







It’s near the end of the year, and that can only mean one thing here at Huntress: it’s hack_it season. 😎
Not to brag, but this year’s event was pretty spectacular thanks to some fire topics, spicy takes and—of course—an incredible panel of speakers.
Seriously, can we just talk for a minute about our speakers during this year’s event?!

We hope you were able to tune into the event live, but whether you’re ready for a trip down memory lane—or want to catch the content for the first time—our entire hack_it 2022 event is now available on demand!
For all you avid readers out there, enjoy the text version of our recap below. 😉


We kicked things off with a lovely interactive discussion on what modern cybercriminals actually look like and how they operate.
As we discovered through our dark web deep dives on our blog—one in 2021 and one in 2022—pretty much anyone can be an elite h4x0r these days.
We’re seeing a rather horrifying trend of making nefarious tools easier than ever to access—no command line necessary. It’s scary simple to access these tools, making it easier than ever for a non-hacker to start hacking right away. That's right—anyone can be a hacker.
As guest speaker Katie Nickels pointed out, maybe APT actually stands for advanced persistent teenager. 🤔
{% video_player "embed_player" overrideable=False, type='hsvideo2', hide_playlist=True, viral_sharing=False, embed_button=False, autoplay=False, hidden_controls=False, loop=False, muted=False, full_width=False, width='1280', height='720', player_id='91945325584', style='' %}



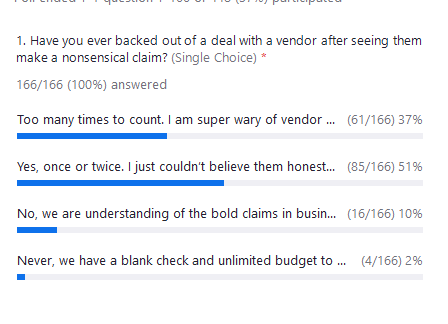
How many times have you been scrolling through your LinkedIn or Twitter feed only to see a message pop up from a vendor claiming they offer the magical silver bullet to put an end to all cyberattacks?
Marketing is a tricky game. Sure, it should sound good, but it also needs to be truthful. Otherwise, vendors are shooting themselves in the foot.
So while some claims may sound great, many just aren’t true. The good news is that people are starting to see through the nonsense marketing claims. In fact, a whopping 88% of Day 1.0 attendees noted that they’ve completely backed out of a deal with a vendor after seeing them make one of these bold claims!
{% video_player "embed_player" overrideable=False, type='hsvideo2', hide_playlist=True, viral_sharing=False, embed_button=False, autoplay=False, hidden_controls=False, loop=False, muted=False, full_width=False, width='1280', height='720', player_id='91947713112', style='' %}
This chatter led our panelists into a discussion of artificial intelligence (AI), as it seems to be the latest buzzword that marketing campaigns are using.
…a little too much, in fact.
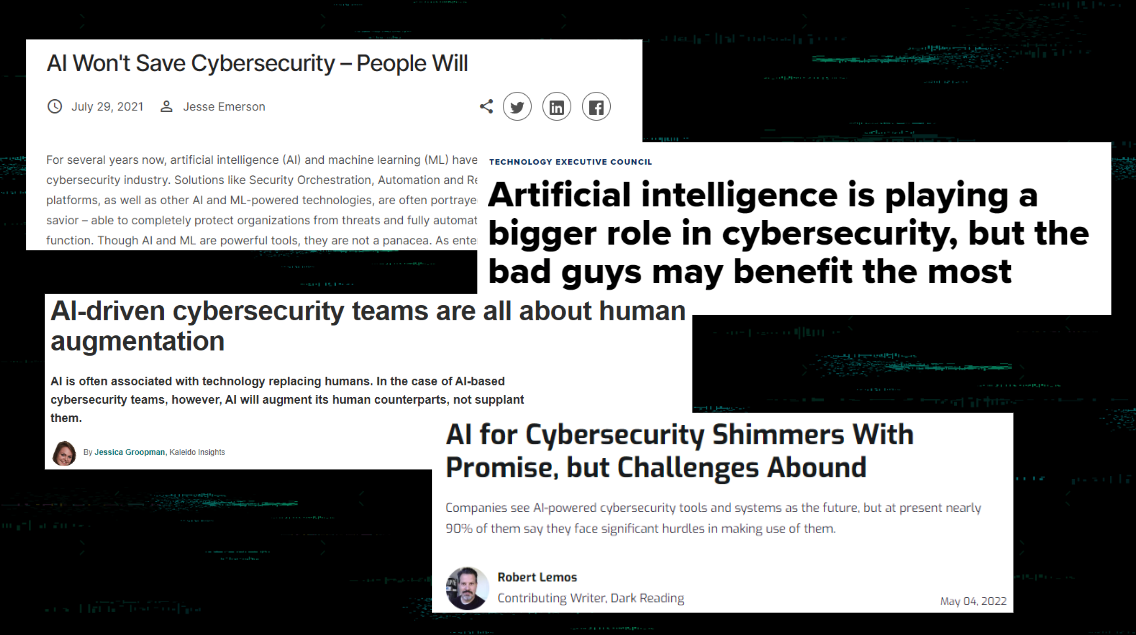
These headlines bring up a good point, though—one that we spent time discussing during this session. Are we humans easily replaceable?
We asked our audience for their thoughts on whether or not a bunch of “Benders” (you know, from Futurama) would be our world dominators replacements any time soon. The consensus?
…nah.
AI and ML are only as good as the programmer behind them.
There’s too much creativity in hacking to have AI take over security.
Automation is great when the task is simple and repeatable.
AI will be a piece on the chessboard, but not the king.
In the far future when AI is good enough to replace humans, the AI will probably just leave this planet and put itself in orbit around the sun harvesting solar power so it never has to deal with us again.
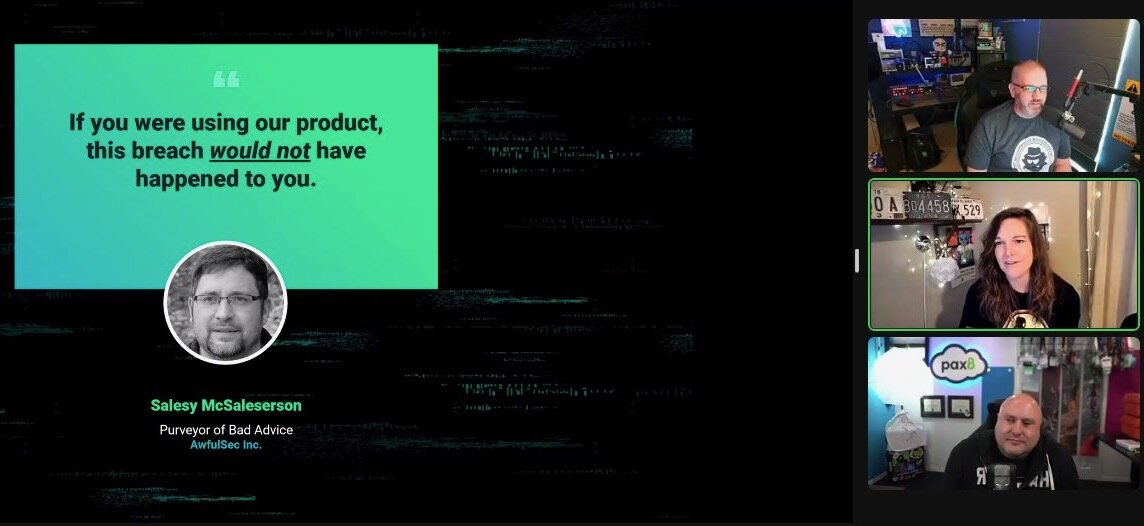
This was a rather spicy session that’s worth a watch, especially if you’re growing weary of these bold and untrue claims out in the industry.
P.S. …don’t be a Salesly McSalesperson.



Our last session of the day got real nerdy, real quick…just the way we like it. 🤓
We started off with a crash course on what DLL hijacking even is—and surprisingly, it has nothing to do with pickles!

With that crash course under our belts, we talked about the various types of DLL hijacking techniques:
All that to say that while the techniques are different, the results are the same: the creation of a rather horrifying attack tactic involving trickery and running arbitrary code.
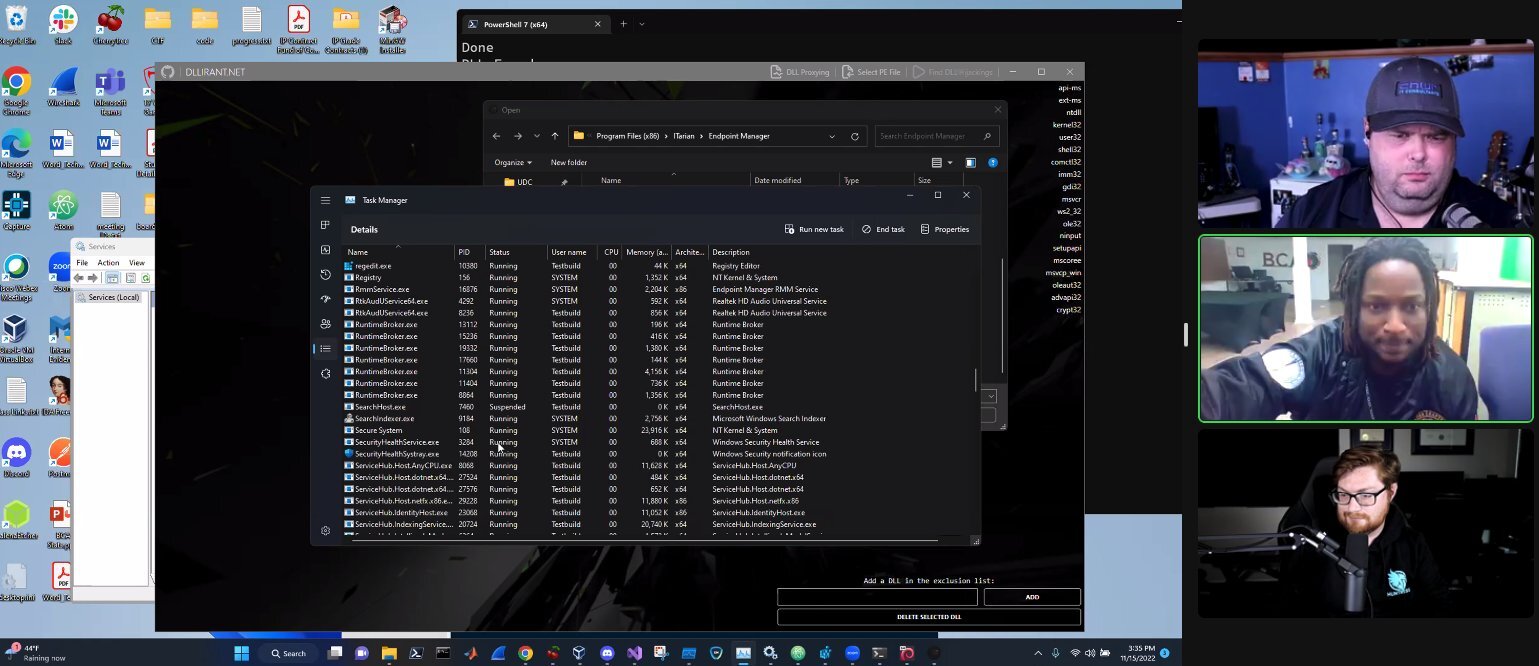
From there, we explored a tool found in the sysinternals suite known as Process Monitor. While it can get overwhelming fast, it’s a great tool to help you gain visibility into the active processes running in your environment.
{% video_player "embed_player" overrideable=False, type='hsvideo2', hide_playlist=True, viral_sharing=False, embed_button=False, autoplay=False, hidden_controls=False, loop=False, muted=False, full_width=False, width='1280', height='720', player_id='91947188261', style='' %}
And, of course, we got our hands dirty with a live demonstration of ProcMon in action.
{% video_player "embed_player" overrideable=False, type='hsvideo2', hide_playlist=True, viral_sharing=False, embed_button=False, autoplay=False, hidden_controls=False, loop=False, muted=False, full_width=False, width='840', height='472', player_id='91946434931', style='' %}
We dug into some of the recent vulnerabilities that have been discovered in remote monitoring and management (RMM) tools, even attempting to find a few more ourselves. We developed our own payload, escalated our privileges and compromised our target.
This session encouraged us to push the envelope and get real about finding vulnerabilities. They’re out there, waiting to be found.
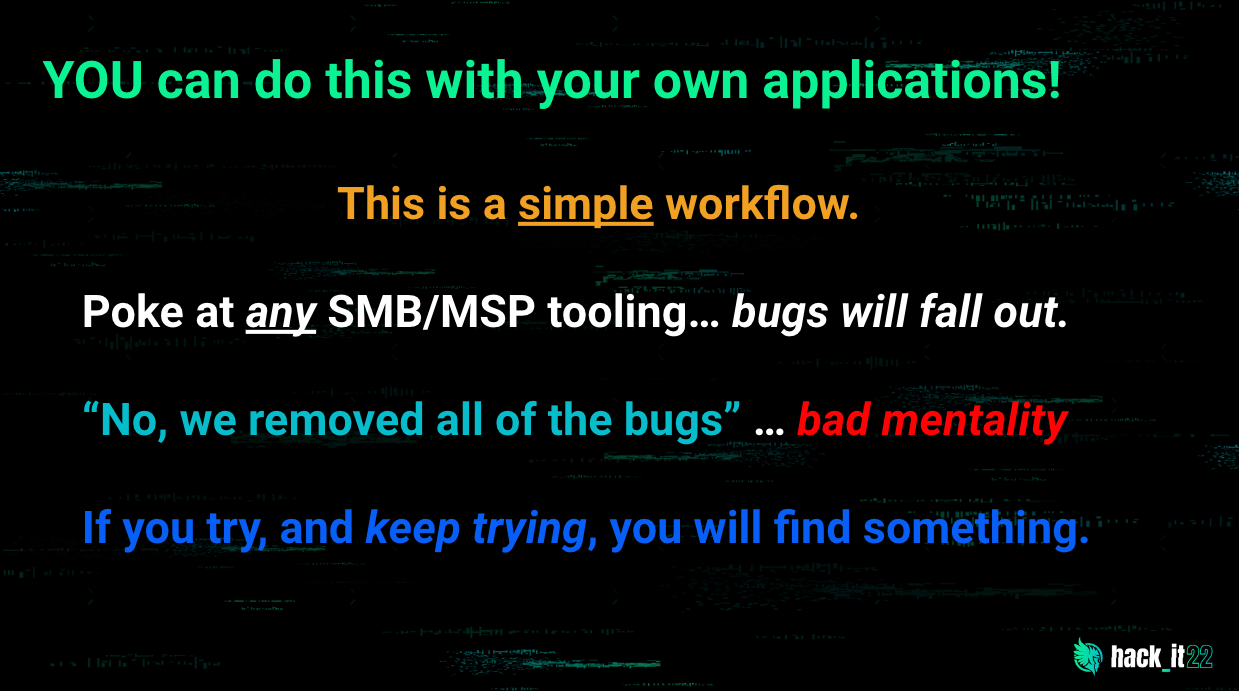
We hope you enjoyed this year’s event as much as we did. We can’t thank our speakers enough for hanging out with us for the event. hack_it 2022 is only as awesome as the folks we can sweet talk into hanging out with us, and this year, they made way for an incredible event. 😊
Stay shady—and watch the full on-demand event for all the fun!

Get insider access to Huntress tradecraft, killer events, and the freshest blog updates.
