







Welcome back to the second edition of Ask the Mac Guy. In our first post of this series, we discussed why you should protect your Macs. Now, we’re going to pivot to how you can best secure your Macs.
This will range from high-level, such as helpful tools you can use to protect your Macs, and even move to some of the lower-level, more technical facets of macOS that can be leveraged to keep you safe and secure.
These best practices won’t be specific to an end user or to an admin—the idea is that this can be consumable by anyone. Let's dive in!
It sounds simple—and in some ways, it is—but it is very common for users to not update their operating system. Apple continually pushes updates, whether security updates or general updates, to their endpoints that are designed to provide further protection to end users. These updates will include updates to Apple’s XProtect signatures and to its XProtect Remediator tool, both of which are designed to block and remediate malware.
There are many third-party tools that you can use to keep yourself safer. There are enough different options that occasionally decision fatigue can set in. So, to hopefully allow you to spend more time protecting your Mac device and not deciding how, here are a few of my favorite tools.

Now you may be thinking, "couldn’t I just use what Apple has built-in?" This is a completely understandable question. In my opinion, you need more. And although Apple makes it difficult to build security tools, especially when it comes to ease of installation, I don’t believe Macs are made to run strictly with the security solution Apple ships with its devices. I’ve written about this before; a great reference can be found in the first blog in the Ask the Mac Guy series.
This could be considered one of the more important parts of securing your machines. If a threat does get on the endpoint and is attempting to evade end-user detection, going back and auditing your systems on occasion can help prevent future intrusion. Everything I speak of below can be found within the user’s System Settings (formerly System Preferences) application.
In short, Filevault encrypts the information on your machine so only the user with the authorized password can access it. Within the System Settings, under Privacy & Security, there is an option to turn on FileVault. As it mentions, you will need to pick a password that you are confident you will remember, as if you forget that password (and the recovery key), you will lose all of the information on your hard drive. However, this is very valuable in keeping the information on your device safe.
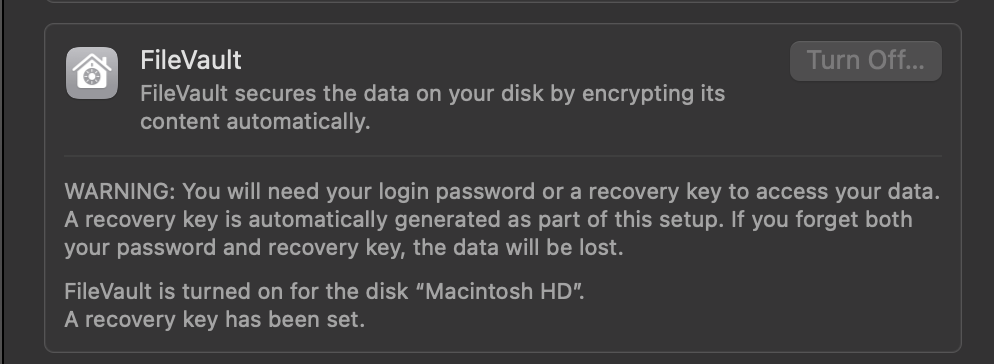
You can implement this at a business level, but even at an end-user level, I can’t recommend enough turning this functionality on.
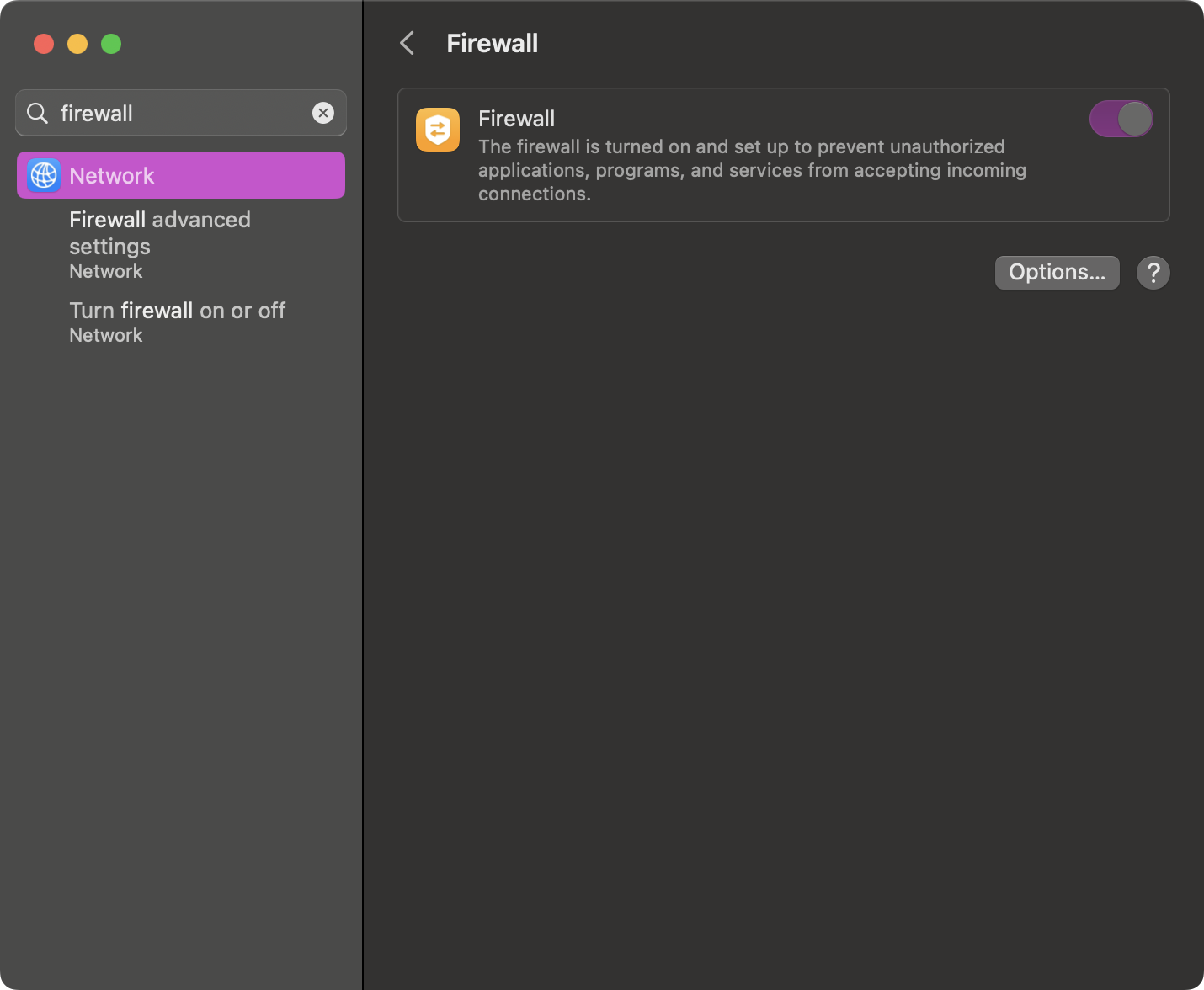
Apple has a built-in firewall that can be toggled on and off. A firewall protects your device from unauthorized incoming connections. There are also third-party firewalls, like LuLu or Guardian, that can extend this capability.
Transparency, Consent, and Control (TCC) is a database on your system that restricts an application’s access to different parts of your software and hardware that it hasn’t been given explicit permission to access. When I talk about auditing the permissions therein, I speak about looking at all of the different tabs in the Privacy & Security pane.
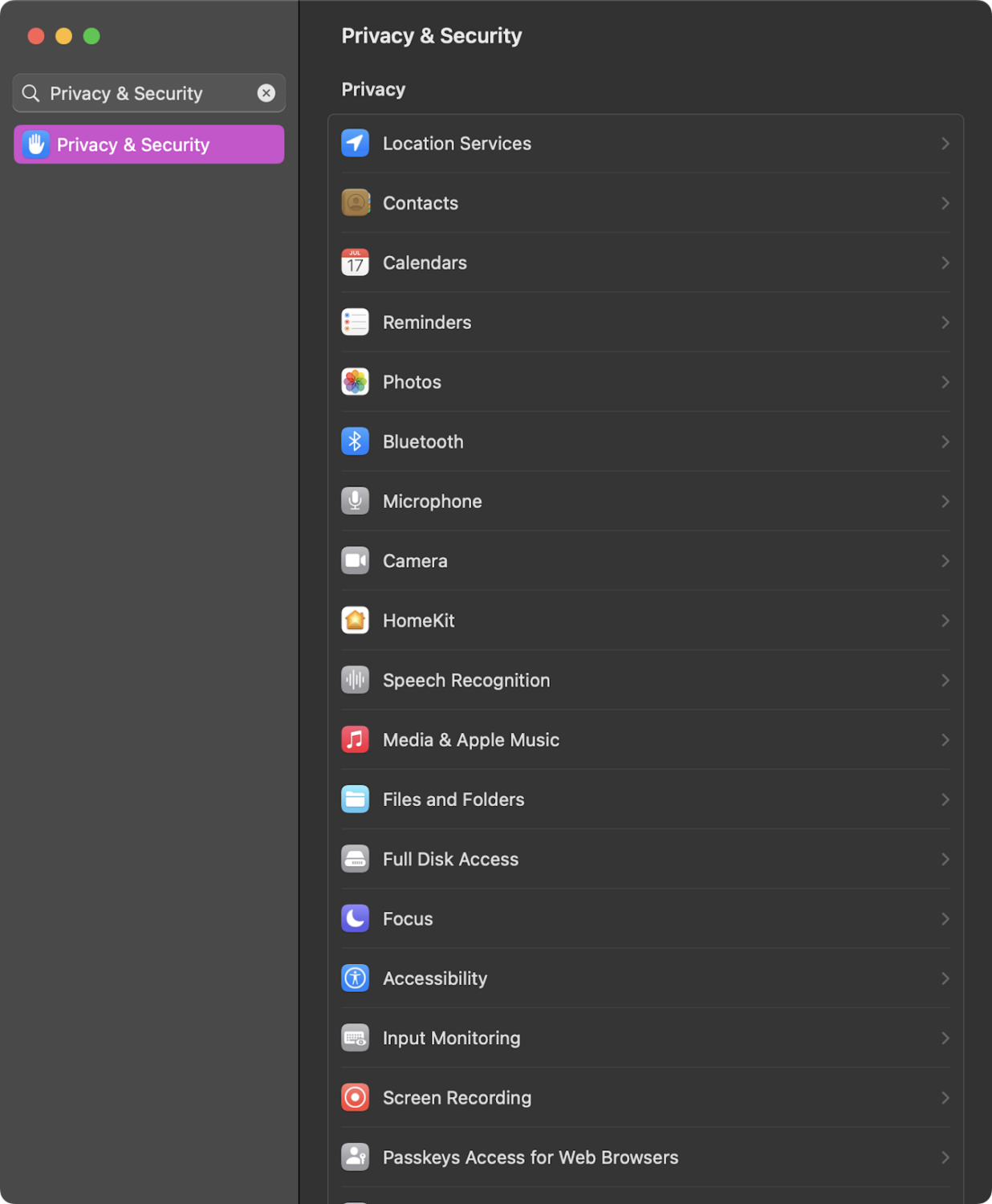
All of these contain sensitive information. If we were to look in Microphone or Camera, we would see applications that have the ability to turn our microphone or camera on and off. If you were looking through these and see an application that you are not familiar with, it may be best to remove said application’s access to the mic and camera.
As we navigate through these, especially Full Disk Access, we can see what applications have the ability to read and write to a directory that may contain sensitive information—such as Desktop, Documents, Downloads, Pictures, etc. Other tabs here include information about what applications have access to your location data, your Photos, and more. Going through each of these on occasion and making sure everything looks accurate can help reduce your risk.
Within the System Settings, if you navigate to the Sharing pane, you will see a list with things like Screen Sharing, Remote Login, Remote Management, and others.
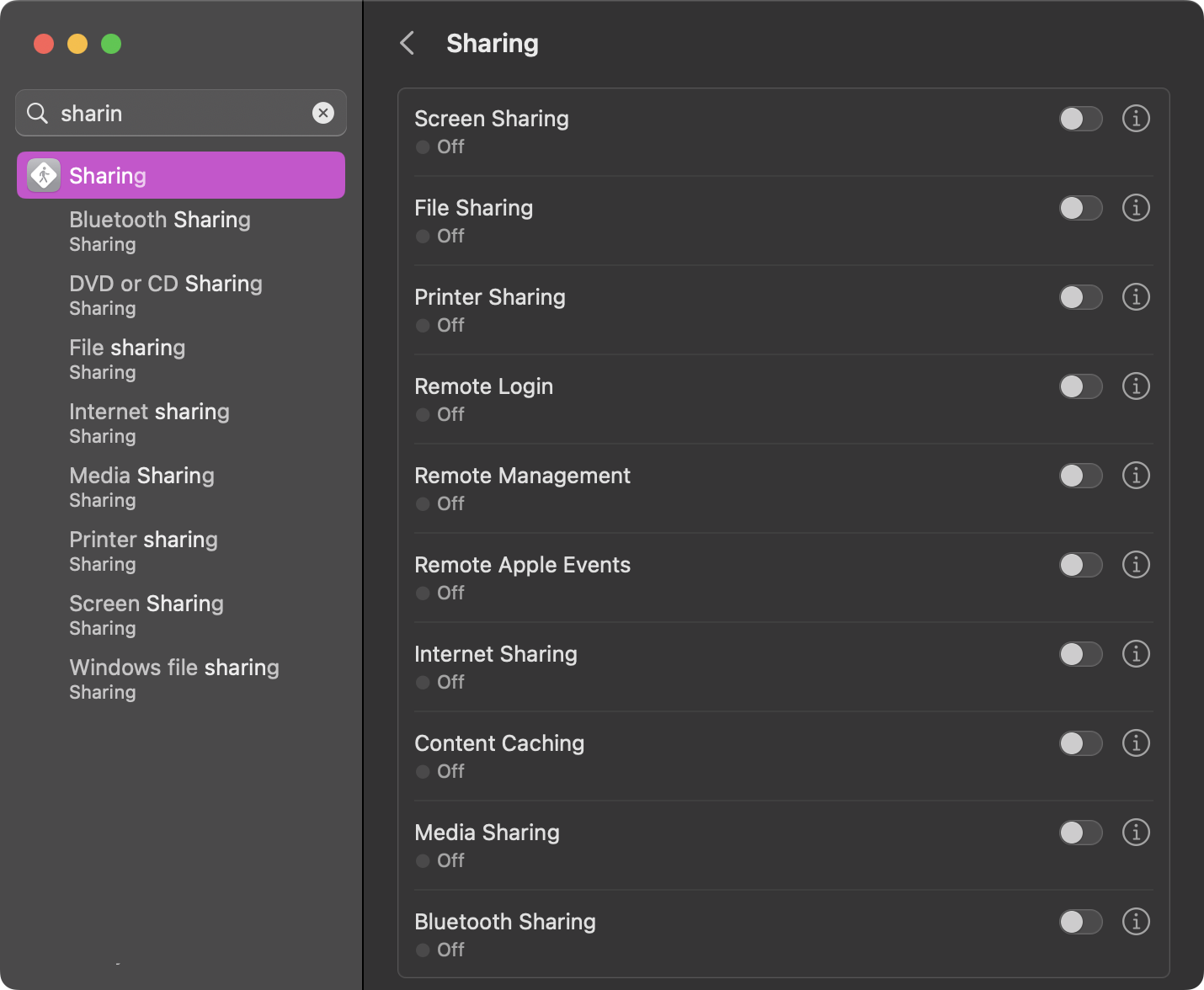
If something like Remote Login is toggled on, it may be worth digging into if it is a necessity or not. Remote Login can allow other users to remotely access your system via SSH or SFTP.
When an incident occurs and you discover that perhaps there is malware on a Mac endpoint, the best thing you can do first is try to gather more information. Tools such as Aftermath, which is free, can gather more information from the endpoint than when analyzed, and put relevant information into a spreadsheet to view.
This can allow you to see what websites were visited in browsers and what was subsequently downloaded, installed, and executed. This can be invaluable in learning more about what happened on the endpoint.
There are many ways to secure your Macs, and each way varies in your understanding of macOS security. If you start by keeping your operating system and applications up to date, you are already well ahead of the competition.
For those in the IT or security space who are trying to keep your Mac fleet secure, using some type of security awareness, such as Security Awareness Training from Huntress, can greatly improve the knowledge of your end users. This in and of itself can be a huge leg up in keeping your devices secure.
Stay tuned for more Mac tips from the Mac guy coming soon!
Get insider access to Huntress tradecraft, killer events, and the freshest blog updates.
