







Hackers are pros at hide and seek. Once they’ve slithered their way onto an endpoint, they usually try to escalate privileges, establish persistence, steal credentials, you name it—all while trying to disguise their malicious activities along the way.
Here at Huntress, one of our favorite things to do is to expose the tricks hackers have up their sleeves. And in a recent webinar, we did just that.
You can watch the on-demand recording here or keep reading for a quick recap.
Huntress experts Ed Murphy, Director of Product, and Josh Lambert, Technical Product Manager, joined together to present EDR in Action: Protecting Your Endpoints from Today's Cyber Threats. During the webinar, we explored:
We built our roots in finding what other security tools missed. At first, that included things like persistent malware, malicious footholds, ransomware and other low-hanging fruit for attackers. But it was always our vision to expand and provide “wider” coverage across the modern attack lifecycle.
That led us to create our Managed Antivirus feature, which marked Huntress’ first entry into preventive security. From there, we added new capabilities like Host Isolation to ensure machines could quickly be quarantined and disconnected from a network to stop the spread of an attack as it was being carried out. But as always, hackers continued to evolve. And so did we.
Enter Huntress Managed EDR—the newest addition to our managed security platform that is designed to help stop cyberattacks in real time.
When building Huntress Managed EDR, our aim was to create a solution that would have deep visibility into endpoint activity in order to stop issues before they become problems. And we knew EDR’s ability to recognize behaviors and categorize them as a threat (or not) enables that.
So here was our hypothesis: Our partners needed better multi-tenancy support, fewer alerts they can’t make sense of and faster intelligence on threats.
Huntress Managed EDR is active on nearly 2 million endpoints. In a nutshell, we’ve seen some crazy sh*t. Here is some of the most notable carnage we’ve come across.
In a typical remote system access scenario, the user is the client and the target machine is the server. The user initiates a remote shell connection, and the target system listens for such connections. With a reverse shell, the roles are opposite. It’s the target machine that initiates the connection to the user, and the user’s computer listens for incoming connections on a specified port.
So why is this a troubling attack tactic? Most firewalls are configured to stop connections going in, not out.
Here is Josh Lambert recreating this type of attack for us.
Defense evasion is always a fun one because we get to see the great lengths that attackers will go to blend into the background and keep their attacks hidden for as long as possible.
One of the less subtle forms of defense evasion is when threat actors try to turn off the security solutions present on an endpoint. But in this example, we were surprised (and somewhat flattered) the see Huntress as the attempted uninstall target.
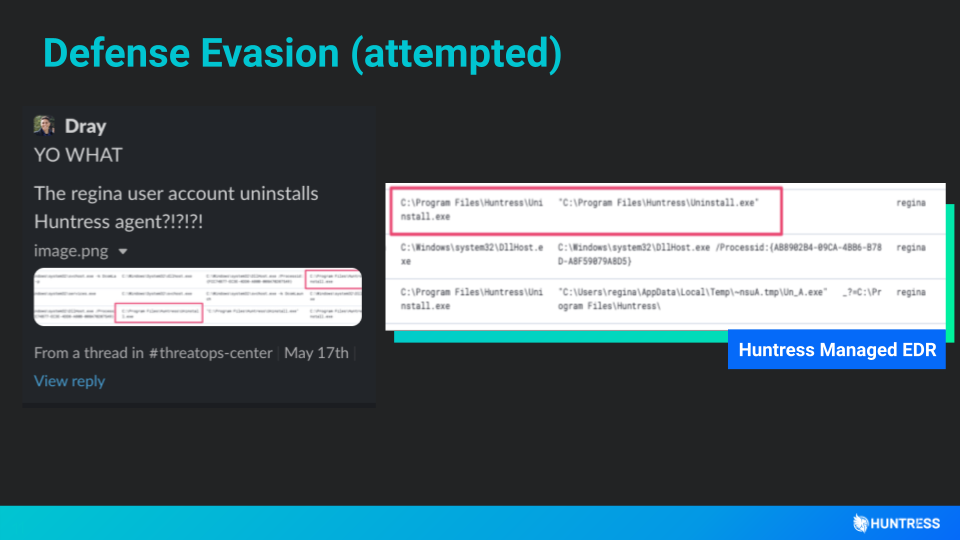
Here, Huntress Managed EDR revealed the “regina” user account attempting to uninstall Huntress. We quickly caught on to this, and I guess you know you’ve made it as a security vendor when threat actors actively try to uninstall your agent.
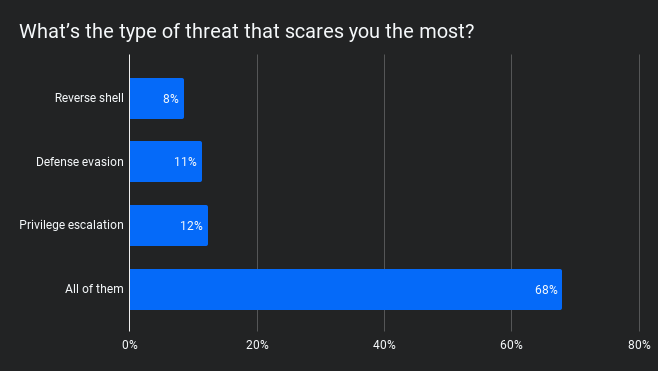
We covered a few more attack tactics, but reverse shell, defense evasion and privilege escalation were clearly some of the most pervasive attacks we’ve seen—and according to poll data, they’re all ones that our audience was scared of. 😱
I won’t spoil all of the fun we had during this webinar—I definitely recommend giving it a watch.
If there’s one thing we learned, though, it’s that there are so many avenues to compromise today. Every endpoint is a target, and that can be scary, but it also emphasizes the important role that endpoint detection and response plays in protecting yourself or your customers from these types of attacks.
Get insider access to Huntress tradecraft, killer events, and the freshest blog updates.
