When I first joined Huntress, what drew me to this company was not just the people and their passion for their work; I was enamored by the unique technical approach to threat hunting. Looking for persistence was a new and different technique that I had never seen before. As an engineer, it was hard to look away from the elegance of this solution.
Little did I know that persistence hunting was just the tip of the iceberg to a much larger security vision. Persistence was never going to be the only thing. It was simply laying the groundwork for a much bigger plan.
As I got to know our founders and the company better, a core problem statement started to become clear:
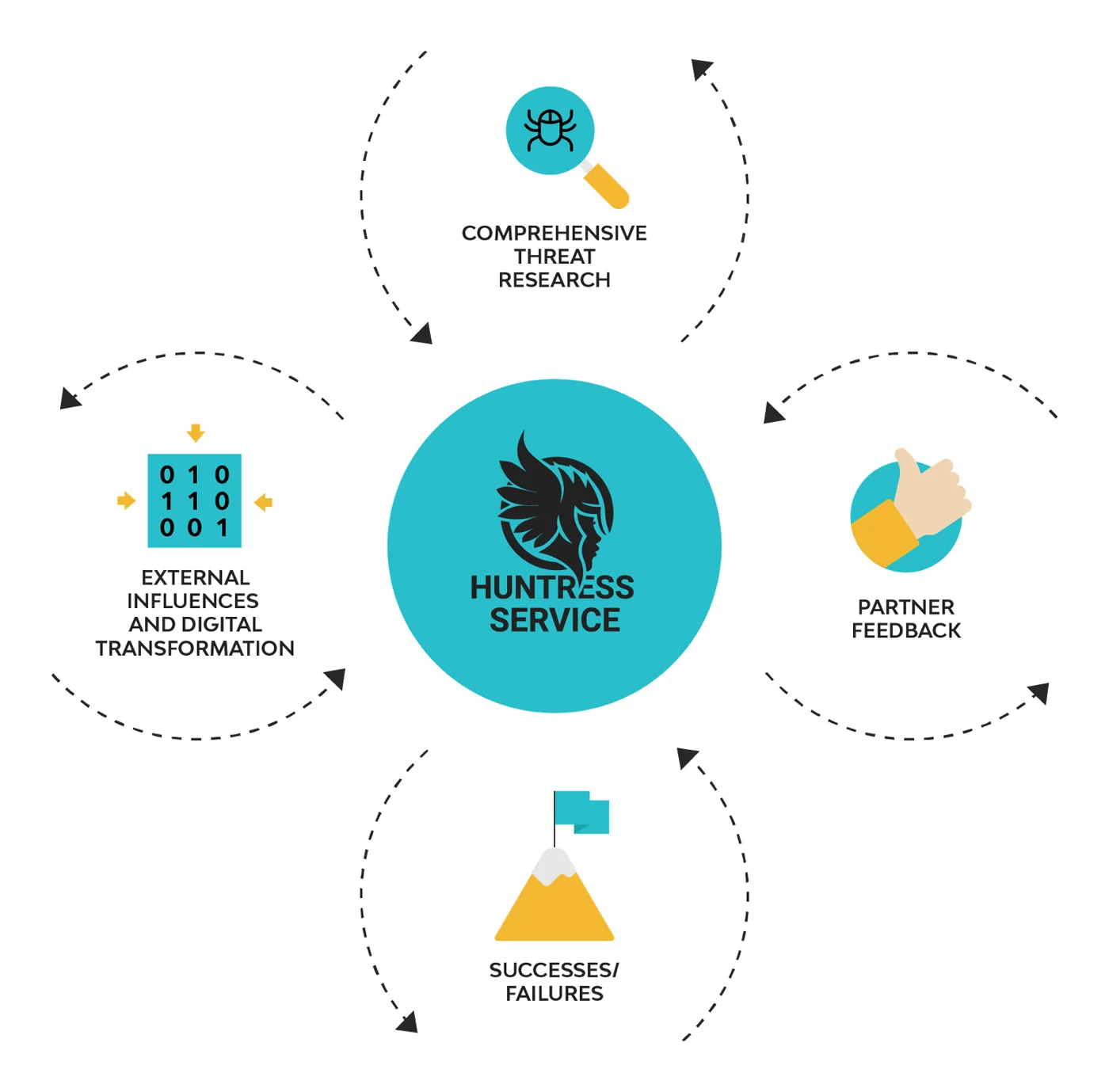
It turns out that the vision all along was to address this exact problem. Huntress is entering that pivotal moment in laying down our response. We are building a security platform that will continuously add new defense solutions to help small and medium sized businesses (SMBs) stay ahead of the evolving threat landscape. And we know that the best way to activate these defense strategies is by empowering our channel partners.
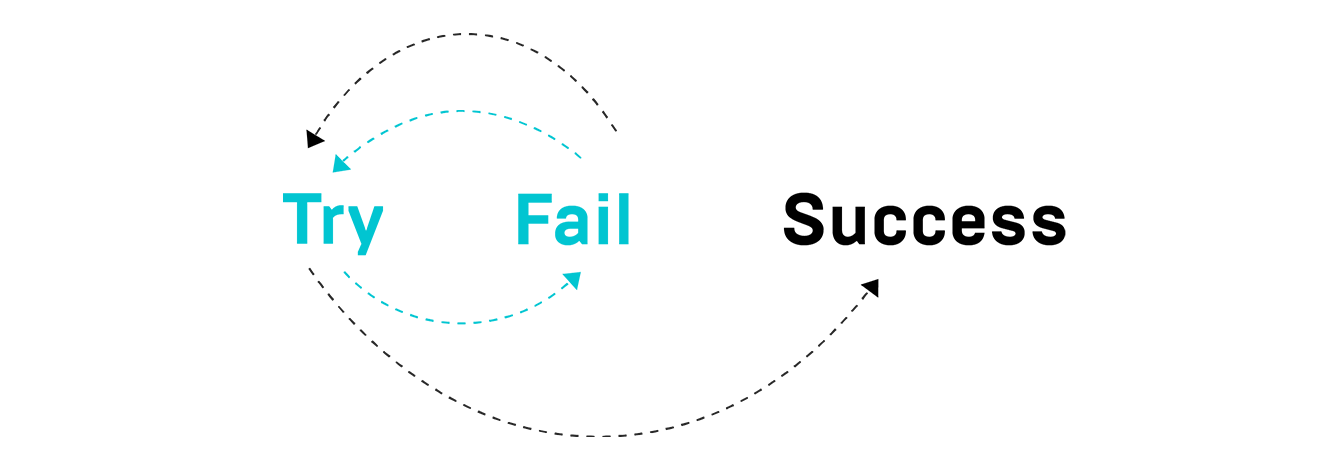
If You Haven’t Failed, You’re Doing It Wrong!
Let’s take a moment to understand the guiding principles that brought Huntress to this point. Our founders came from cyber offense working at the NSA and the name of the game is doing whatever it takes to achieve the objective.
If we think about this offensive perspective, failure is all part of the game. This sounds counterintuitive, but encountering failure has the power to teach and inform the next step. Attackers know this and benefit greatly from this mindset. At Huntress, we’ve realized there is no reason why defenders can’t benefit as well.
The key is knowing that you’ve failed and establishing a tight feedback loop. For many attackers, knowing when they’ve succeeded is very clear — the same can be said about knowing when they’ve failed. By failing often, attackers can regroup, readjust, and try again with a new approach (is this why it’s called “hacking”?).
As defenders, the playing field is much different. The definition of either success or failure is much less tangible and often difficult to grasp. But this doesn’t diminish the need for constant iteration to update our defense. We’ve already stated how attackers adapt their techniques and tactics based on the lessons learned from failure, but there’s also changing business needs, digital transformation, and external factors that influence how we establish our defenses. Defenders too need to stay agile and pivot quickly in order to stay ahead of the threat.
Where It All Began
When our founders came up with the idea around threat hunting by looking at persistence, they initially looked inward at their experience working in cyber offense at the NSA. I’ve heard Kyle tell stories about how he would often find his way onto adversary machines and once there, he was rarely ever discovered or kicked out. This idea gave birth to the Huntress methodology of hunting down persistence—a story now being told and shared with the community.
But there are so many more untold stories about both the changing threat landscape and the challenges our partners are facing today. With that, Kyle, Chris, and John decided to seek out these pain points and articulate these stories to make sure they get the attention—and innovation—they deserve.
Stories and Innovation
Over the last year or so, Huntress has been at the forefront of every major managed service provider (MSP) security incident. We are driven by the principle that the security community should share and come together to help one another.
To that end, when attacks impacting our community occur, our founders make it a point to offer their expertise in mitigation, hunting down root causes and spending countless hours providing hands-on support in any way possible. Through these first-hand incidents, we become extremely intimate with new threats and attackers.
With new threats comes time for innovation, and each new story from our partners guides our innovation towards delivering true value. In many instances, there are key problems that are rediscovered over and over again. For example, open external RDP ports are repeatedly seen as the entry point for attack. How can we innovate to find solutions to these problems that are impactful (to bring value) and accessible (so that they will actually be adopted)?
At the same time, solving a single new problem is never the end of the line. After defenders use these solutions to plug their external services, attackers will realize their attacks are overused and no longer effective. Attackers will be driven to pivot and create new tactics — causing the cycle to inevitably start all over again. What we also need is a way for defenders to more efficiently pivot themselves.
Tightening the Feedback Loop
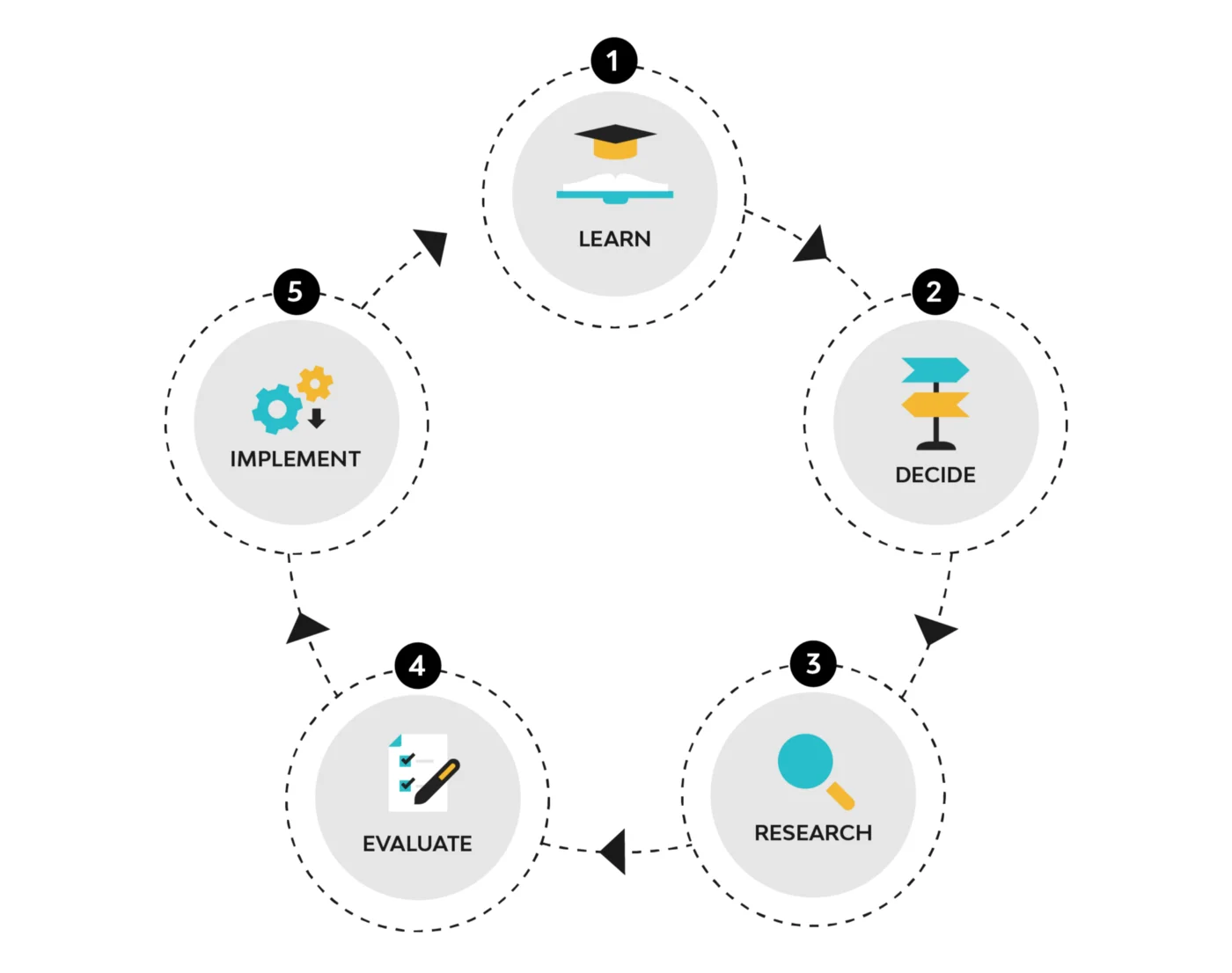
When we think about how most defenders or managers of IT approach security solutions, they typically go down this path:
1. Learn about a new attacker technique or emerging cybersecurity problem
2. Decide if this new problem is worth addressing
3. Research tools, features, or vendors that can offer solutions
4. Evaluate options or conduct a trial
5. Implement and manage full solution
Just looking at this, there is a lot to unpack and we haven’t even touched on the financial burden of finding additional dollars to fund this effort — let alone training on new technology and ongoing maintenance. After all this, what is the tradeoff between reduced risk vs. time and materials? And considering the sheer number of security problems that continuously emerge, how often does this cycle need to be repeated?
What we realized after listening to countless partners describe the issues they face is that they need a service that will enable them to quickly evolve and remove obstacles that slow down that evolution. This is where the Huntress Platform steps in.
Just Tell Me What It Is!
As Huntress takes on this transformation, our partners will start to see a platform that evolves with the changing security needs.
Here’s how it will work:
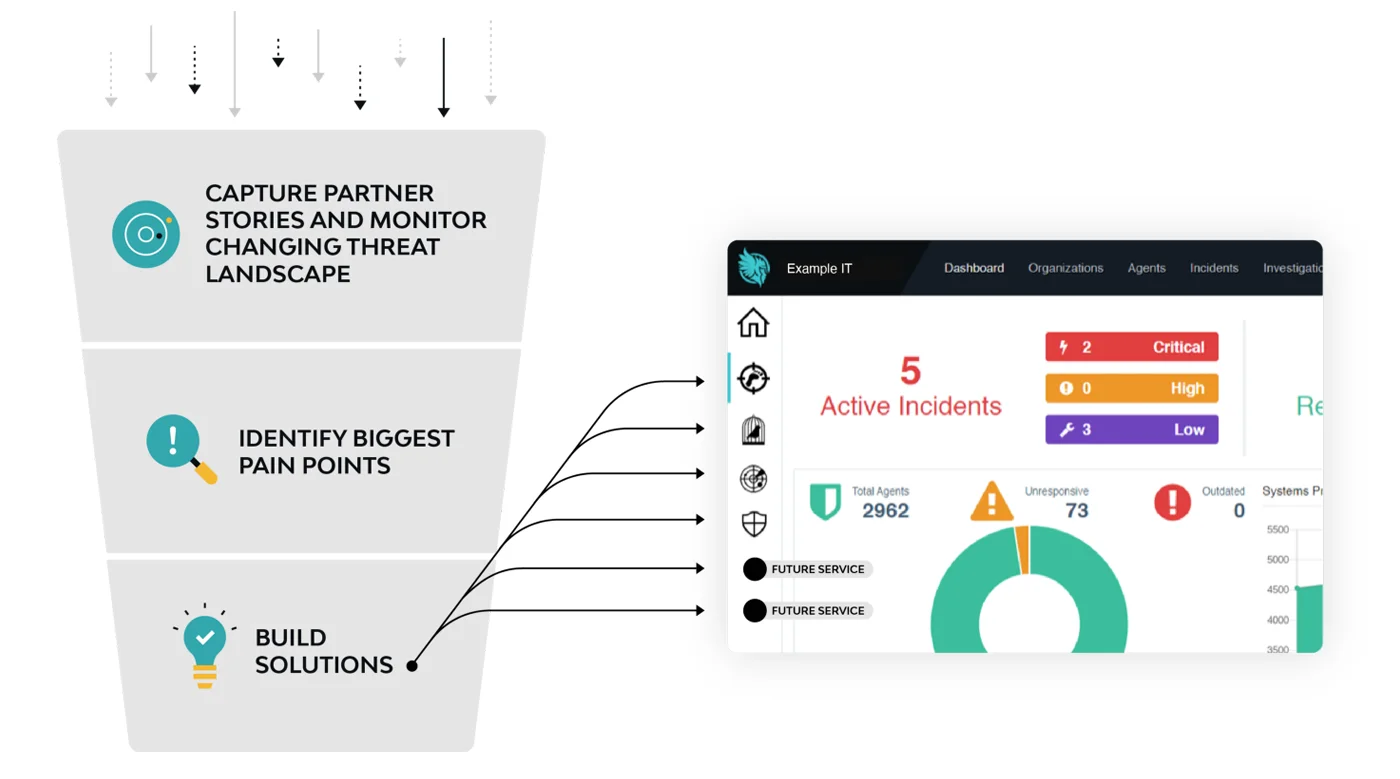
As we listen and understand more of the challenges our partners face, we will distill the key problems and innovate new solutions that also incorporate what we’ve seen from our own threat research. These will appear automatically in the Huntress dashboard as a new service for our partners in order to address new emerging challenges.
What do we mean by “appear automatically”? If we go back to the Cybersecurity Adoption Cycle, there’s a ton that goes into choosing a new security solution. The technical design and implementation is one thing, but what about how it affects partner business models? In so many of our conversations with partners, we’ve heard questions such as:
- How do I bake in a new point product w/ my existing service packages?
- How do I sell yet another security solution to my end customers?
- How do I balance productivity with security?
Attackers are evolving right around us, not waiting for us as we evaluate options and make our next move.
At Huntress, our goal is not only to chase after these changing threats but to remove as many obstacles as we can that get in the way of our partners adopting new security innovation, ultimately helping them grow their business.
One Level Deeper
In addition, these services themselves will go through their own evolution based on partner feedback and the way attacker tactics themselves change. For example, the ransomware of tomorrow may not look like the ransomware we see today. Our solutions need to quickly evolve with these changes.
In this first round of the Huntress Security Platform, we are announcing two new services at no additional cost:
Ransomware Canaries will enable faster detection during a ransomware incident in order to enable a more timely response. We’ve seen first hand so many instances where a ransomware outbreak has occurred, leaving our partners seeking answers around when the encryption began, which endpoints were infected, and if the infection is spreading. Faster detection leads to faster response.
Open Port Detection will provide visibility into the external attack surface starting with external port monitoring. The goal of this service is to highlight low-hanging exposures that attackers often gravitate towards when launching their attacks. A perfect example is one we highlighted earlier: open RDP. Alerting on these low-hanging exposures offers actionable next steps into improving security posture and providing visibility into changes.
Closing Thoughts
This vision of creating a continuously evolving platform has been active in the minds of our founders since Huntress’ inception. Rather than being just a single stop along the security journey, we want to give our partners the ability to clearly identify their top security problems and quickly implement solutions.
By lowering the barrier to entry for effective cyber defense, we are enabling more organizations to increase their security postures — ultimately making it harder for attackers. Coupled with some recent momentum, this was the perfect time to buckle down and turn this vision into reality.
Stay tuned. This is only the beginning.