






On August 5, Huntress was made aware of the recently uncovered vulnerability tracked as CVE-2023-39143. For overall statistics, in our partner base we have over 1,000 vulnerable servers across 812 different companies. We have begun outreach efforts to all of our partners.
Our researchers are currently looking into the vulnerability so we can provide a deeper technical analysis and ideas for potential detection of exploits against the vulnerable versions. We will provide further updates to this blog and our Reddit post as we gather more information. In the meantime, here are some details to hopefully help you get started with patching and mitigation.
As of now, any Windows Papercut MF or NG server below version 22.1.3 is affected. Please follow the patch guidance from Papercut as soon as possible to mitigate this vulnerability. Note that this patch is only available for servers of version 22 and onwards—patches are not available for older versions of this software.
If you are unable to patch quickly, the next best mitigation is to ensure the server is not publicly accessible from the internet. This will not prevent lateral movement attacks from within your network, but it’s better than leaving your server completely open.
This vulnerability can also be mitigated by disabling the external device integration setting. To do this, go to Options -> Advanced -> External Hardware Integration and uncheck “Enable external hardware integration”. Please ensure you review your environment before making this system change as it could limit functionality of Papercut server where you have already integrated external hardware. The preferred mitigation here is to patch ASAP.
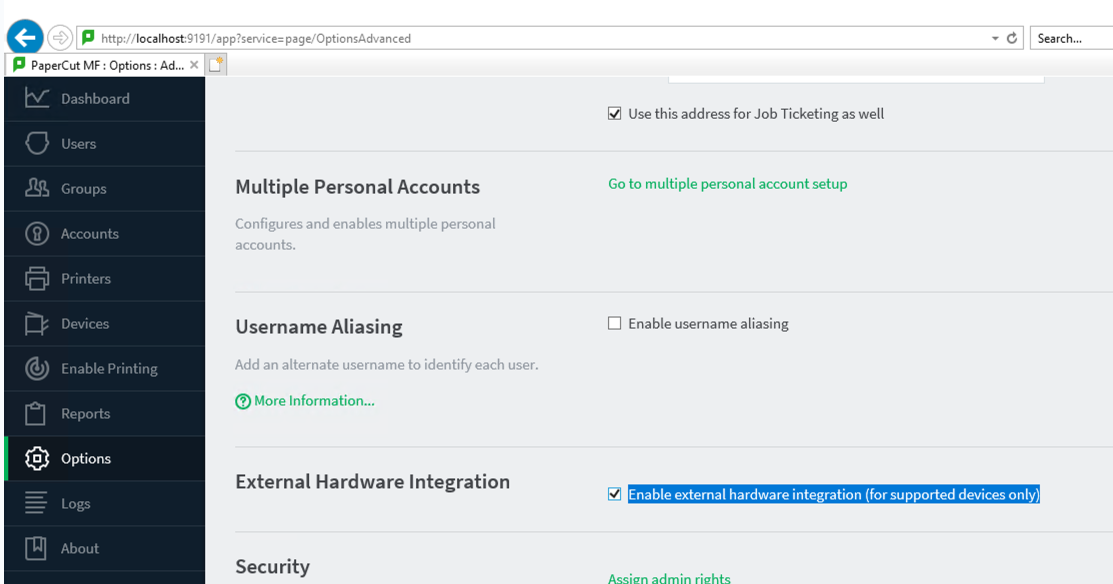
Patch as soon as you can if you have a vulnerable version (see above); otherwise apply some mitigations.
As always, if you’d like to have someone else watching your back while you work on patching and/or mitigation, feel free to spin up a free trial with us so our 24/7 SOC can keep an eye out for you.
Thanks to Huntress team members Caleb Stewart, John Hammond, Sharon Martin, David Carter, Adam Rice and Anthony Smith, amongst many others for their contributions to this writeup and rapid response effort.
Get insider access to Huntress tradecraft, killer events, and the freshest blog updates.
