Network owners, operators and defenders find themselves in an increasingly contentious and hostile space, with entities ranging from opportunistic criminal elements to state-directed organizations engaging in various types of computer network intrusion. Through the seemingly endless sequence of blogs, alerts and hyperbolic media reporting, stakeholders may find it increasingly difficult to discern a strong “signal” from intense background “noise.”
In this blog, we will explore recent disclosures concerning an actor referred to as “Volt Typhoon,” assessed to be linked by multiple sources to the People’s Republic of China (PRC). Through this discussion, we will examine how such strategic network intrusion activity can impact and inform organizations that may believe themselves outside the scope or focus of such targeting. We will then conclude with recommendations for asset owners and operators of all types in the face of an increasingly contested and threatening networking environment.
Background
On May 24, 2023, Microsoft and a collection of Western intelligence and security agencies published findings on an actor labeled Volt Typhoon. This PRC-linked threat actor engaged in widespread exploitation of external-facing services and network appliances since 2021. Observed activity to date indicates this activity is likely limited to initial access development and information-gathering activity in victim environments. However, prominent US officials indicated in public comments that the identified intrusions are potentially preparatory work for future disruptive events against various critical infrastructure targets that would be of interest in future conflict scenarios in East Asia.
Based on reporting from the above entities as well as Secureworks, Volt Typhoon operations focus on exploiting or accessing external-facing services and appliances for initial access. Observed applications and services include:
- Zoho ManageEngine ADSelfService Plus (CVE-2021-40539)
- Paessler PRTG monitoring software
- Fortinet FortiGuard devices
Some of these items, such as ManageEngine, have previously been leveraged by various entities, while the specifics surrounding the other examples remain unavailable at this time. Irrespective of details, Volt Typhoon focuses on leveraging application- or server-side exploitation as an initial access mechanism into victim environments.
Following access, post-exploitation command and control (C2) activity from Volt Typhoon uses proxied traffic through legitimate, compromised assets to obfuscate the intruder’s origins. Specifically, Volt Typhoon appears to leverage vulnerabilities in a variety of small office, home office (SOHO) networking and security appliances to compromise equipment, then use these devices for relay points to control infected endpoints. Identified items in public reporting include, but are not necessarily limited to, equipment from ASUS, Cisco, D-Link, Netgear, and Zyxel.
Widespread exploitation of SOHO and similar equipment for infrastructure creation is nothing new. Examples range from criminal botnet activity such as the many variants of Mirai, to more concerning state-sponsored campaigns such as VPNFilter and CyclopsBlink. In each of these cases, the compromises are less about the networks directly impacted than marshaling infected nodes for C2 proxy services or executing follow-on attacks, such as distributed denial of service (DDoS) actions.
We thus observe parallel operations to achieve (still unknown) adversary objectives: compromising various third-party entities to create a C2 layer that enables the “core” compromise activity against targeted networks. As shown at a high level in Figure 1, such actions are complex endeavors but allow for an adversary to operate in a stealthy, difficult-to-detect manner.
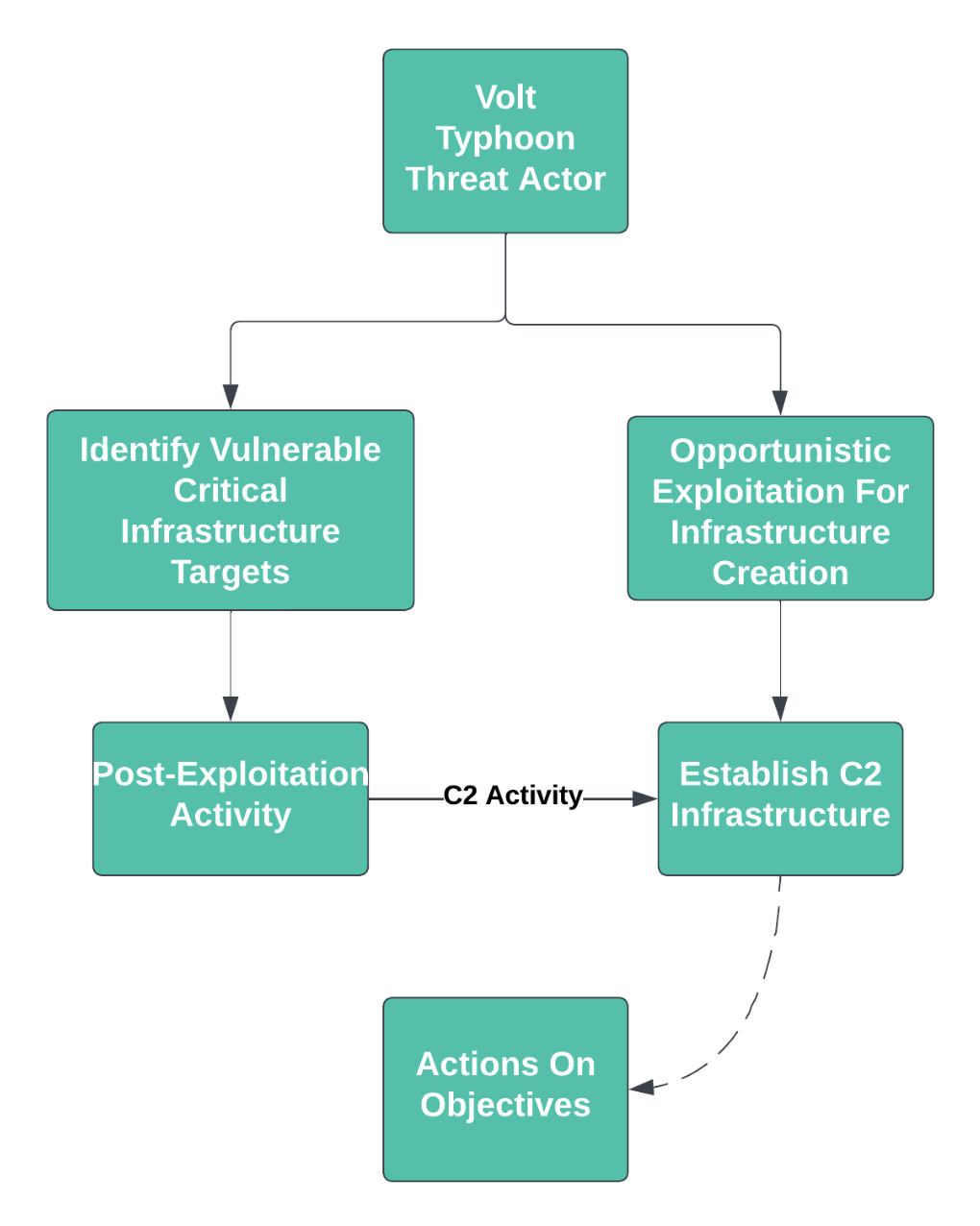
Figure 1: Simplified Volt Typhoon Attack Chain
Post-exploitation activity via the tunneled C2 includes a variety of techniques while eschewing the use of “malware” in the traditional sense. Among other items used, Volt Typhon leverages:
- Built-in operating system and administrator commands for the impacted device
- Third-party administrator tools and scripts, including remote management and maintenance (RMM) applications and archive tools such as 7zip and WinRAR
- Publicly-available offensive tooling, such as Impacket
Volt Typhoon uses the above tools and techniques for lateral movement, credential harvesting and system information gathering. Importantly, this activity mirrors a wider evolution in “threat space” of migrating towards a combination of “living off the land” binaries (LOLBins) and publicly-available tools. In avoiding custom tools and malware, adversaries can both more effectively “blend in” with legitimate network administrator activity and avoid easy classification and identification by analysts and defenders. The lack of compiled tools or similar malware objects largely negates the use of anti-malware solutions, while the extensive use of legitimate applications allows adversaries to hide in more general network “noise.”
Assessing The Threat
Volt Typhoon represents an interesting—although, as indicated in references above, not necessarily unique—threat actor, given the intrusion emphasis on platforms with little security or monitoring (network appliances and devices) and post-access behaviors that circumvent many defensive mechanisms. The specific nature of the threat remains cloudy at this time, though. While US officials have cautioned this campaign represents the initial steps in a long-term effort to prepare for attacks on critical infrastructure, identified tooling and actions so far indicate no activity or capability beyond widespread access development and information gathering.
For organizations operating in the critical infrastructure space, the scope and scale of activity mean Volt Typhoon must be taken seriously, if only out of caution. Organizations in these verticals, such as communications and electric utilities, should employ whatever means possible to evict these actors from compromised networks, and follow relevant best practices to prevent similar intrusions from taking place in the future.
But what of organizations outside of critical national infrastructure? From the perspective of the average small- or medium-sized business, exotic threats such as Volt Typhoon may seem to be distractions from more immediate security needs: countering business email compromise, preventing ransomware, or evicting illicit cryptominer operations. While reporting from CISA, Microsoft and others appear concerning, organizations with limited security resources and significant additional challenges can, and should, question the relevance of this and similar reporting, especially after being hyped by more traditional media sources as a harbinger of upcoming “cyber warfare.”
Yet, organizations cannot simply cast campaigns such as that executed by Volt Typhoon aside so easily, for irrespective of purpose and intention, the behaviors and tendencies observed in this intrusion mirror larger trends. As noted previously, exploitation of external facing services (whether for initial access or to build adversary-controlled infrastructure in legitimate system space), LOLBin abuse and avoidance of custom tooling are trendlines that extend from scary state-sponsored entities with fancy names to various criminal enterprises to current red teamers and penetration testers. Thus, observers outside of critical national infrastructure should look at the example afforded by activity such as Volt Typhoon, even if this entity itself is not the most pressing concern for the organization.
Additionally, a direct concern manifests where organizations are targeted as an adversary’s “means to an end,” while the organization itself is of no consequence to the intruder. In this case, we refer to the infrastructure “harvesting” activity executed by Volt Typhoon (as well as others, such as VPNFilter or CyclopsBlink). Here, the only value an organization has to the adversary is the combination of being vulnerable, accessible and online. In these situations, any organization, from a public school to a small machine shop, is a potential victim—and a potential unwitting accomplice in larger-scale cyber operations.
Although the threat might be different than that faced by critical infrastructure organizations, it remains very real and has implications for the victimized entity. Simply dismissing campaigns such as Volt Typhoon as irrelevant thus sets an organization up for failure—particularly given that some of the most powerful defensive strategies for “inadvertent” or “opportunistic” victims are also some of the easiest to implement.
Perimeter Security and Hardening
First and foremost: organizations must harden and secure external-facing devices and services. This advice applies whether the organization is a multinational enterprise environment or a single-location small office network. In the case of the latter, reasonable attack surface identification and hardening should be easier due to a significantly lower volume in services and users, although such action admittedly remains a challenge.
Irrespective of hardening difficulty, network defenders witnessed a return to server (or appliance) side exploitation in the past five years as multiple threat actors focused initial access activity on external-facing devices and services. From catastrophic vulnerabilities in load balancing gear to compromised VPN concentrators, adversaries learned what items are accessible externally and can be leveraged for follow-on access to internal networks. As a result, defenders need to shift their understanding of initial access vectors from phishing and other user-focused activity to the infrastructure underpinning an organization’s web presence or remote access capability.
Unfortunately, monitoring and visibility options for such devices—whether proprietary systems or Linux-based equipment—remain limited in scope and seldom accessible to most organizations with restricted security spend. Visibility is certainly ideal, and at minimum, exploring options to offload application and system logs to central logging structures can be a significant step in identifying (or, post intrusion, analyzing) a breach. Additional mechanisms such as netflow analysis and communication tracking can add further visibility by identifying anomalous connections and traffic flows. Short of this, however, organizations should emphasize patching and hardening such equipment wherever and whenever possible. Resources such as CISA’s Known Exploited Vulnerabilities catalog and similar, free and publicly available information sources can help direct and focus these efforts by identifying and prioritizing those issues already weaponized by intruders.
For most organizations, they or their service providers will need to “own” the issue of hardening and maintaining a secure network perimeter. While other intrusion routes obviously exist, opportunistic, widespread exploitation of server- or appliance-side vulnerabilities now represents one of the primary mechanisms for adversaries to enter victim networks. Identifying critical vulnerabilities and quickly patching them is one of the best and most reliable routes to closing off such infection vectors to adversaries, which requires actively monitoring vendor communication channels and having the IT resources necessary to rapidly apply fixes. Sound configuration management, infrastructure redundancy and other actions can place an organization in a good place, such that patching a single point of failure does not risk the entire organization’s functionality or online presence.
Defensive Lessons Learned
Based on Volt Typhoon’s activity and multiple other adversary operations, organizations—even those who may not be in the crosshairs of state-sponsored hacking operations—must adopt a robust, layered defensive posture. Single controls and solutions, such as anti-malware, will simply not suffice in an environment where adversaries regularly and successfully subvert legitimate system functions for malicious purposes. In this contested, hostile environment, organizations instead need to adopt an approach of defensive controls and countermeasures throughout the stack, as shown in Figure 2.

Figure 2: Simplified Network Intrusion Path
Historically, solutions like antivirus or anti-malware may have sufficed to defeat most infections. But as adversaries increasingly migrate toward the abuse of legitimate system functions and administrative tools, greater visibility and analysis of activity is required to differentiate legitimate administration activity from likely intrusion behavior. While much ink has been spilled decrying the failure of endpoint detection and response (EDR) in capturing these intrusions, the fundamental point is that EDR or EDR-like visibility is necessary to at least capture the signals and signifiers associated with intrusion operations.
For many organizations, especially those near the “bottom” of the security maturity stack, automated correlation and comparison of such signals is likely to remain a pain point for the foreseeable future. However, the capture of such signals for analysis and evaluation—even if post-incident—is a powerful mechanism for scoping an intrusion scenario and guiding subsequent incident response actions.
Essentially, organizations must prioritize visibility in their environments to provide sufficient signal and context to allow subsequent investigation to identify malicious activity. Investing in EDR or EDR-like capability, while not an item that will prevent intrusions (whether state-directed or otherwise), at least will allow network owners, administrators and defenders to understand how adversaries have abused functionality for malicious purposes. Subsequent eviction and mitigation strategies will be highly dependent on the nature of the organization and its tolerance for disruption, but the central idea holds: Absent visibility into adversary actions, network owners are operating at the will of potential intruders who wish to either compromise or subvert the network in question.
Final Thoughts
Network intrusions are increasingly commonplace, but our response to such activity need not be passive. Through an increasing emphasis on the visibility of network and host actions, and the correlation of observations within these views, network defenders and managers can identify instances where intruders mean to do them harm. As adversaries migrate from bespoke malware to leveraging common tools and administrative techniques for malicious purposes, the job of defenders will get more difficult—but with adequate visibility and understanding, it will not be impossible.
Defenders must continually strive to understand adversary operations and tendencies, and use this understanding to effectively vector and orient defense in the most suitable fashion. By understanding how adversaries such as Volt Typhoon operate, even if this specific adversary is not of direct interest, defenders can appropriately prepare their networks and ensure such activity is at least monitored, if not immediately alerted on. As adversaries continually evolve and shape their behaviors to evade simple defensive mechanisms, vendors and defenders must continually adapt and shape their efforts to counteract such evolution.
Interested in diving into more hacker tradecraft? Join us for Tradecraft Tuesday, our monthly webinar where our experts discuss the latest exploits, hacks, and attacks.

















