allow attackers to operate undetected and execute malicious commands, such as:
The biggest challenge with detecting LOLBin attacks is that they mimic regular system operations. Below are some examples of regular operations and how a LOLBin attack may mimic them.
On Windows endpoints, there are a number of ways to create user accounts. User accounts can be created and managed via PowerShell, WMI, or the Local Users and Groups Manager, as illustrated in Figure 1.
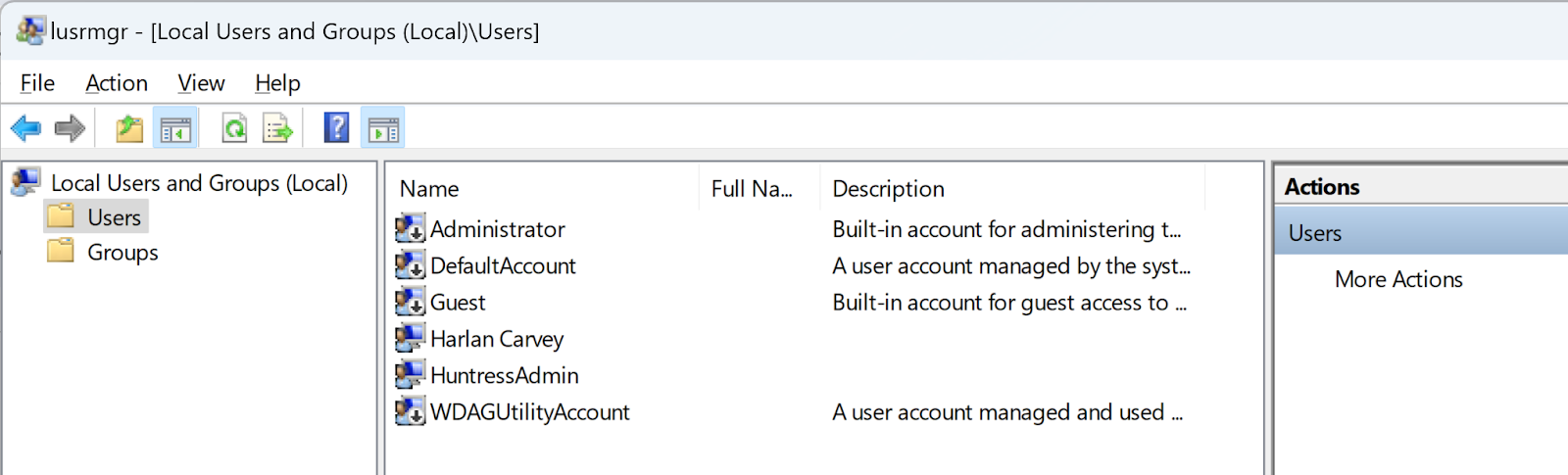
By clicking on “Users” in the Local Users and Groups Manager, and selecting “New User,” you’ll see the new user dialog illustrated in Figure 2.
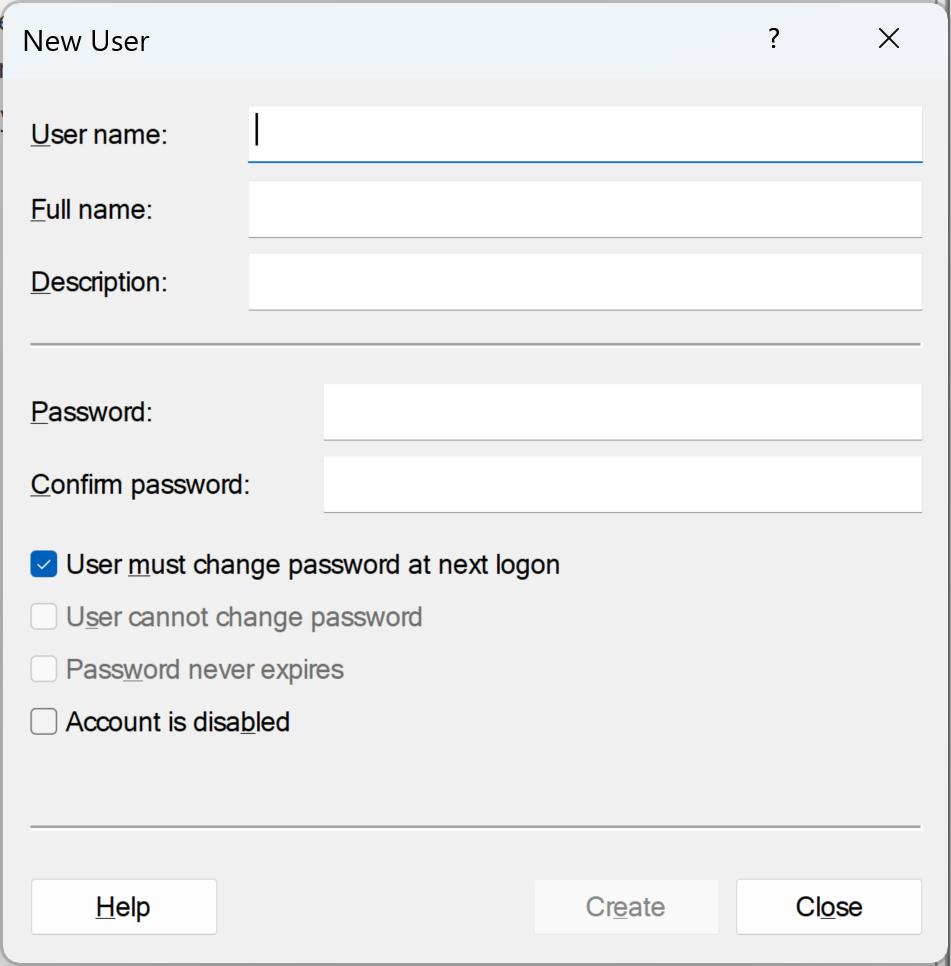
Completing the New User dialog form and clicking “Create” will create a new user account. In addition, there are a number of commercial products available that can be used within an organization to create and manage large groups of user accounts across an entire infrastructure.
Another means for creating user accounts involves the native utility, net.exe. Many administrators use this LOLBin to create, manage, and remove user accounts. Threat actors do so as well.
When it comes to cybersecurity and detecting the malicious use of native utilities such as net.exe to create user accounts within your organization, the first step is to:
If your organization does use net.exe to create user accounts, ask yourself these questions:
If so, any activity outside of those guardrails should be considered suspicious in nature and given a closer look.
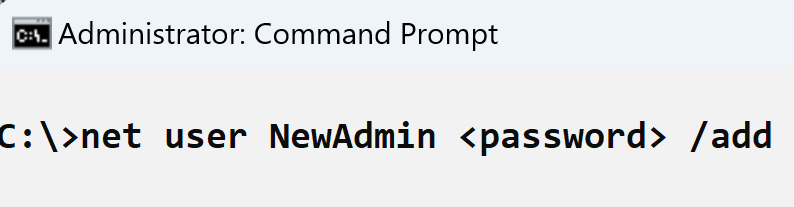
Another aspect regarding the use of native utilities is how those utilities are launched. One common means for doing so is for administrators to log into a system, open a command prompt, and type the command (illustrated in Figure 3), or run the command from a batch file.
In this case, the process lineage has cmd.exe as the process parent and Explorer.exe (the Windows Explorer shell) as the process grandparent.
Any observed command line where the process parent or grandparent is one of the following should be considered malicious:
Most organizations have standard username and password conventions that are used across the various interfaces. This can include conventions like using first initial and last name in emails or setting up passwords to follow particular requirements, like including a capital letter, number, and symbol.
If what you’re seeing in the suspicious activity differs from typical organizational conventions, then the activity is likely malicious.
For example, if your organization uses a naming convention for new user accounts that includes a reference to a department or team, or consists of the user’s first name and last name (together, or separated with a “.”), then any new user accounts created that don’t follow that convention should be considered malicious.
Yet another way aspect to help identify the malicious use of the net.exe LOLBin is the structure of the command line itself. Many times when net.exe is used legitimately, the structure of the command line appears as follows:
net user <username> <password> /addNote that the /add switch for creating a new user (not using the switch changes the password of the user account) falls at the end of the command line. However, it doesn’t have to; this is simply a convention that many administrators tend to follow.
Huntress analysts have observed the following command line being used to create user accounts on several instances against multiple customers:
net /add user WDAGUtilltyAccount Ujmqaz5055 /y
Note the subtle misspelling of the username, with the second “l” that should be an “i.” Huntress analysts also observed the following command line employed on a customer network:
net /add user ASP.NET Ujmqaz5055
Note that the use of this password by threat actors has also been observed by others and similarly reported.
Huntress analysts have also captured a number of usernames and passwords seen repeatedly used by threat actors over a considerable period. One example of a commonly used password is from the previous example:
Ujmqaz5055
Other observed examples include P@ssw0rd01!, Nullpass123, JapanNight!128, and Noface66Nocase!.
Examples of usernames commonly used by threat actors include:
A threat actor’s use of LOLBins doesn't mean it’s game over for the defender or the impacted organization. Using native utilities doesn’t have to mean that a threat actor’s activities blend in with legitimate activity.
In fact, with a little thought and just a bit of foresight, the threat actor’s use of those native utilities can instead be exploited as a detection opportunity, allowing defenders to disrupt the threat actor’s activities much earlier in the attack chain.
Understanding who uses those utilities, when, how they use them, and from which endpoints within the infrastructure presents a number of valuable opportunities to inhibit or even entirely avoid attacks.
Get enterprise-grade endpoint protection with Huntress’s Managed EDR today.
Fileless malware often relies on LOLBins. By leveraging legitimate system tools, fileless malware can execute malicious code without ever dropping a file to disk, making it difficult to detect and remove.
PowerShell is arguably the most commonly used LOLBin. Other common ones include CMD, rundll32, and regsvr32.
LOLBAS, or "Living Off The Land Binaries And Scripts," is a superset of LOLBins, encompassing a wider range of legitimate system components that attackers can leverage.
Get insider access to Huntress tradecraft, killer events, and the freshest blog updates.
