Managed SIEM Solution to Stay Ahead of Evolving Cyber Threats
Huntress puts enterprise-grade SIEM in reach for any team with our managed SIEM solutions. Compliance and threat response backed by our 24/7 AI-assisted SOC. No chaos, big budget, or headaches that come with traditional SIEMs.


What Users are Saying
The Huntress human-led SOC has an eye on your environment and logs 24/7 to detect, investigate and hunt. Making you secure and compliant.
Sleep easy and take control of compliance with powerful search, effortless reporting and long-term data retention up to seven years to meet the most demanding regulatory standards.
Ditch hidden fees and tuning headaches. Huntress SIEM delivers full visibility, 24/7 AI-assisted SOC support, and compliance reporting—all for one flat, transparent rate.
SIEM Solution Without the Noise. Only the Security That Matters.
We don’t believe in log hoarding—just smart, actionable and compliant data.
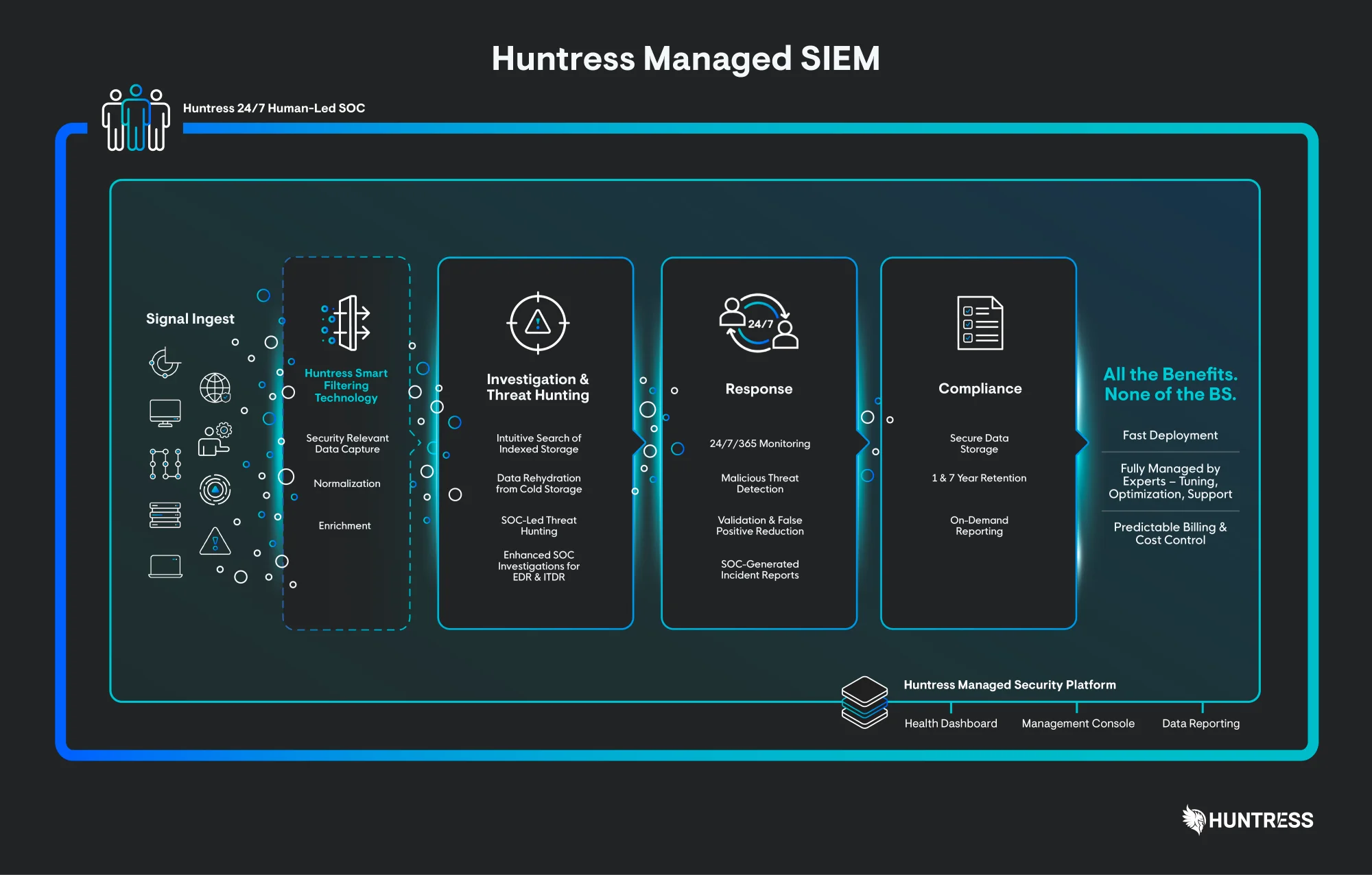
Huntress SIEM uses proprietary Smart Filtering to zero in on the signals that matter and ditch the data that only slows you down. You get sharper insights, faster response, and exactly what you need to stay compliant. No bloated storage bills. No wasted time. Just clean, focused security that works for you and your 24/7 Huntress SOC.

We handle the SIEM so you can do what matters most.
The Huntress SIEM is powered by our 24/7 AI-assisted SOC, so you can save time and resources. From relentless threat hunting and monitoring to the fine-tuning and configuration that keep things running smoothly. We do it all and you get the credit. As it should be.
Huntress Managed SIEM was designed to protect you by responding to threats earlier in the attack chain. Our team of SOC experts delivers detailed incident reports and can remediate confirmed threats for you.

The Huntress human-led SOC has eyes on your environment 24/7 to spot threats like known malicious attacker infrastructure and hunt for specific tradecraft like RDP brute force attacks.

Ingest relevant log data across endpoints, firewalls, VPNs, identity, password management, and other systems. All data is encrypted in transit and at rest and can be stored for up to seven years.

Huntress SOC experts actively monitor, triage, and investigate events for customers. We tune, write detections, and weed out false positives while responding on your behalf to confirmed threats.

Huntress Managed SIEM prices by data source with a pooled total data allocation so you avoid spikes in billing and get budget-friendly consistency.
If you’re like most, it’s hard to know which data from which sources is worth your attention. We tell you and use our proprietary Smart Filtering Engine to keep only the data that matters, tuning out the noise and keeping costs low.



The Biggest Mistakes First-Time SIEM Buyers Make
Don’t buy a Security Information and Event Management (SIEM) solution until you’ve read this guide. Choosing the right SIEM isn’t easy, and one wrong move can leave you with a noisy, overpriced system that doesn’t deliver what you need.

Protecting Businesses Like Yours


SIEM FAQs
Security information and event management (SIEM) is a security approach and platform that collects logs and security events from across your environment—endpoints, firewalls, VPNs, identity systems, cloud platforms, and more—and centralizes them so you can store, search, and analyze security‑relevant activity in one place.
SIEM was initially designed as a means to collect multiple disparate log sources and store the data under one centralized platform. Correlation rules took this one step further by adding a means to create alerts on the log data retrieved. Historically the use case for SIEM is built around: the collection/storage of logs, compliance, and threat visibility. The common problems with SIEM based on the “consume all data'' approach are cost, training/skill to deploy and manage, and lastly, defining useful data from the noise.
Huntress Managed SIEM makes powerful threat response and robust compliance support accessible to everyone without the big budget, big team, or big headaches that come with traditional SIEMs. Our Managed SIEM redefines the industry standard by applying Smart Filtering capabilities at the log source to capture only threat-specific logs. This simplifies the workload toward threat discovery and data retention. Managed SIEM is also built to collect Windows-based events and syslog using the same proprietary agent you’re familiar with. Our AWS backend supports your data and stores it safely and reliably.
The Huntress’ Smart Filtering engine, which analyzes log streams and keeps only security‑relevant events rather than hoarding every line, significantly reducing data volume and false positives while preserving the visibility needed for threat hunting and investigations. On top of this, a 24/7 human‑led SOC writes and tunes detections, monitors telemetry, triages suspicious activity and delivers clear, actionable incident reports, so you get true managed detection and response from SIEM rather than a raw log bucket you have to manage yourself.
Traditional firewalls and antivirus are simply not enough. The time to discover incidents is about six months. Finding and targeting attackers quickly is only possible with a full picture of log data as a whole. SIEM creates a bird's eye view of log data to quickly identify an attacker's tracks using correlation analysis and Smart Filtering.
Firewalls, antivirus and even EDR or MDR focus on specific control points and mainly see what is happening on endpoints or at the network edge, but many attacks show up first in logs that tools do not fully cover. A managed SIEM provides a unified view of these events across endpoints, identity systems, network devices and SaaS platforms so you can spot initial access, lateral movement and data exfiltration earlier and with more context than endpoint telemetry alone.
It also gives you centralized log retention and search capabilities that auditors, regulators and cyber insurers increasingly expect, allowing you to show that critical security events are recorded, searchable and correlated rather than siloed in individual products or overwritten after a short period.
The Huntress team designed and built Smart Filtering from the ground up. While most vendors depend on the source (firewall, endpoint, router) to apply its own filters, we directly filter the log data using our proprietary filtering engine, acting as a sieve to collect only critical information from log sources.
Smart Filtering reduces SIEM noise and storage requirements by keeping only the security‑relevant events from the logs you send into the platform and discarding routine or low‑value log lines that do not materially improve detection or investigations. After logs are ingested from Windows systems, syslog collectors or cloud and SaaS integrations, Huntress uses Smart Filtering to identify events that matter and stores only those, which allows you to avoid the “data hoarding” that plagues many legacy SIEMs and to benefit from long‑term retention without runaway costs.
While other vendors may offer some source‑side filtering or rule‑based suppression, Smart Filtering is built and maintained centrally by Huntress to work across multiple log sources and is a core reason why we can offer predictable per–data source pricing while still keeping alert volumes and false positives low.
Huntress Managed SIEM integrates with the IT and security tools organizations already use, providing centralized visibility across endpoints, network infrastructure, cloud platforms, identity systems, and third-party security controls.Instead of forcing a rip-and-replace, Huntress extends your existing environment by collecting Windows Event Logs from servers and workstations via the Huntress agent, which can also function as a syslog collector for firewalls and network devices. All logs are Smart-Filtered to retain only security-relevant events, securely stored in Huntress’ AWS backend, and made searchable for threat detection, investigations, and compliance reporting.
In addition to core log collection, Huntress Managed SIEM supports third-party EDR sources from platforms such as CrowdStrike Falcon, Cisco AMP / Secure Endpoint, and SentinelOne, along with identity and authentication integrations including Microsoft 365 and Entra ID (via Huntress Managed ITDR) and Duo. Cloud and infrastructure visibility includes AWS CloudTrail and AWS S3 bucket log collection, as well as DNS and network security platforms like Cisco Umbrella. MSPs and IT teams can also integrate operational tooling such as NinjaOne, with most integrations enabled directly through the Huntress portal using native connectors, APIs, syslog, or an HTTP event collector. Huntress continues to add new integrations over time while maintaining Smart Filtering to control noise, data volume, and costs as environments grow.
While the Huntress EDR agent is designed for rapid response-based actions at the endpoint, our Managed SIEM relays host Windows event and syslog data to our backend for further analysis and log storage. SIEM data is stored and hosted by the Huntress team for storage for one year by default or up to seven years for additional compliance support.
While Huntress Managed EDR and Managed SIEM are built to work together, they focus on different parts of the attack surface and the kill chain. In simple terms, EDR answers “what is happening on this machine right now,” whereas SIEM answers “what has been happening across the environment over time.” When both are managed by the same SOC, they reinforce each other by providing both deep host‑level visibility and broad environmental context.
No, Huntress Managed SIEM is intentionally built so that MSPs and IT teams do not need an in‑house SIEM engineer or a standalone SOC to benefit from it. The Huntress SOC handles the heavy lifting by designing and updating correlation rules, maintaining Smart Filtering for new log sources, monitoring telemetry around the clock, conducting investigations when something suspicious occurs and escalating only meaningful incidents with clear remediation guidance.
Your responsibilities are mainly to decide which customers and log sources to onboard, respond to the guidance the SOC provides—especially for changes on third‑party systems like firewalls and VPNs—and, when useful, run your own ad‑hoc or scheduled queries for customer‑specific reporting and internal investigations.
Yes. Huntress Managed SIEM is designed so MSPs can roll it out quickly and consistently across many clients without a complex project or specialized SIEM expertise. Deployment starts by installing or confirming the presence of the Huntress agent on the Windows servers and workstations you want to monitor; that same lightweight agent is then enabled to collect Windows Event Logs and, where needed, to act as a syslog collector for network devices.
From there, you turn on Windows Event Log collection for selected hosts in the Huntress portal, designate one or more systems as syslog collectors, and point supported firewalls and appliances at those collectors. You can then add cloud and SaaS integrations like Duo, DNSFilter, NinjaOne or SentinelOne through simple configuration in the portal, using native integrations or an HTTP event collector endpoint. MSPs typically start by enabling SIEM on their own environment and a small pilot group of customers, then use the same repeatable pattern and portal‑level configuration controls to scale SIEM across their broader client base in a controlled and predictable way.
Because Managed SIEM relies on Smart Filtering and SOC‑driven triage, you see far fewer raw alerts than you would with a traditional SIEM that ingests everything and forwards every rule hit directly to the customer. Smart Filtering strips out non‑security‑relevant noise at ingestion time, and the Huntress SOC further distills what remains by investigating suspicious events and only escalating incidents that reflect real risk, which significantly reduces false positives and alert fatigue.
When there is a real issue, you see it as an incident in the Huntress portal with a clear explanation of what happened, what data sources were involved, what the likely impact is and what actions have been taken or are recommended.


Solving the SIEM Problem
Don’t settle for a SIEM that doesn’t work for you. It’s time for a new approach.
Whether you’re grappling with excessive false positives, struggling to find the right expertise, or facing unpredictable costs, you’ll get the insights you need to make informed decisions about your security strategy.