







The world of IT can be a confusing place.
There are many different sectors and disciplines, and they all have their own ways of approaching and solving problems. This inevitably leads to confusion, as each company or department uses the same terminology with a variation in definition depending on their own thoughts and ideas.
We’ve decided that we wanted to provide some clarity about these confusing situations and dive into the wonderful world of ‘managed’ cybersecurity.
First off, the word “managed” is pretty self-explanatory. We’re not here to pick any fights with Merriam-Webster.
But when looking at the word “managed” in the world of cybersecurity, there’s some variation in how vendors will use the word to describe the solution or service they offer. This comes up a lot with endpoint detection and response (EDR) solutions.

When we talk about managing an EDR, this is the element of human interaction—someone actively looking into security issues that the solution flags and curating a report or response to mitigate the threat.
We will give examples of what we’ve seen ‘managed’ mean in our space and dive down into what managed means to us.
Touching on the original point made around confusion, this really does stem from the acronym soup that is prevalent within our space. We explored a much broader look at this chaos in a previous blog. Today, we are going go with a depth-first approach, talking about:
Anyone looking at this list and thinking it’s a little ‘light’ would be correct. There are many more managed acronyms out there that refer to some level of management; however, we wanted to add a little specificity to what we are looking at and define it more toward Huntress.
Starting with the most general of this group, the MSSP (managed security services provider) acronym describes an organization that takes a generalist approach to managing security technologies. An MSSP often manages many tools from different vendors for their customer base. They are responsible for maintaining and managing these security tools and programs spanning areas such as network, identity, endpoint, and vulnerability. MSSPs ensure these tools and programs are delivering the technical function they are meant to perform, often focusing on prevention and alerting as outcomes.
MDR (managed detection and response) companies take a more targeted approach to your security. The primary focus of this type of offering is a team of security experts looking into data and telemetry being fed to them by a tool or group of tools to provide insight into any security threats going on within a customer’s environment. The emphasis is really placed on helping you out of a bad situation should a compromise happen. MDR will usually rely pretty heavily on artificial intelligence (AI) and machine learning (ML) to optimize the process for the human analysts looking into the threats that are presented. Is it very common for MDR offerings to be built around EDR products due to the visibility that they offer. However, providing meaningful security coverage from visibility into network or user authentication behaviors is possible.
We mentioned that EDR is the foundation of many MDR offerings, and to wrap up our conversation around “managed,” we wanted to talk about the two different types of managed EDR that we see out in the market. First, we’ll take a look at third-party managed EDR. This is where a company will take over “ownership” of another vendor’s EDR solution, offering help and advise where they can on the solution itself, as well as ingesting all information pertaining to threats the solution sees. From here, they will curate incident reports and suggestions on how to remediate any full-blown issues that are seen; however, the drawback is it’s not their EDR, so there is a limit to how much they are able to do.
Enter first-party managed EDR! This is one of those ‘best of both worlds’ situations. With first-party managed EDR, the product is a combination of visibility from the native software vendor and monitoring from subject matter experts who know their software inside and out. This makes sure that every element of the EDR itself is looked after and maintained, and establishes a virtuous cycle where the subject matter experts have a direct influence on the capabilities of the software.
Okay, we’ve set the scene and are now in a pretty solid place for understanding what each of the common acronyms means.
So which one does Huntress do? In the context of this conversation, we do the first-party managed EDR one (we offer other solutions, but for this blog, we are solely focusing on our Managed EDR offering).
Now, that could be it; we could stop there and have imparted some wisdom for the day. However, I don’t think this is the place to stop. We are striving to be different after all, and of course we aren’t the only ones that offer managed EDR out there, so let's change the question slightly…
In the simplest terms, Huntress' 24/7 SOC (security operations center) is how we deliver Managed EDR.
Our SOC team is the life source of how we make sure that we are managing the EDR effectively. Our security researchers are digging into emerging threats to understand how we might detect them, while our 24/7 analysts filter out the noise and report on the true threats that arise for our partners and customers around the world.
As we spoke about above, management of an EDR versus a managed EDR (third-party vs. first-party) is a pretty big differentiation to be made; however, both are going to offer levels of detection and response of threats within a company's endpoints. It becomes more specific and definitive when it’s everything is coming from the same vendor, allowing greater understanding and visibility into the data.
And it’s not just the technology differences that define Huntress. Many MDRs send unactionable, vague, or overly complicated reports after investigating an alert, requiring more investigation as to whether or not the MDR company sent something that was malicious or just something that looked malicious but is actually expected.
Huntress does that differently.
Our reports are curated by the good ol’ human investigators in our SOC team, giving you a solid understanding of which system(s) are affected, a straightforward explanation of the security phenomena and threat, and then guidance and recommendations of the next steps that make contextual sense.
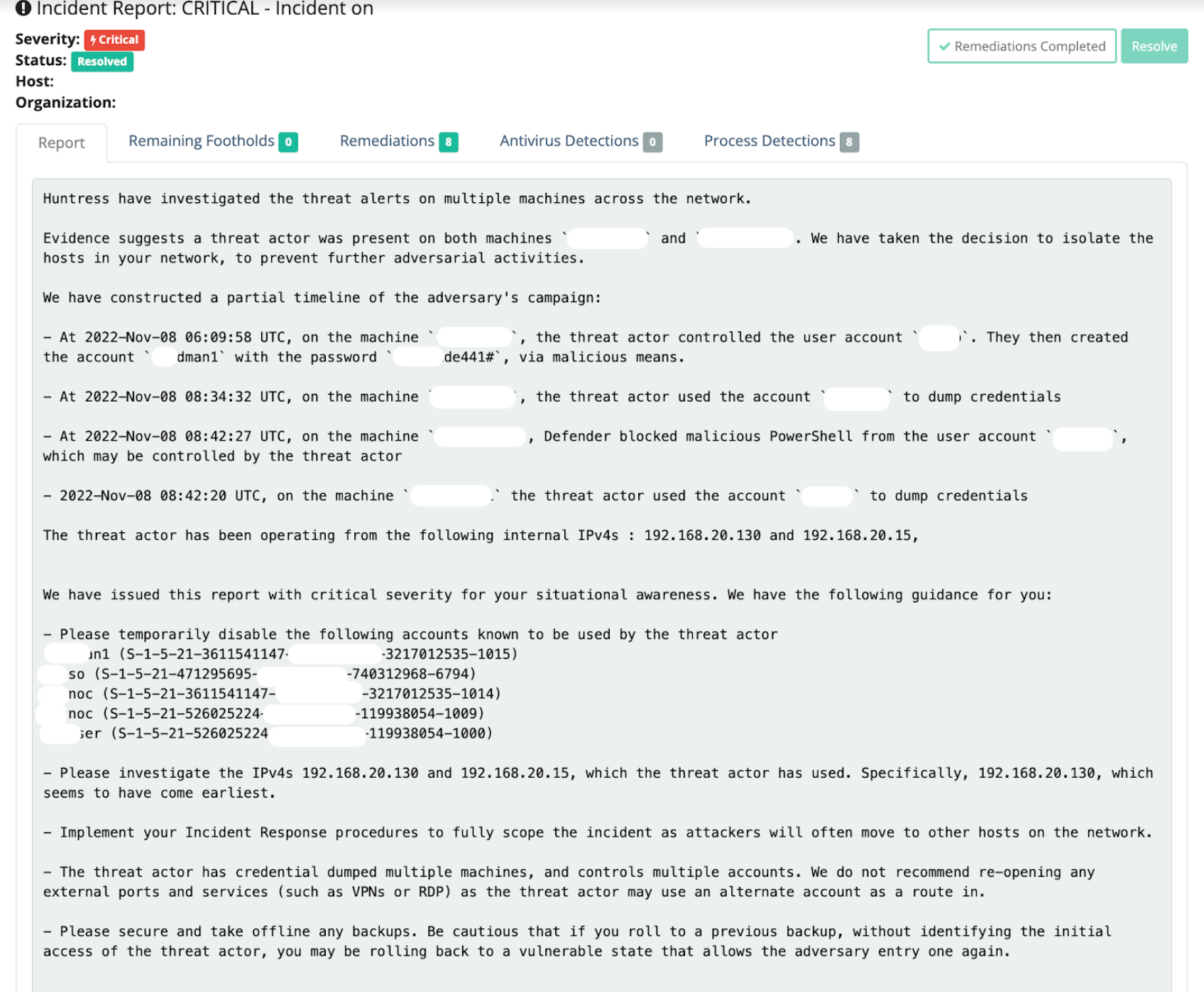
Let’s get specific on the differentiators a Huntress report brings.
After our carefully curated detection logic highlighted suspicious activity to our team, a manual investigation was done to understand how this intrusion came to be. The information gathered was summarized in the report in the simplest of ways. This approach empowers the reader to remediate the infection, recover systems (when needed), and harden their network to prevent a recurrence. And in many intrusions, we’re even able to offer one-click assisted automated remediations—for example, eradicating a persistent cryptominer infection from your host.
And let's not forget our Support team. When reported recommendations or remediations are not working, we have our human support squad who are a web chat away to offer assistance, information, and resources to get the host(s) back into a healthy state.
Now, if all that wasn’t enough, another great point to make about using humans over the AI Overlords—it’s very hard for AI to distinguish between something that actively needs some human interaction and something that is just ‘noise’.
Automated alerts and reports often just work by stating, “I noticed this, looks bad, here’s an info dump, someone should look into it,” or worse, an automated system will respond undesirably on flimsy evidence—for example, an automated system isolating and taking a machine offline erroneously. An overreliance on “intelligent” technologies can increase the speed of response and decrease human cost, but this far too often means sacrificing accuracy and clarity on why an action was suggested/taken.
Whilst Huntress doesn’t pretend to be perfect, we aspire to be as close to perfect as possible. From the development of our EDR technology, to the detections that are conjured, to the alerts that are investigated and reported—human beings at Huntress are leveraging automations but are not beholden to them.
We’re constantly using context and refining evidence to make the best decisions to issue reports and guidance for true positive threats and never inundate our community with needless noise.
Sorry, normally I’m pretty good at starting with a solid tl;dr (too long; didn’t read for anyone that has waited too long and now is just afraid to ask what that means—thank you for that, internet!). However, with this blog, there was way too much great information for me to give the game away at the start, so here we are…
Hopefully, this clears up some of the confusion out there, or if nothing else, illuminates our awesome SOC team even more. If you’re keen to see some of the humans hunting for the insidious and hideous threats at Huntress, give Matt, Anthony, Cat, Dray, or Matthew a follow!
Get insider access to Huntress tradecraft, killer events, and the freshest blog updates.
