







From scam messages to fake websites, if you’re online long enough, you’ll encounter phishing. And that’s why security awareness training (SAT) exists. The goal of any SAT program is to help end users make smarter decisions when conducting themselves online. However, we’re all human, and nothing that involves humans is perfect. People will always make mistakes, especially when it comes to phishing emails. There will even be repeat offenders. That’s why we use phishing scenarios in Huntress Security Awareness Training to identify your highest-risk users before they click on a real phish.
Mistakes are a natural part of the learning process, but it’s easy to stifle an opportunity to make a meaningful behavioral change when someone is made to feel bad for clicking on a phishing simulation email. Instead, these mistakes should be viewed as a chance to coach someone on how to understand how they were tricked and what they can do to avoid these situations in the future—that’s the philosophy behind Phishing Defense Coaching.
Most phishing simulation tools will send learners an alarming message that reprimands them for clicking, provide no follow-up for compromised learners, or assign them to a generic “recovery training” that doesn’t do much to correct potentially harmful behaviors.
With Huntress SAT, a learner who clicks on one of our phishing scenarios will automatically be enrolled in Phishing Defense Coaching. This will bring them to a virtual coaching session led by a Huntress Threat Researcher who tailors coaching to the specific scenario the learner interacted with.
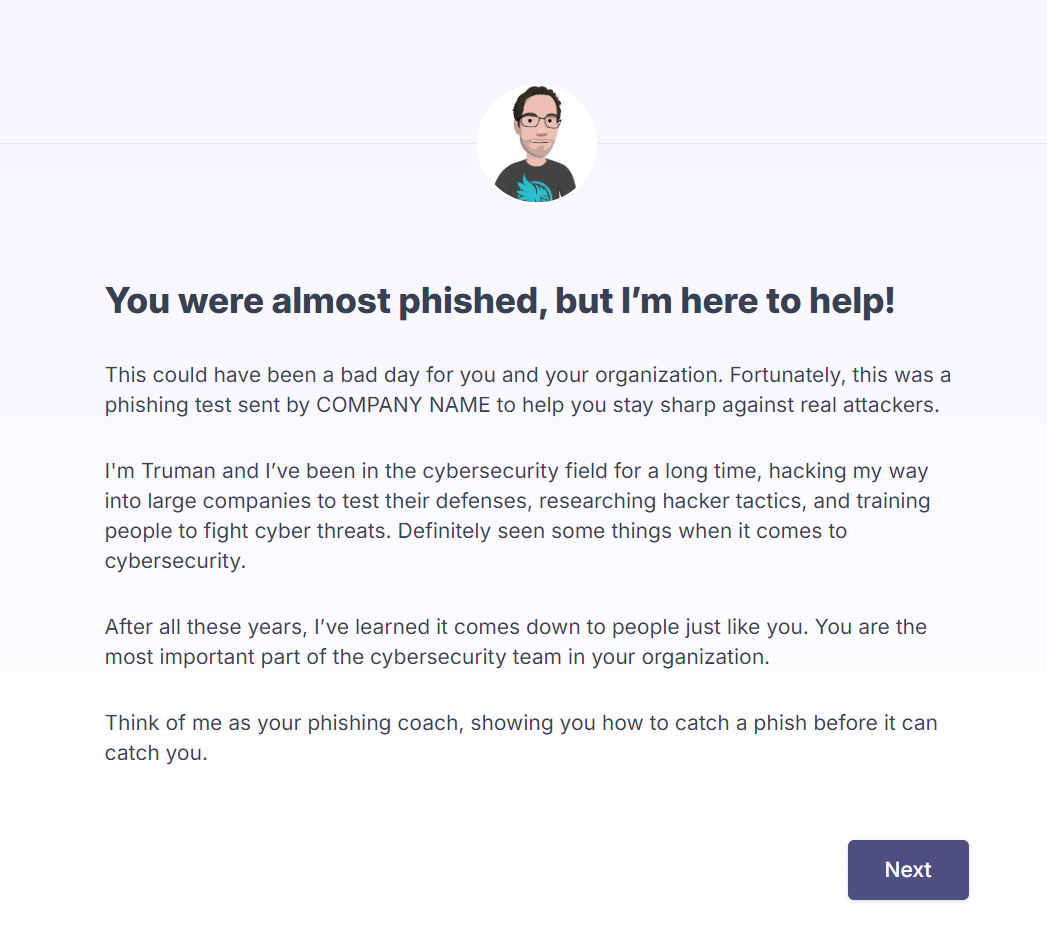
First, learners will be introduced to their coach and made aware that the link they clicked was a phish but, fortunately, just a test.
From there, learners will be asked to disclose why they clicked on the email. This is an important step because it not only determines the custom learning path they’ll be placed in but also compels the learner to rethink their motive for clicking while also providing the admins insight into those motives.

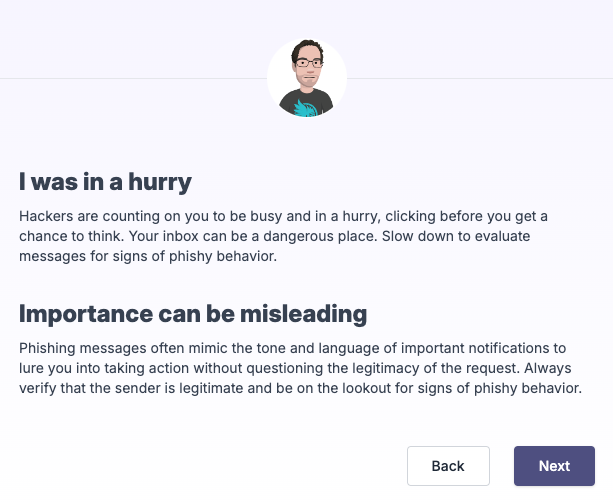
After selecting one or more reasons, the learner instantly receives coaching from a Huntress Threat Researcher who’s experienced in red team penetration testing and well-versed in thinking like a hacker. They’ll address the learner’s specific reason(s) for clicking the link and explain how hackers will exploit that mistake to take advantage of them. They’ll also coach the learner on how to correct this behavior in the future.
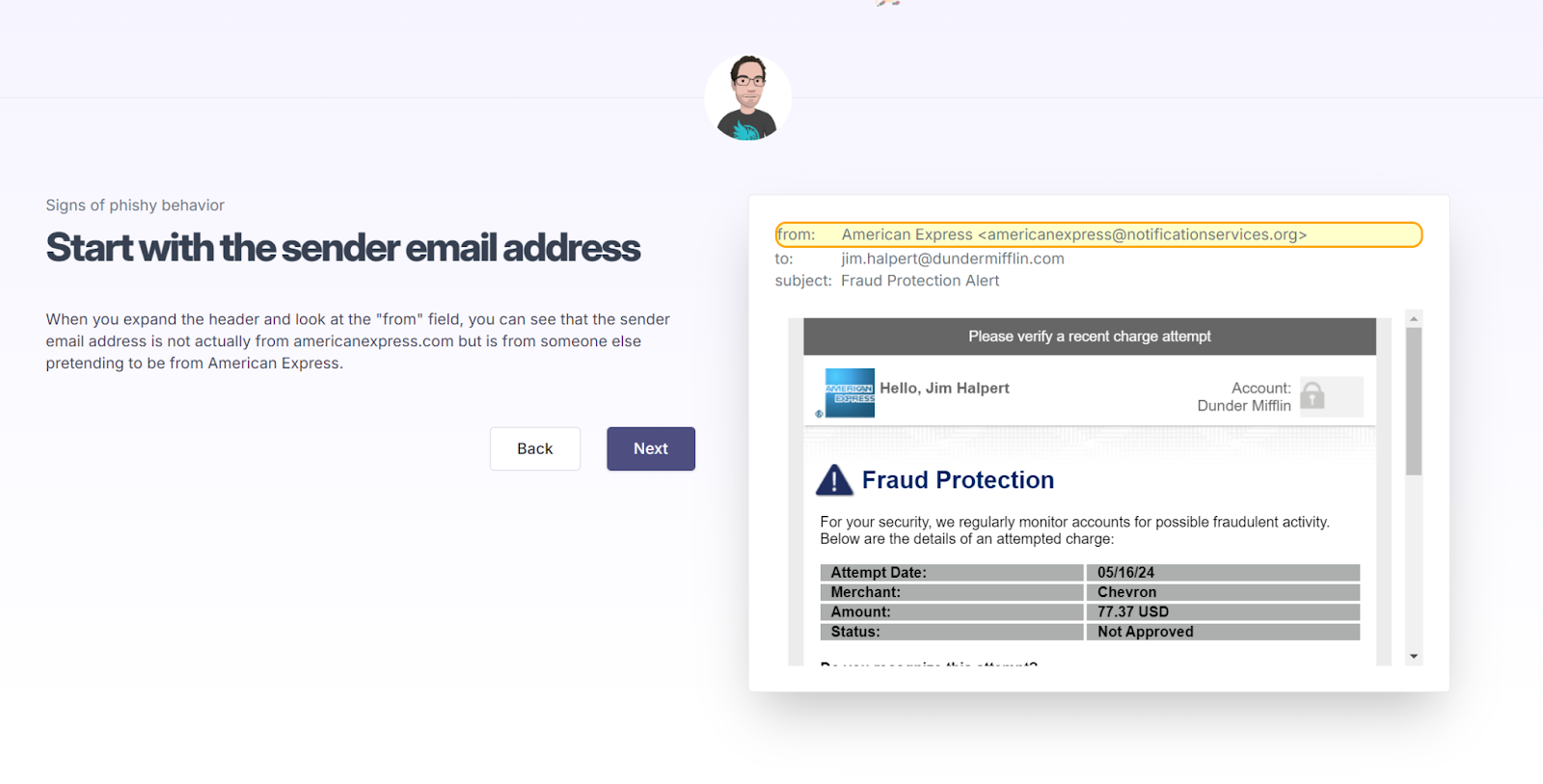
Learners will then complete a brief knowledge check before examining the email they interacted with. The coach shows them the exact phishing scenario they clicked on and highlights the areas containing potential phishing indicators so they know what to look for going forward. The learner can determine if the email may be malicious by identifying these potential risks—such as the sender’s email address or a sense of urgency in the message.
By walking learners through the same scenario they interacted with, the coaches help learners contextualize things they should’ve looked out for based on their real experience. It also helps them understand that phishing attacks can be highly sophisticated and difficult to spot, which gives them the confidence to identify and prevent risks moving forward.
Once learners have completed their coaching session, they self-report how prepared they feel to identify future phishing attacks. Admins can use this information to determine which users feel comfortable preventing future phishing attempts and which could benefit from more training.
A bonus from Phishing Defense Coaching is the direct learner feedback and data available to admins and our team at Huntress to help with the continued optimization of your training programs. During the open beta of Phishing Defense Coaching, we saw:

By understanding their learners’ confidence in identifying a future phishing attack, as well as the motivators driving them to click links, admins can better identify their users’ areas of potential risk and work to mitigate them. This is also valuable to the Huntress SAT team, as it helps us identify broader trends across the learner base to optimize training programs and produce better security outcomes for your teams.
Try it out with a self-guided tour.
Phishing Defense Coaching is just the latest cool feature we’ve added to Huntress SAT. And it’s now available at no additional cost with all Managed Phishing scenarios in Huntress SAT.
Get insider access to Huntress tradecraft, killer events, and the freshest blog updates.
