







If you missed Tradecraft Tuesday on January 9, you missed out on a banger episode! The tl;dr on what we covered is:
If you’re feeling the FOMO, don’t worry, we got you. Watch the episode on-demand here or keep reading for a recap.
Our January episode of Tradecraft Tuesday was all about remote monitoring and management (RMM) and remote access tool (RAT) abuse and how hackers leverage these platforms to wreak havoc. Max Rogers, Sr. Director of our Security Operations Center, joined me to add his insights on how he’s seen these tools abused time and time again and why RMM abuse can be so difficult to combat at scale.

We started the show with a brief recap of RMMs and their common attributes. Embarrassingly enough, I realized halfway through the presentation that I had forgotten to remove the slides for another presentation, Intro to Command & Control, that I was giving later that week.
Well, as it turned out, it wasn’t a problem at all because the Intro to Command & Control slides fit in quite well alongside the Intro to RMM slides.
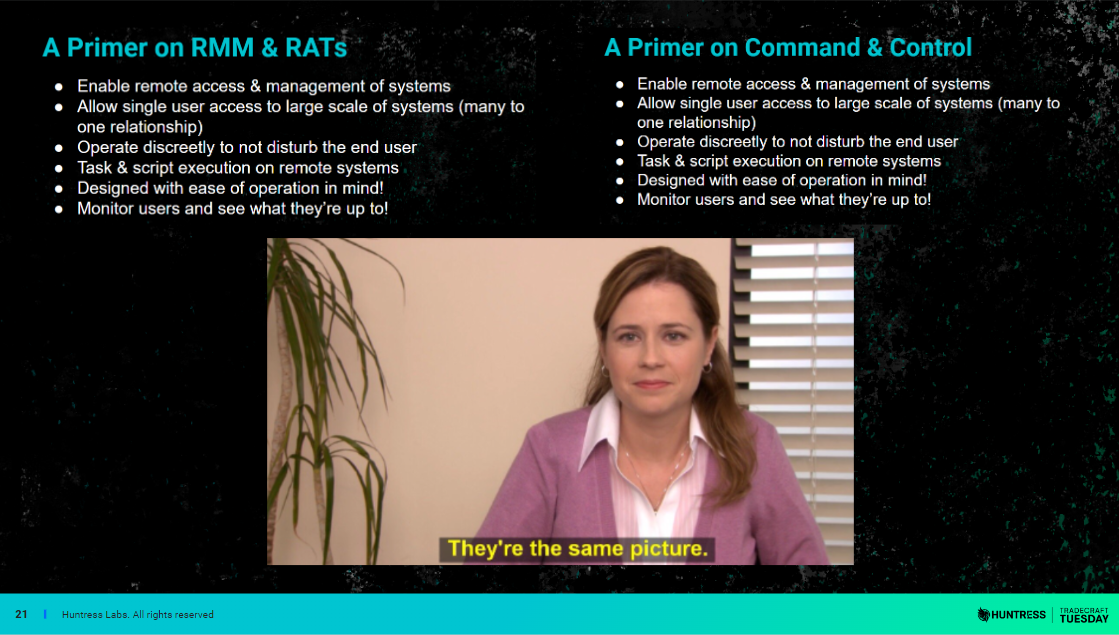
It’s not hard to see why attackers weaponize RMM at an alarming rate given how similar these platforms are to the major command and control frameworks. According to the Huntress SMB Threat Report, about 65% of incidents in Q3 of 2023 included the weaponization of RMM software for persistence or remote access.
In the wrong hands, your RMM platforms give attackers a pre-installed, distributed set of command and control agents that are ready to do their hacker bidding. Scary stuff!
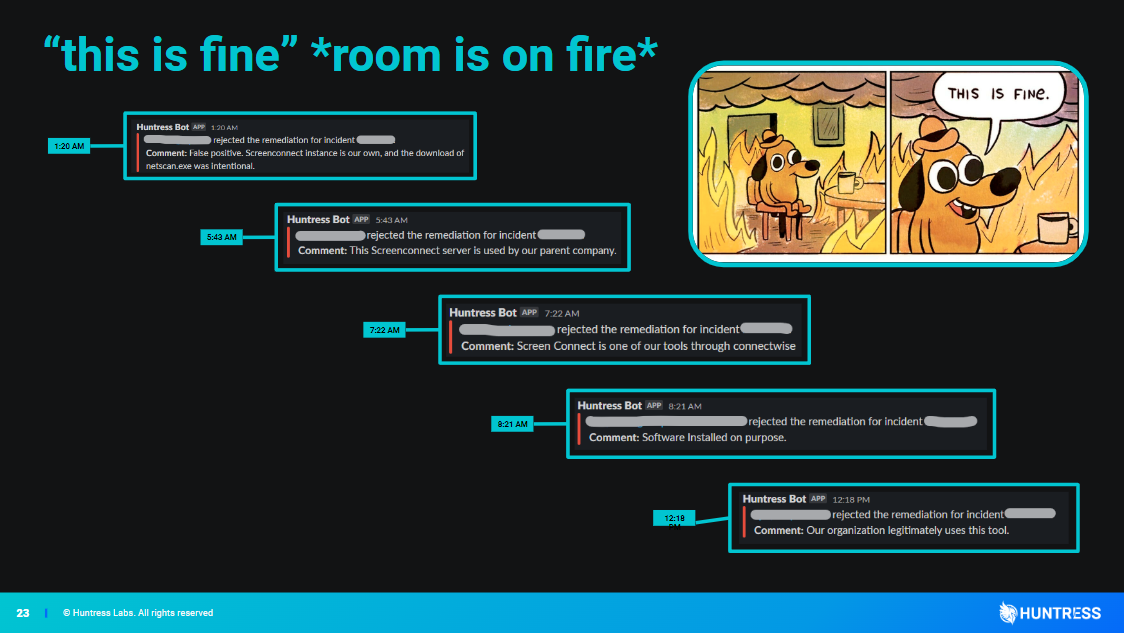
This type of attack is nothing new, though Max remarked that he’s surprised it’s taken this long for RMM and RAT weaponization to become widespread. He offered his battle-tested insights as to why this kind of attack can be particularly hard to detect and deter. He also offered his methodology and tips for hunting down RMM abuse and which network and host indicators you’ll want to pay attention to.
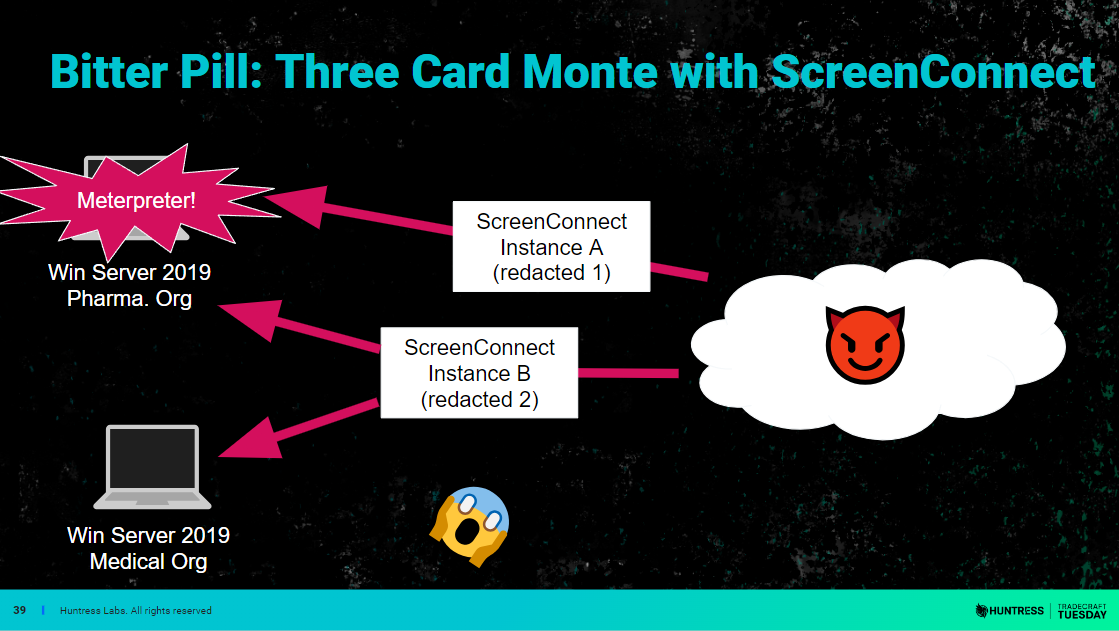
We also spent some time discussing the wackiest and most alarming cases of RAT abuse from recent memory: Bitter Pill, a multi-stage attack against healthcare and pharmaceutical organizations that leveraged ScreenConnect for remote access and persistence. We summarized our blog on the subject, so I recommend reading the blog for the details.
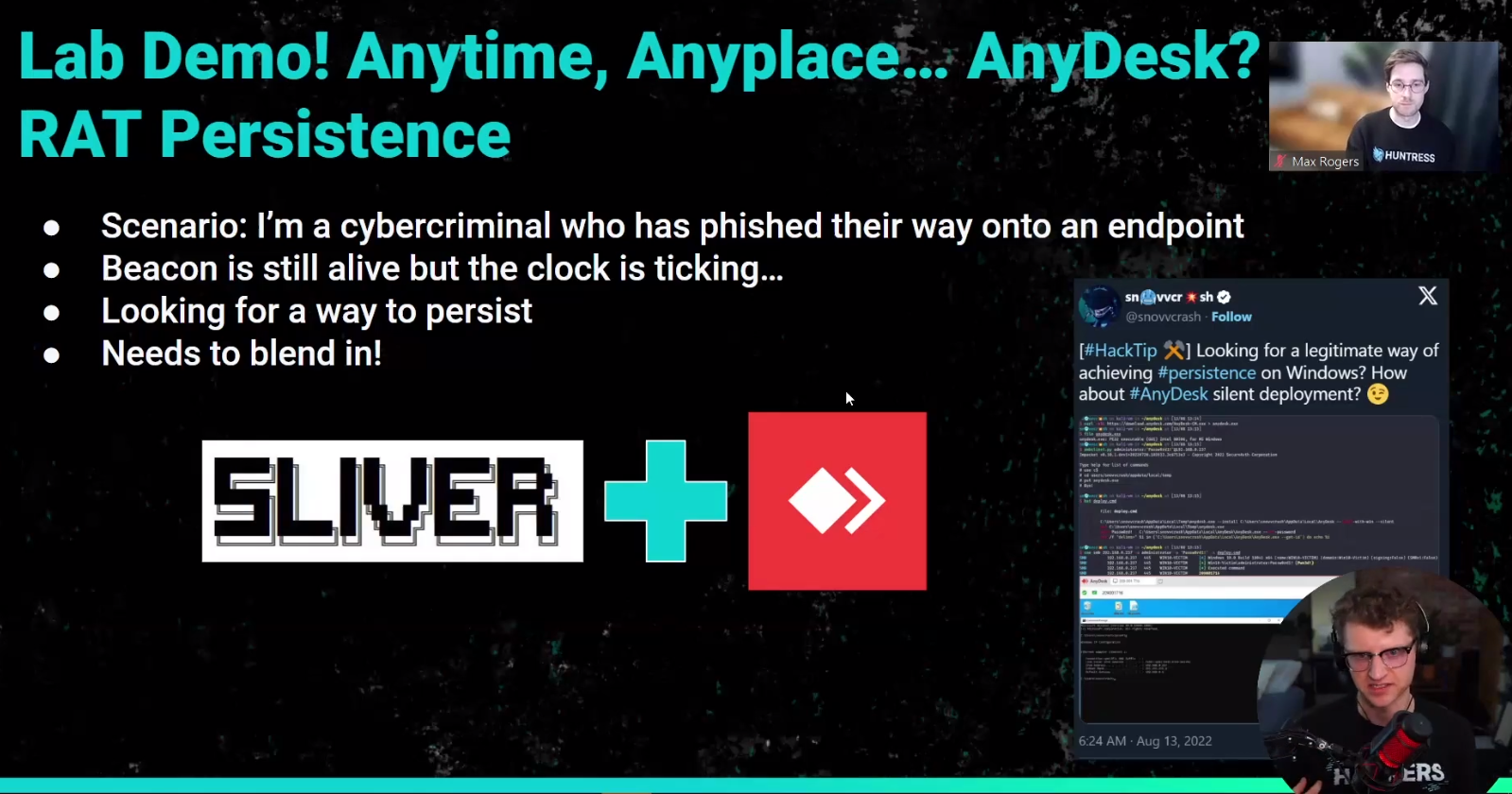
Finally, we put on our hacker hoodies to demonstrate a simple example of persistence using AnyDesk.
Need a way to maintain persistence in your target environment and want to blend in? Consider using AnyDesk with a silent install. I demonstrated how an attacker might silently install AnyDesk from a Sliver C2 beacon to start at boot.
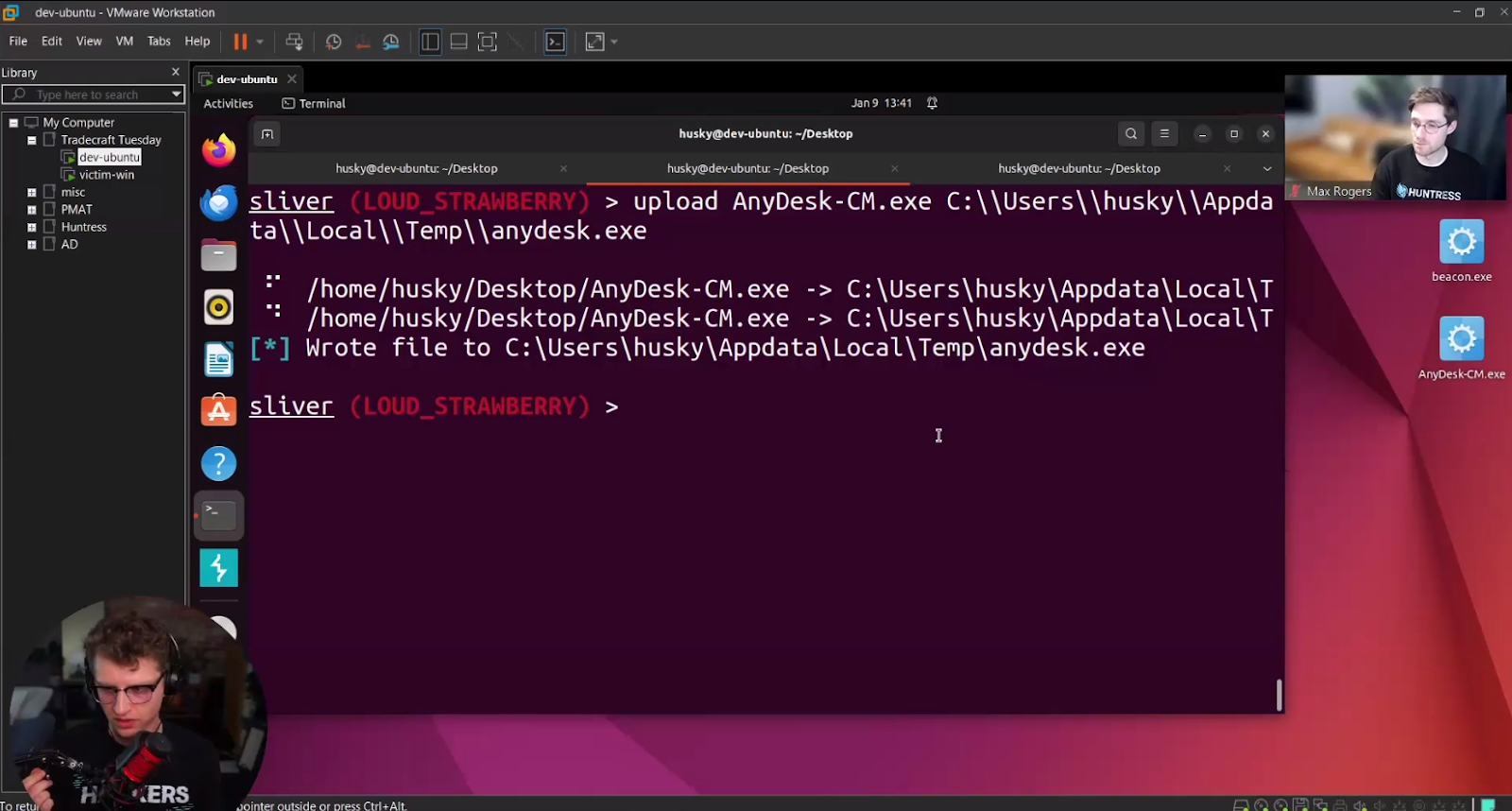
I hope you all had as much fun watching January’s Tradecraft Tuesday as we had hosting it. Any day I get to dust off my Sliver team server and do cool hacker stuff is a good day. We hope the episode highlighted the urgency of protecting your RMMs from falling into the wrong hands and how to hunt down shady RMM abuse in progress.
Remember, you can watch this episode and all of our other Tradecraft Tuesday episodes on-demand. And if all of what you just read sounds like a blast and you want in on the next Tradecraft Tuesday, come through and hang out! It’s free, no boring sales pitches, and the chat is always on fire—register here.
Get insider access to Huntress tradecraft, killer events, and the freshest blog updates.
