Huntress Resource Center
Welcome to your go-to destination for cybersecurity resources and education. Dig in and find a range of materials made to empower users of all levels with the knowledge and tools to defend against evolving cyber threats.



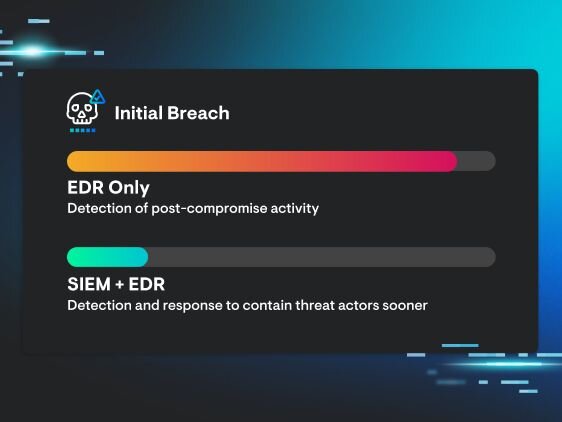
A One-Two Punch: EDR + SIEM for Faster, Smarter Threat Response (APAC)

A One-Two Punch: EDR + SIEM for Faster, Smarter Threat Response (NA)

10 things you must have in a Managed SIEM Solution

Hack the Hackers Back: Offensive Strategies for Cyber Defense

Community Fireside Chat: EMEA | Navigating Security Compliance in Europe
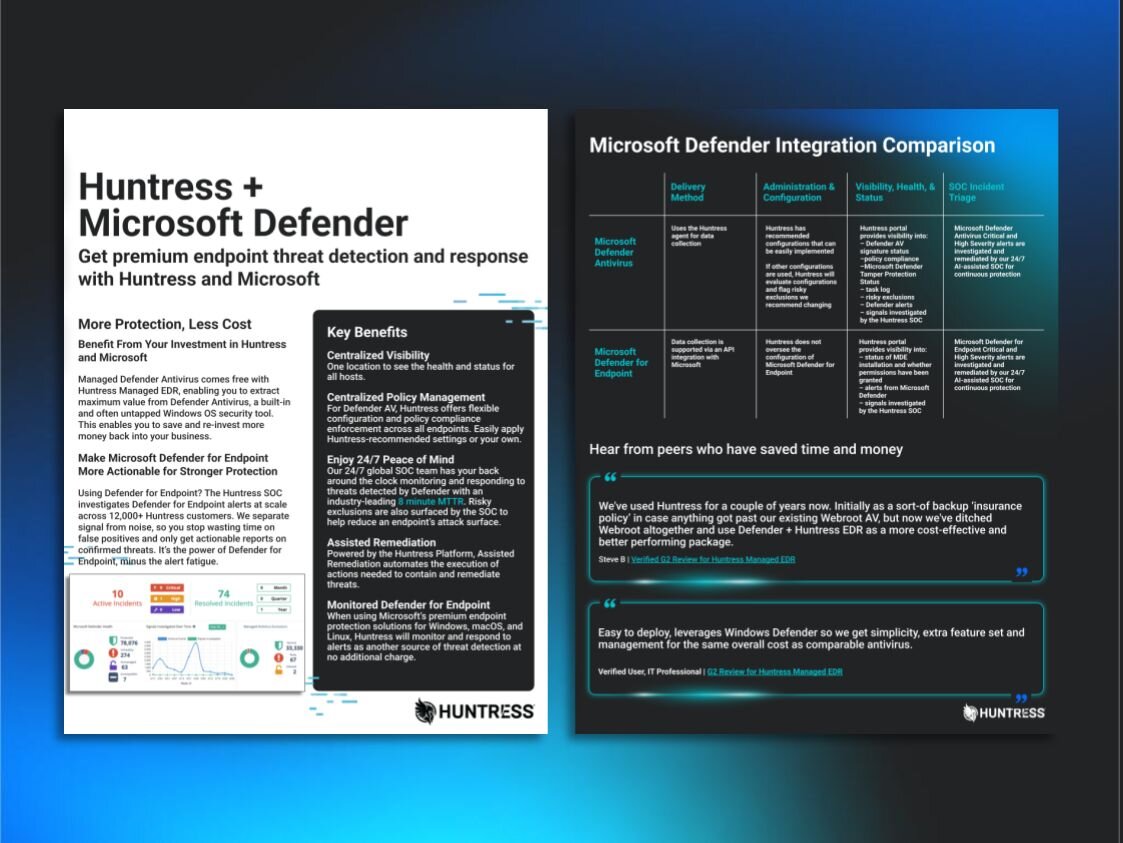
Huntress + Microsoft Defender Datasheet
Incident Response Tabletop-in-a-Box
SAT Checklist for IT & Security Professionals
SOC Incident Walkthrough: Bouncing Hackers Before They’re In Your Network

Microsoft + Huntress: A Look at the ROI

The MSP's Guide to Evaluating Security Vendors
True Cost of a Cyberattack
The True Value of People-Powered Cybersecurity

Huntress + Microsoft Defender



See Huntress in Action
Book a personalized demo to look at Huntress under the hood, explore the dashboard, and ask questions to our experts.