







There are many ways to deploy software to macOS, and each comes with its own unique set of benefits and challenges. Outside of manually downloading and installing the software directly on the endpoint, which can be quite tedious outside of a single device, there are two primary methods for managing your macOS fleet: MDM (Mobile Device Management) and RMM (Remote Monitoring and Management).

Let's explore each of these methods in detail, including the differences between them, their pros and cons, and which one may be the best option for your business.
MDM, or Mobile Device Management, is designed to have a central location for administrators to manage your mobile devices. In this case, "mobile," within the macOS ecosystem, refers to laptops like MacBooks, iPads and iPhones, and even Apple TVs. There are several companies that excel in the business of Apple management—names you may have heard of are companies like Jamf, Addigy, Kandji and many others.
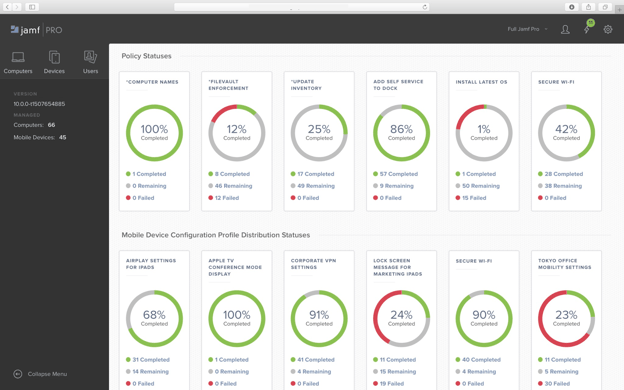
An MDM like Jamf Pro is currently the industry standard, and administrators can build themselves homepages that give them all of the most pertinent information they desire.
If we instead look at Addigy as our test instance, we can see a homepage that provides some great contextual items:our devices, alerts that need to be resolved, and devices that may have some type of security issue.
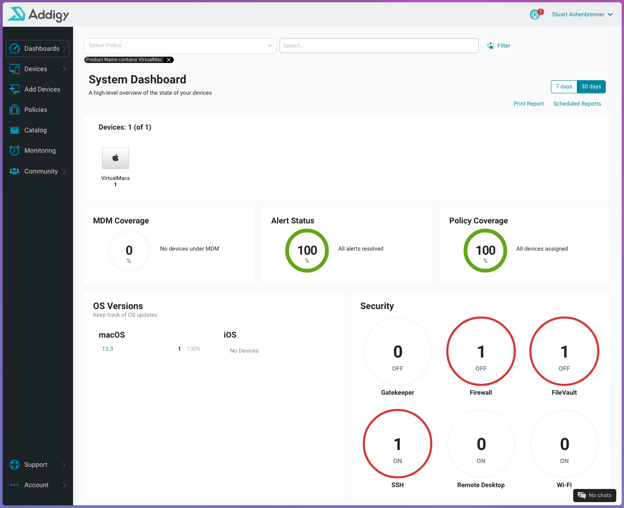
From this dashboard, we can create policies that apply to a specific subset of devices. This allows us to tailor settings based on whose device they’re running on, further giving us the ability to have a large number of devices that can address the needs of each department. For example, a developer may need tools like VSCode, Xcode, or Sublime Text, whereas employees in accounting will likely need Microsoft Excel and not those developer tools. Leveraging an MDM gives administrators the ability to deploy specific software to specific endpoints.
On top of software deployment ease, one of the biggest upsides, in my opinion, is the ability to interact with the TCC database for permissions handling. For a quick overview of TCC (Transparency, Consent and Control), the main concept is to give the end user more control over what their software is attempting to interact with. For example, if Zoom wants to use my camera, I would get a prompt from TCC asking if I approve or decline this request.
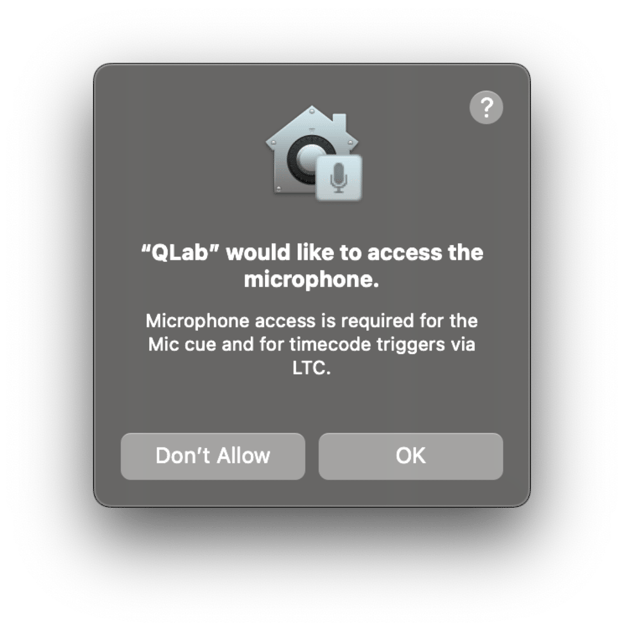
This extends to the microphone, the ability to read and write to home directories, as well as full disk access (writing/reading from any non-SIP-protected directory).
The reason this plays into the decision to roll with an MDM for macOS management as opposed to solely an RMM is the fact that you can deploy policies, via PPPC payloads, to alter permissions to this database. When using the Huntress agent on macOS, it is recommended to grant the application full disk access. When a PPPC payload is deployed—in the form of a .mobileconfig file—it is installed on the endpoint and handles all of those potential permissions issues. For a pre-configured PPPC payload that does just that, see below.
Not only that, but it can be done silently—both installation and PPPC payloads. This has massive implications for ease of use, allowing enterprises to deploy PPPC payload and software, and give that software the permissions it needs without any end-user interaction. To do this with Huntress, we have a knowledge base with some helpful articles for you.
Apple allows the use of MDM to handle this type of behavior for these reasons: to handle permissions, easily deploy applications within your org, keep an updated inventory and plenty of other reasons. On top of this, Apple released Apple Business Manager (ABM). This is Apple’s own MDM software. Using ABM is beneficial to layering your MDM, as this proves to Apple that you (the organization) own that piece of equipment. This can benefit IT administrators when employees leave the organization and potentially take the device with them.
Overall, MDM creates a very strong argument for its use cases, making life much easier for IT professionals, admins and their end users.
RMM, or Remote Monitoring and Management, is software that can be deployed to your Mac fleet that does exactly what its name states—it is designed to remotely manage your devices. While more often used for support-type events, RMM can also be leveraged to help manage software.
RMM solutions are particularly good at giving insights into the happenings on the endpoint itself. Whether it’s CPU usage metrics or even remoting into the machine to help solve issues, RMM gives administrators many different tools for properly managing their devices. This is helpful to many SMBs, who maybe don’t have many Mac devices in their fleet. And although the adoption of Apple devices in the enterprise is steadily rising, Windows still heavily outweighs the total number of deployed endpoints.
Huntress aims to make the deployment of its agent with RMM easier by providing scripts in order to deploy in a quick, concise manner. We also have multiple knowledge base articles to help you expedite this process.
While MDM and RMM are both great ways to manage macOS devices, each has its own strengths and weaknesses. What MDM lacks, RMM generally excels at, and vice versa. When supporting macOS, the answer is that, ideally, you want both of these solutions. This is especially true as the adoption of Apple devices in the enterprise becomes more and more prevalent.
I don’t want to speak for someone and declare one over the other, as it depends on what suits your needs best and where the pricing most matches your budget. However, I’d be remiss not to mention the struggle of properly deploying software, to macOS in particular, only using an RMM. In macOS Ventura, Apple once again reaffirmed their security posture in giving the end user an unprecedented look into the happenings on their system—whether it be TCC prompts, requiring admin privileges in order to install/uninstall system extensions, or even the newer Notification Center alerts regarding the addition of new Launch Items (Launch Daemons and Launch Agents).
In many ways, this makes the use of MDM much more simple from strictly a software management and deployment perspective, however, it is impossible to ignore the price, which is often at least 2-3x more expensive per endpoint than RMM.
By understanding the differences between these two methods, you can make an informed decision on which one to use for your macOS management needs. And in the end, what matters most is that your tools are doing the job you need to keep your endpoints safe and secure.
Get insider access to Huntress tradecraft, killer events, and the freshest blog updates.
