







In classic martial arts movies, there’s always that one scene where the hero singlehandedly takes on a gang of oversized, overconfident goons. One by one, they come at him, and one by one, they hit the ground. Then, as all the bad guys are writhing in pain, a final challenger appears on screen—he’s small, quiet, and unassuming. Our hero smirks, preparing for another easy fight. And that’s when the real battle begins. But, as you might’ve guessed, that little guy has the deadliest skills—he’s fast, ferocious, and unforgiving. By the time our hero realizes he needs a new strategy, it’s too late. That little guy you never saw coming was in full control the entire time.
Adversary-in-the-Middle (AiTM) is that guy. While more infamous cyberattacks—think ransomware or phishing—are the big thugs we’re all fixated on, AiTM lurks just off camera, silently intercepting your data, redirecting traffic, and hijacking sessions without drawing much attention. It’s often underestimated, but when it finally strikes, the damage can be brutal.
In an AiTM attack, an adversary sneaks in between you and whatever you’re trying to connect with—be it a website, an app, or a service. They intercept the information flowing back and forth, all while staying completely under the radar.
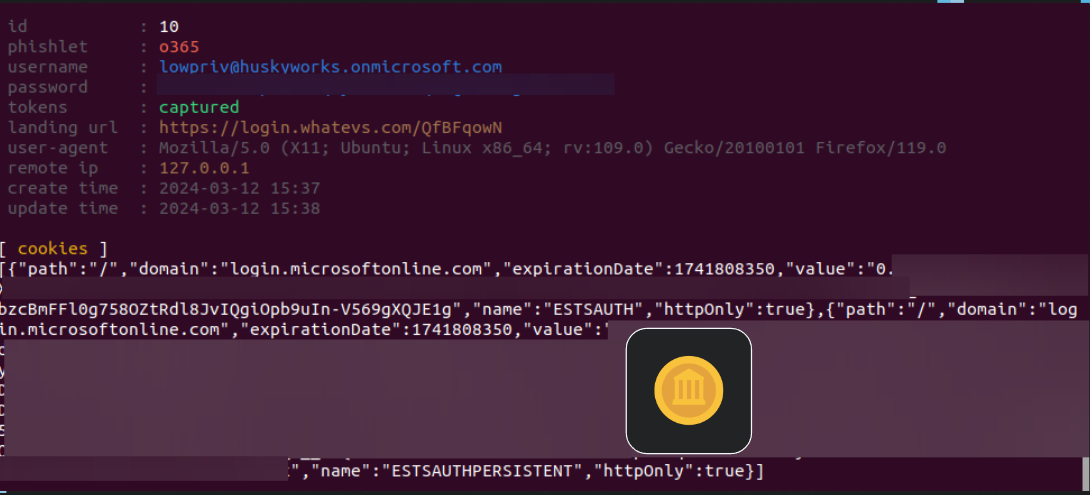
For instance, a common AiTM attack involves hijacking session tokens, those temporary identifiers that keep you logged into a site after you’ve entered your username and password. Once a threat actor steals your token, they’re no longer just monitoring you—they’ve become you. In other words, they’ve gained complete control over your session. And all the login credentials, financial transactions, and sensitive data that come with it.

Modern websites want to be easy to use. If they’re annoying to use, that’s bad for business. And bad for business means bad for the bottom line. But modern websites also need to authenticate their users and prevent unauthorized access. ”Easy to use” and “highly secure” are often diametrically opposed.
To meet both goals, websites use an authentication system based on sessions. You log in once with your username, password, and multi-factor authentication (MFA) code. In return, the site authenticates you and provides you with a token to store in your browser. This token is used in lieu of your username, password, and MFA code. For a time period after the first authentication, the token will allow you to access resources without inputting your credentials over and over.
(Psst! We did a Tradecraft Tuesday episode exploring how identity attacks work. Check it out.)
Here’s the problem: if that token falls into the wrong hands, it allows the user who found or stole it to authenticate themselves as the original user. A token is a whole set of credentials wrapped up into one package. So, while tokens are generated after multiple factors are used, the token itself is single-factor authentication.
Exploitation of this system is simple. Steal that token, and you become that user—no username, password, or MFA required.
Token theft tactics can be classified into two types: active and passive. Active token theft occurs when a hacker directly interacts with a victim to steal their token. In contrast, passive token theft involves obtaining tokens by scouring data breaches, credential dumps, or shady forums. Internally at Huntress, we refer to these methods as "pickpocketing" for active theft and "dumpster diving" for passive theft.
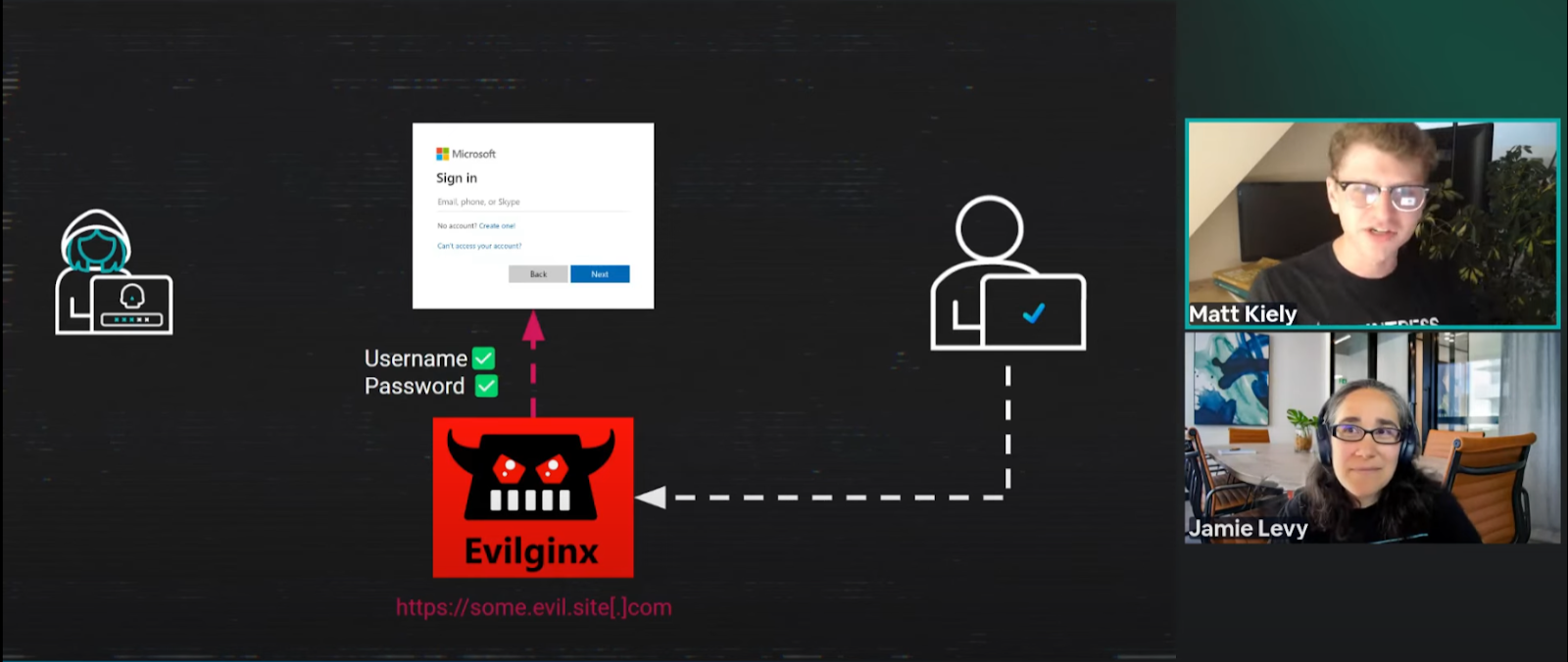
Active token theft includes AiTM attacks, where an attacker deceives a victim into authenticating through a transparent proxy that relays the authentication process to the legitimate Microsoft 365 service. Evilginx is the best-known AiTM toolkit, but many Phishing-as-a-Service (PhaaS) platforms, such as NakedPages and Evilproxy, carry out similar attacks daily against small and medium-sized businesses (SMBs).
Let’s do a little experiment. Take a look at Figures 3 and 4. The two images are screenshots of Microsoft 365 login pages. Can you tell which is an AiTM page and which is legitimate?

Sorry, it's a trick question: there isn’t enough information to tell because you can’t see the URL in either of those screenshots.
AiTM pages are generally indistinguishable from the legitimate website’s login page. This is because an AiTM site isn’t a clone or copy of the actual login page. When a victim clicks on a link and lands on an AiTM site page, they’re brought to an attacker-controlled proxy. The proxy brokers the login transaction between the victim and the legitimate login page. When the victim completes the authentication, the attacker can see their username, password, and session token in plain text. This means that the victim is seeing the real login page of the service, but their entire interaction is proxied through attacker-controlled infrastructure.
AiTM attacks aren’t universally effective against all types of MFA. There is such a thing as phishing-resistant MFA, which will prevent token reuse by binding a session to a physical device. However, the adoption rate for phishing-resistant MFA is low, especially in the SMB.
Awareness is critical for all other identities that use non-phishing-resistant MFA. Be politely suspicious of links, and if you think you’ve fallen victim to a token theft attack, inform someone who can invalidate your session and rotate your credentials immediately.
AiTM attacks are prevalent, but fear not because they’re also preventable. One of the best ways to protect yourself from AiTM attacks is through a layered security approach. Having protection tools like endpoint detection and response (EDR) and identity threat detection and response (ITDR) are incredibly helpful in catching these attacks after a threat actor has snuck in. But why let them get that far in the first place? You can also mitigate your risk before they gain initial access with a robust security awareness training (SAT) program.
Since the Huntress Security Operations Center (SOC) has seen so many AiTM attacks, it’s clearly an important topic. That’s why we’re making sure our partners and customers can train their end users to identify and prevent AiTM from happening in the first place. With that said, we’re happy to share the release of our newest Huntress Managed SAT episode: Adversary in the Middle.
In this episode, Bot-Head is scheming to attend Curriculaville Comic-Con with an epic Mech suit. But there’s one big problem—her wages from Major’s Fried Chicken just aren’t enough to cover that pricey costume. So, she plans an AiTM attack on Cannoli Bros. Construction to score stolen credentials and solicit money from their customers.
By following Bot-Head’s scheme, you and your learners will get to know more about AiTM tactics, how to spot them, and, most importantly, what to do when a real attack comes knocking.
The most dangerous threats aren’t the loudest or biggest. They’re the ones you didn’t even see coming. AiTM may not have the reputation of more notorious threats like ransomware or phishing, but their stealth is what makes them so scary. Adversaries quietly slide between you and another party, leaving you vulnerable before you even know something’s gone wrong.
But you don’t have to be vulnerable. Huntress has your back. We’re all about helping you stay one step ahead, and that means giving you the tools, knowledge, and insights to spot and stop these sneaky attacks before they get too close. We want this to be about more than just defense. It’s about helping you take the power back from the craftiest threat actors.
Get insider access to Huntress tradecraft, killer events, and the freshest blog updates.
