







If you've been in cybersecurity for a minute, you know malware doesn’t just show up and disappear. Hackers don’t drop a payload and call it a day—they dig in, adapt, and stick around for as long as they can.
Legacy antivirus (AV) and super SUS EDR/MDRs will lob you a one-off alert, but stopping these threats isn’t about catching one-off alerts. It’s about finding and shutting down the persistence that keeps them in your systems. If your security isn’t built for that, threats will outlast you.
That’s where Huntress Managed Endpoint Detection and Response (EDR) comes in. It catches what others miss and helps kick attackers out—for good. But why tell you when we can SHOW you…
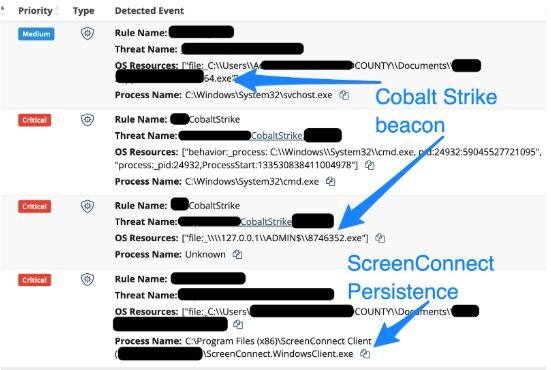
Threat actors don’t discriminate—they’ll go after anyone, including local government. In one case, a county employee got tricked into installing a remote access tool via email. The attacker:
Huntress—utilizing its Managed Microsoft Defender setup—shut it down before things got worse. But here's what you can do to avoid being next:
✔️ Secure every endpoint (not just servers—users' machines too)
✔️ Train your people (users who can’t be tricked stop attacks before they start)
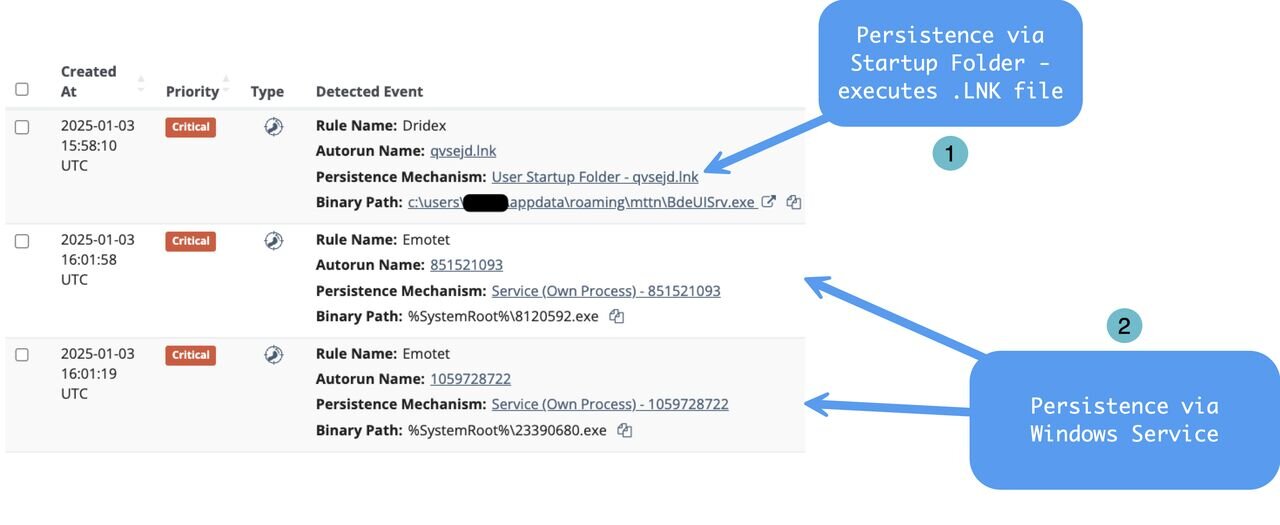
Some malware doesn’t just infect a system—it moves in, unpacks, throws on a Snuggie and gets cozy. Back in 2018, a healthcare diagnostic center found that out the hard way. A user unknowingly interacted with persistent malware that secured a foothold through:
For years, this malware sat undetected. Then, on January 3, 2025, Huntress was deployed to the environment. Within an hour, every trace of it was identified and eliminated.
🕵️ Want to hunt persistence yourself? Start here:
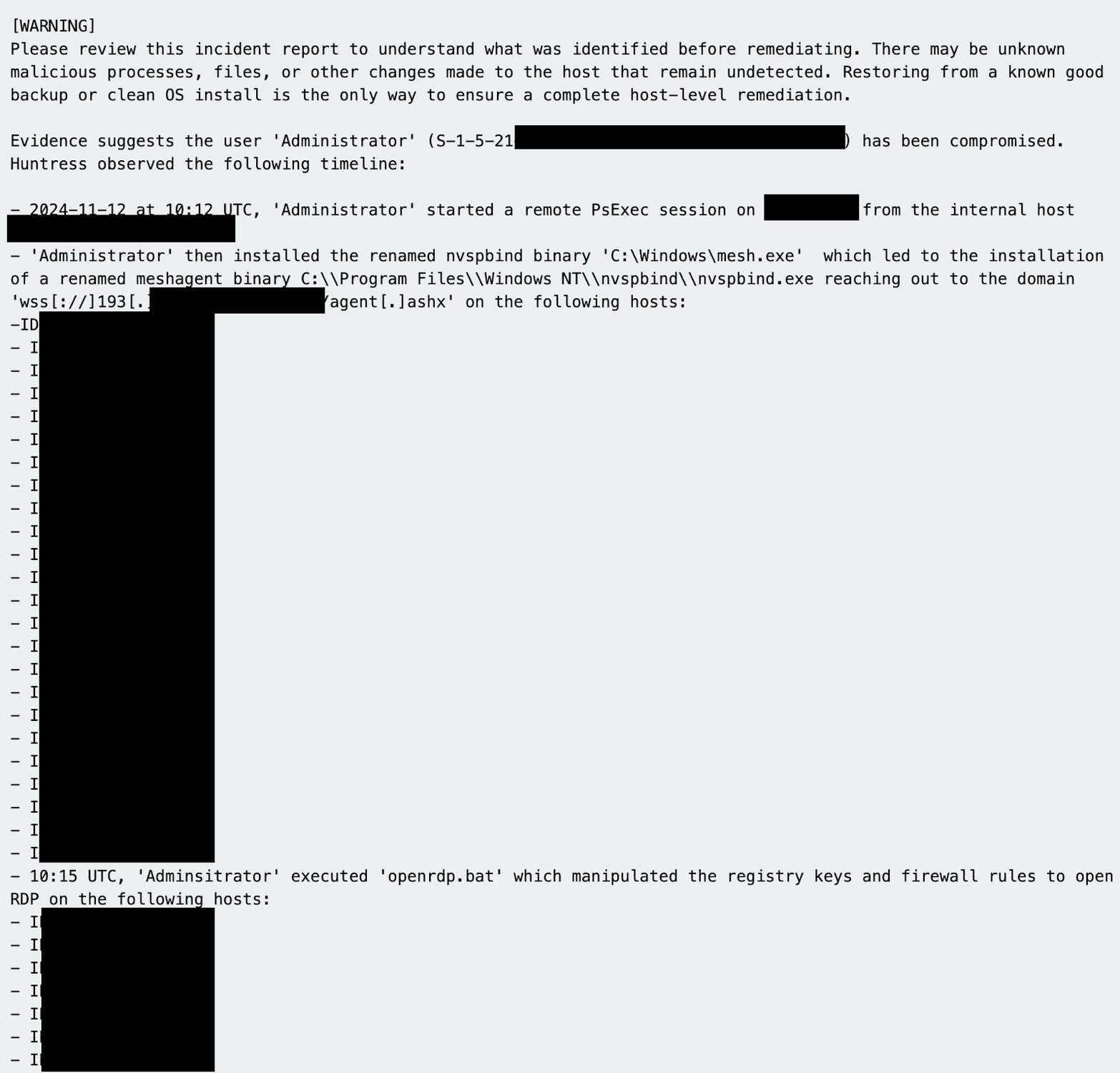
A medical research company exposed a remote desktop gateway (RDG) server to the internet. Predictably, attackers brute forced their way in and:
🚨 Compromised the Administrator account
🔄 Used PSExec to move laterally
🔓 Disabled Windows credential protection
📡 Modified the Windows firewall to allow more remote desktop protocol (RDP) traffic
🛠 Established persistence using a renamed Mesh Agent
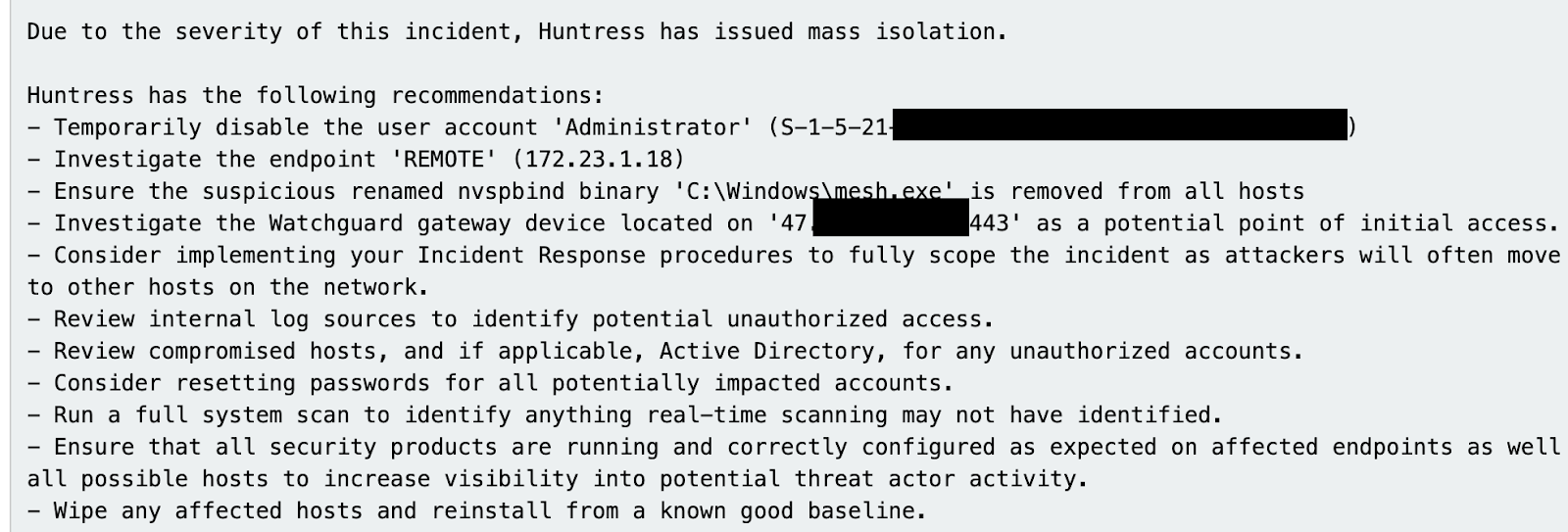
Within minutes, Huntress detected the compromise, isolated the network, and helped them evict the threat. If you’re running an RDG server, ask yourself: Is it locked down? Am I monitoring authentication attempts? Do I even need it exposed?
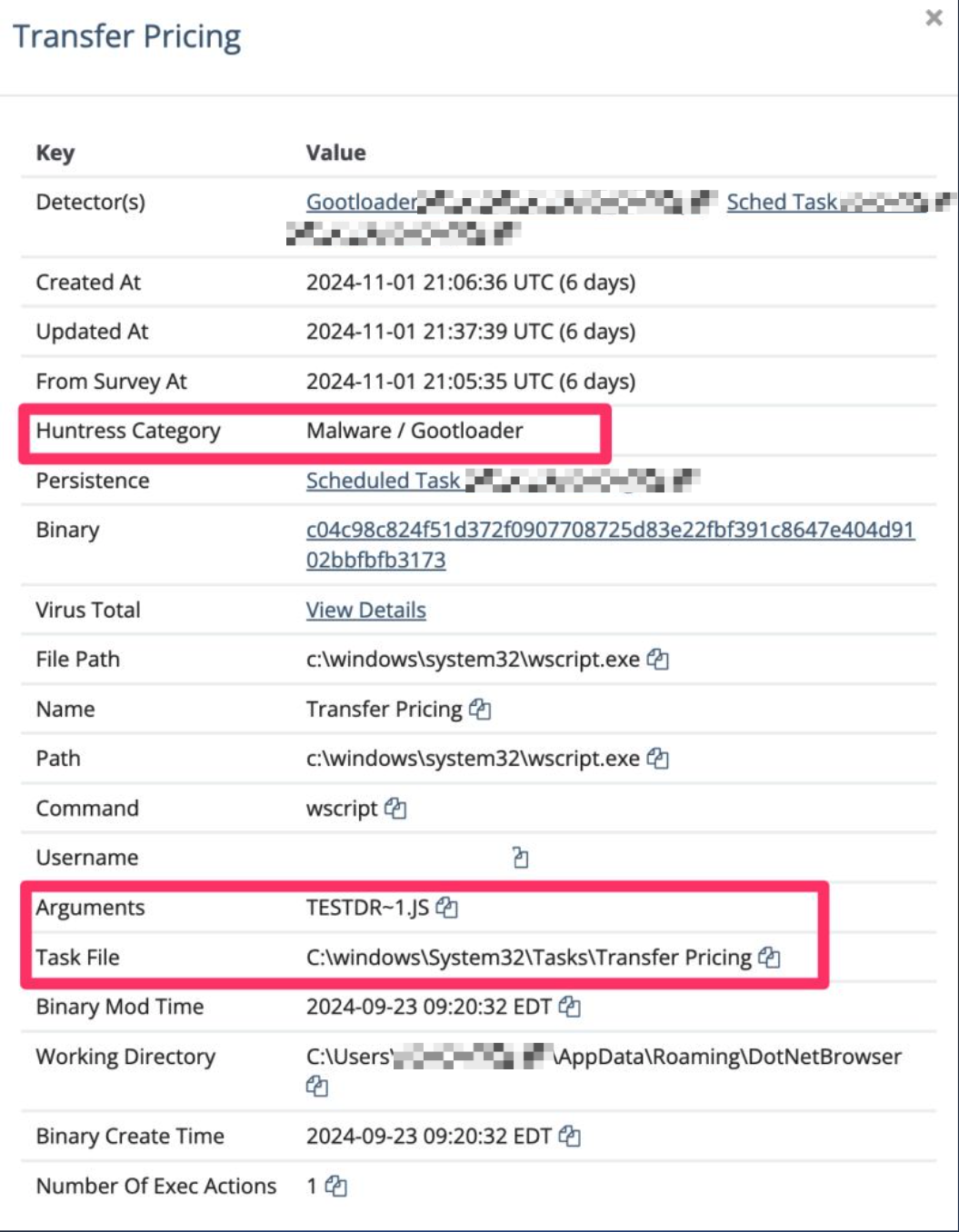
If your users aren't security-aware, you’re making an attacker’s job way too easy. A manufacturer found that out when an employee downloaded Gootloader malware via an SEO poisoning attack. From there:
This whole mess could’ve been avoided with security awareness training. If users don’t know what’s risky, they’ll keep clicking bad links. Train them. It works.
These aren’t hypotheticals. They’re real cases—threats that sat for years, attacks that bypassed traditional defenses, intrusions that could've led to massive breaches. Managed EDR isn’t just another security tool; it’s your always-on Security Operations Center (SOC), your malware-hunting team, your real-time incident response.
Ask yourself:
If any of those answers aren’t a strong “yes,” you might already have an attacker poking around. Let’s fix that. We invite you to (ab)use our free trial and maybe find something shady you didn’t previously know about.
Get insider access to Huntress tradecraft, killer events, and the freshest blog updates.
