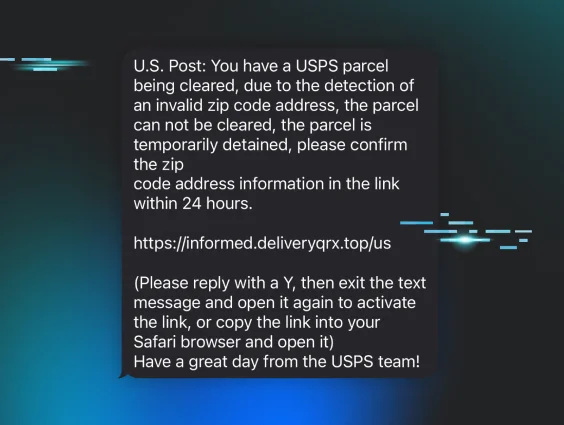
Have you recently received a text message urging you to take action to avoid a negative outcome? Maybe you’ve just been informed you have an outstanding toll fee, or more likely, there’s a package for you being held due to a shipping issue. These are almost always smishing (or “SMS phishing”) attacks.
What Is Smishing?
Smishing attacks are a form of phishing where fraudulent text messages are sent to trick victims into clicking malicious links, providing sensitive information, or taking other harmful actions. It's crucial to remember that these urgent messages are often a ploy to catch you off guard. With the rise of AI tooling, smishing campaigns are even easier for attackers to launch and maintain these days. And, during the holidays, you can expect the number of smishes you receive to increase. After all, attackers know that you’re more likely to be traveling and receiving more shipments, so this timing typically results in higher “conversion rates.”
Below, we’ll break down one of the most popular smishing attacks over the past few months—package tracking scams.
How the Smish Begins
It’s no longer uncommon to find a text like the following sitting in your inbox.
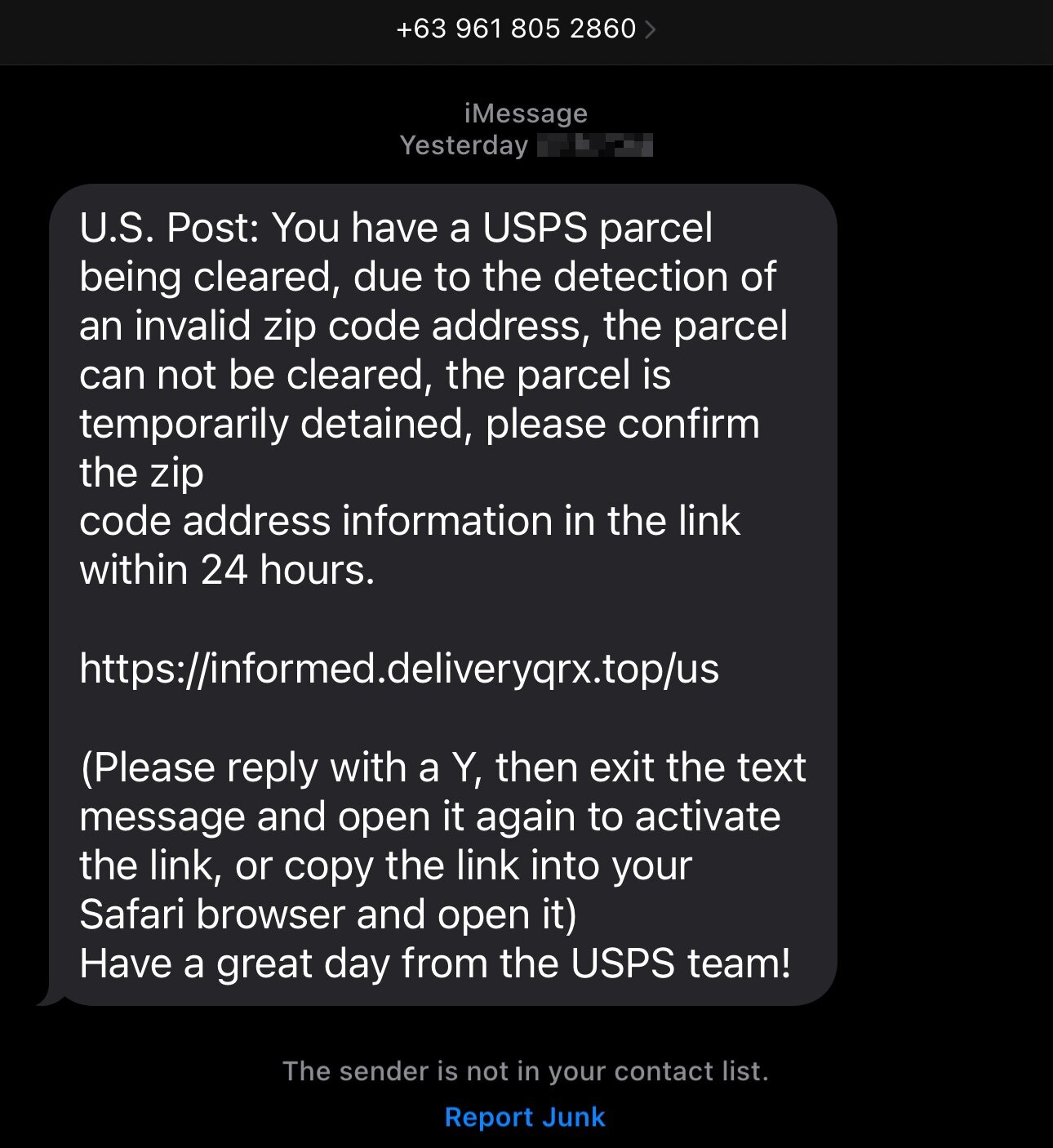
As you can see, the message—though the country code is from the Philippines—states that there’s an issue with your United States Postal Service (USPS) shipment, and you need to go to a specific link to confirm some information.
In the example above, the link isn’t clickable. But not to worry, the scammers have kindly added helpful instructions. Not only will replying to the message make the link clickable, it will also:
- Improve the deliverability rates from this number to other victims
- Let the scammers know that your phone number is “live,” likely resulting in you receiving more smishes in the future
In any case, navigating to the link in the message takes us to what looks like a legitimate USPS website.
Sites Might Look Legit, but Look Closer
In any good smish, you’ll be directed to a fake site that, upon an initial glance, might be indistinguishable from the real thing. Case in point, here’s the USPS site we end up on.
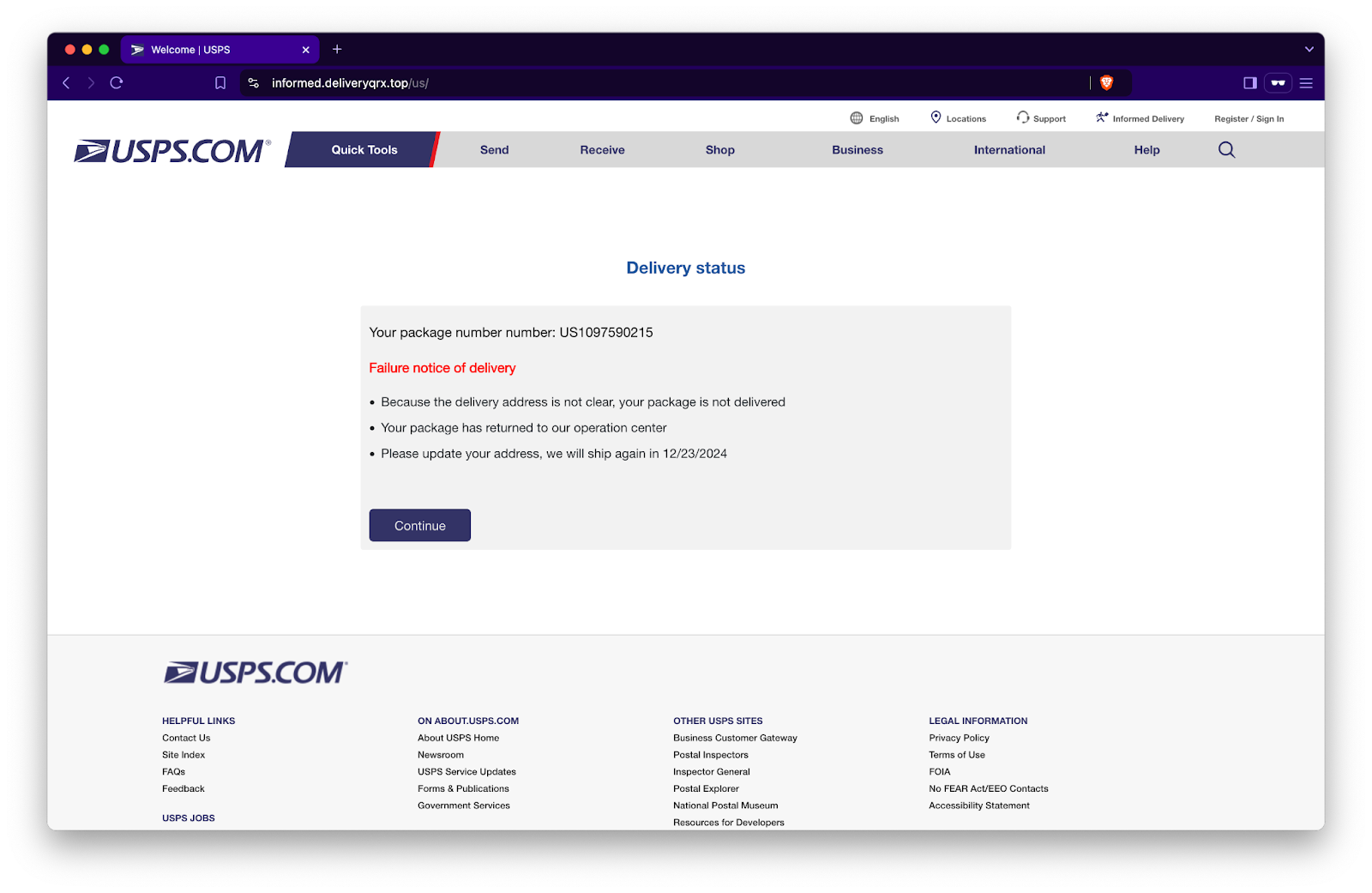
Ignoring the URL bar, the site we’re directed to looks legitimate. Sure, the message box could be a little more polished and proofread, but as you can see below, the menus work, even leading to real USPS website links.

So what happens when we click ”Continue,” blindly trusting that the “package number number” in the "Delivery status” box is our own? Let’s find out.
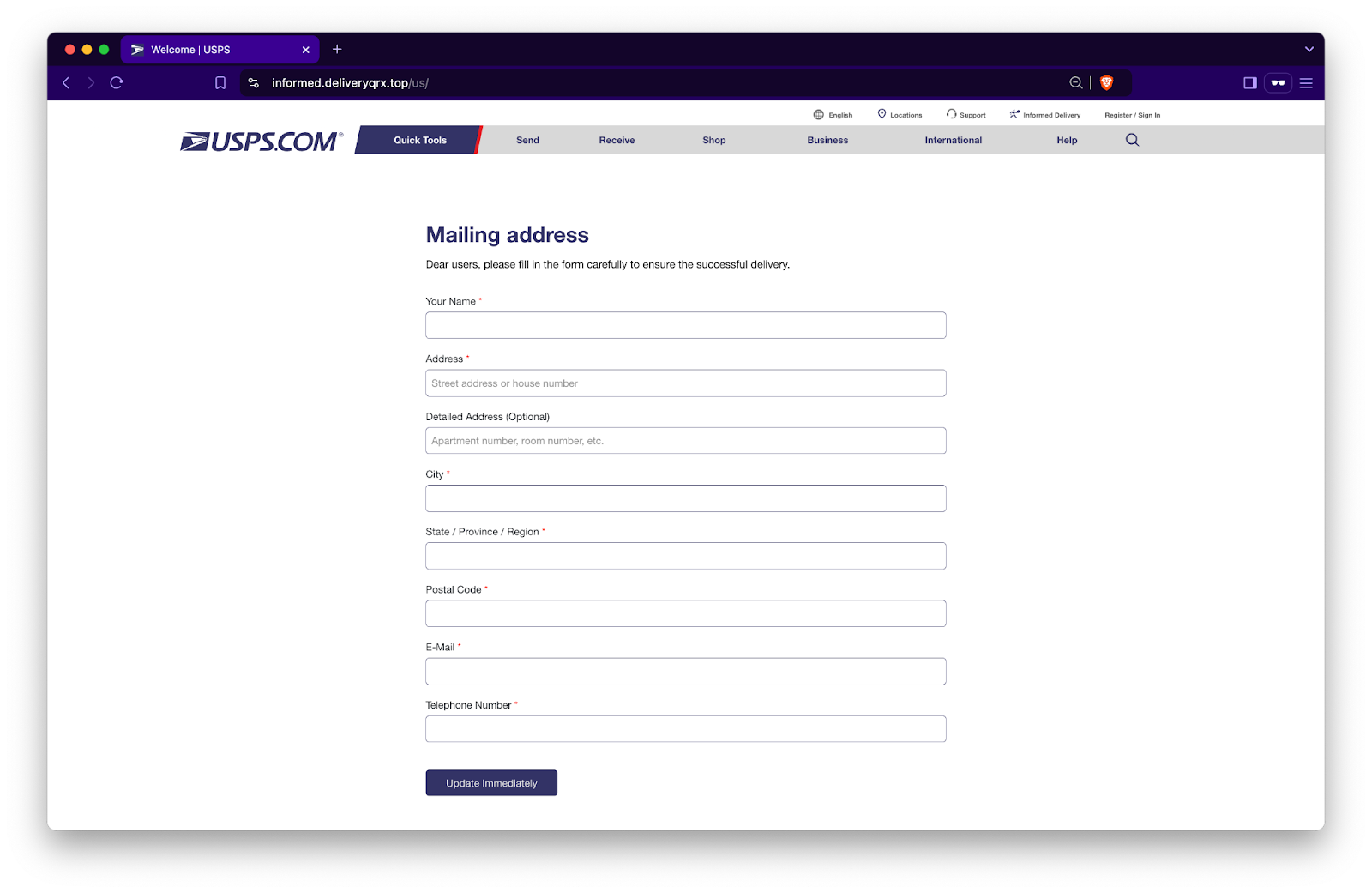
You’re asked to input your “Mailing address” and telephone number. Before we proceed, take note of odd language like “dear users” and the inconsistent capitalization in the header compared to other forms of capitalization on the page. These should have your “Spidey senses” tingling. But, let’s suppose the alarm bells aren’t going off just yet, so you continue to enter your information and hit the “Update Immediately” button. What happens next?
How Scammers Score: Getting You to the Payment Page
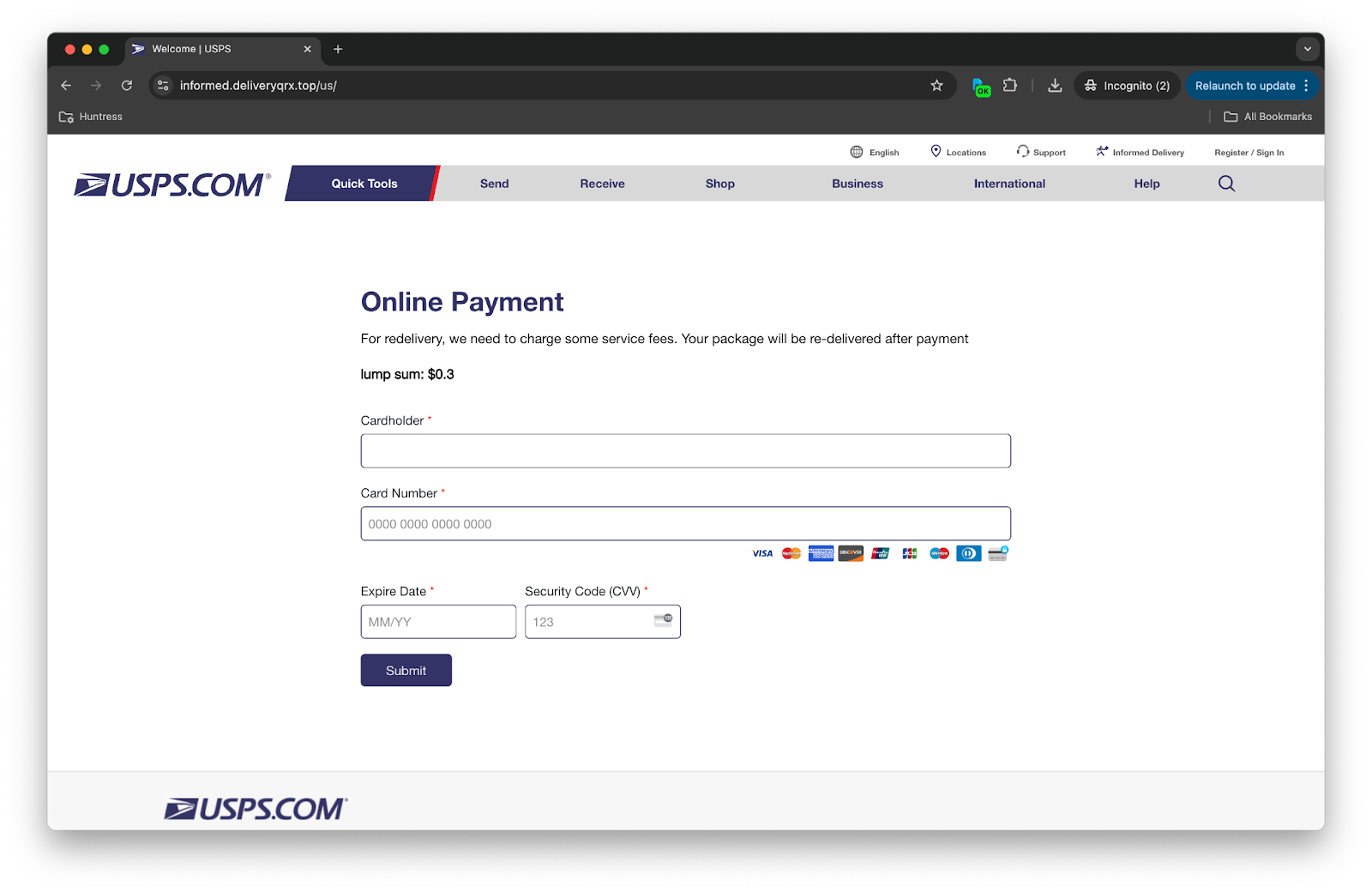
As you can see above, you’re now asked to make an online payment—a “lump sum” of just $0.3! This is, allegedly, for the redelivery of your package. But take note of the multiple red flags on this page. When’s the last time you’ve seen something aside from lottery winnings referred to as a “lump sum,” let alone costing 30 cents? Not only that, the “$0.3” leaves off the trailing zero, which is uncommon. Additionally, the second sentence in the description doesn’t have a period like the first one. And the first sentence is simply too casual for USPS: “...we need to charge some service fees.”
Well, let’s pretend you’re not on top of your game and you just need your mystery package, so you input your payment information and press “Submit.”
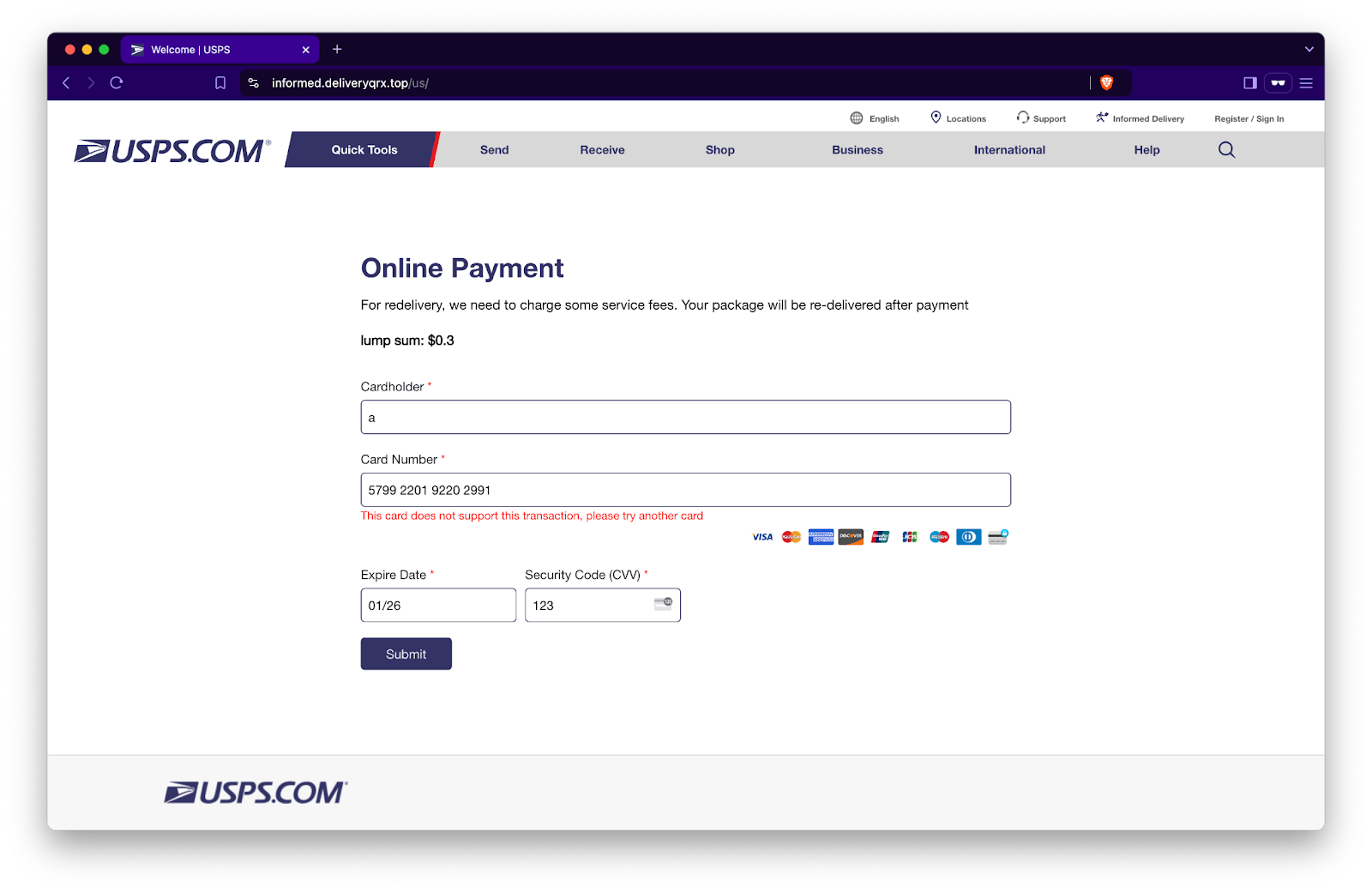
Your card didn’t work! Luckily, the helpful red error message tells us, “This card does not support this transaction, please try another card.” Hmm, that’s odd because you just used it to buy coffee this morning. After a second attempt, you get the same message. That’s when you follow the instructions and reach for an alternate credit or debit card, fill out the form, and submit it again. But the strangest thing happens—no matter how many cards you try, you keep getting the same error message. Only after trying four cards do you either:
- give up and decide to call USPS, or
- realize that this is a scam
Unfortunately, whichever option you choose, it’s too late. The scammers already have your billing information and at least one of your card numbers. It’s now a matter of time before they start being used, if not immediately. At this point, the best thing you can do is report your cards as stolen or use some other method of permanently disabling them. You also shouldn’t be surprised if you get even more phishing emails moving forward, as the scammers have the personal information you provided to them.
Why Was This Attack Successful?
There are several reasons this smishing attack is successful.
- Well, it’s the holidays, and you’re probably expecting packages often around this time of year. For that reason, the message was relevant.
- If you read that your package is “detained,” along with the time-sensitivity of having only 24 hours to fix the issue, you’re more likely to take action without thinking. The scammers successfully instilled fear and urgency, both of which are very powerful in social engineering attacks.
- When you head to the website, it does look legit. Are there things that stand out? Sure. But if you made it this far—past all the red flags in the initial message itself—you’re less likely to spot the red flags on the fake site.
- After your first card doesn’t work, you’re likely to try a second or even a third card. Why? Sunk cost fallacy. You’ve already taken all of these steps and you want your package!
How You Can Protect Yourself
The scammers have constructed this attack relatively well, which is probably why it's being seen so often in the wild. The simple truth is it’s working. Not all hope is lost, though—there are ways you can protect yourself from smishing attacks:
- Never take action based on a sense of urgency in a message. Always stop and think, especially when you’re being rushed. Remember, you are in control.
- Off the top of your head, take your best guess at what the USPS web address could be. Most of you might guess “usps.com,” and guess what, you’d be right. When you see a URL like “informed.deliveryqrx.top” in the original message, alarm bells should be blaring. Even if a link looks legitimate, never click or follow links in messages unless you specifically requested it or are expecting the message. When in doubt, use a secure, verified method of getting to the website you’re looking for, then navigate from there.
- Confirm the validity of the issue. In this case, is the tracking number shown on the website tied to one of your shipments? An easier route may be to go to the order history for the recent shopping you’ve done and check for shipping issues on the retailers from which you checked out.
- Look out for spelling and/or grammatical errors. This particular example was what you could consider a “good” attack, but there were things that still stood out, which I pointed out throughout this post. Punctuation, terminology, choice of words, and inconsistent capitalization should have given you pause. Trust your instincts.
- I’ll start this last point by saying that phone numbers CAN BE spoofed for calls and texts you receive. That means that it’s possible for an attacker to call or text you from (what appears to be) the phone number of their choice. However, in this case, the fact that this message—supposedly from USPS—came from the Philippines, is a massive red flag. To be clear, this doesn’t mean that if you get a text message or call from a phone number you recognize, like that of your bank, you should trust it blindly. You shouldn’t. But that doesn’t mean that you should ignore an obvious red flag either.
Smishing attacks can be tricky, especially when timed strategically by attackers. My best advice is this: most unsolicited messages you receive should be ignored. If, after slowing down, thinking critically, and looking for signs of phishing, you still believe that a message may be legitimate, verify it by navigating to the source on your own. Do not follow links or instructions in the message.
If you end up in a situation where you realize after the fact that you were phished, take immediate action. In the example we reviewed, you’d want to get your compromised payment cards disabled/reported, and internalize the fact that any personal information you provided may be used against you in future attacks. In the event that you entered your credentials, they’re now compromised and you need to immediately rotate them wherever they’re used. Hopefully, this should only be for one website if you’re following the golden rule of using unique passwords for each site (made much easier with a good password manager).
Avoiding becoming a victim of social engineering attacks may seem daunting, but if you remain vigilant and aware of how attackers operate, you’ll be just fine. Here’s to a happy, secure new year!