







How do security teams know exactly what malware is doing and how to stop it?
In a recent episode of Tradecraft Tuesday, I was joined by Principal Security Researcher Caleb Stewart to dive into the thought process behind reverse engineering malware and the value it brings.

Understanding how malware functions is critical to developing a stronger security posture. Not only does it aid in improving defense measures by learning how malware behaves, but it can also give valuable intel into how threat actors use malware to operate. A real-world example of this is shown in our recent blog about Qakbot when Huntress discovered how to stop it during its execution.
Let’s dive into the basics behind reverse engineering malware and how you can get started.
It’s dangerous in the wild wild web, and detonating malware with no preparation or regard for safety can have disastrous consequences. Instead, you should carefully craft a secure, isolated environment for your malware analysis.
Below are some simple steps you can take to ensure that you are as prepared as possible for your analysis.

There are countless reverse engineering tools available, but here’s a few we recommend:
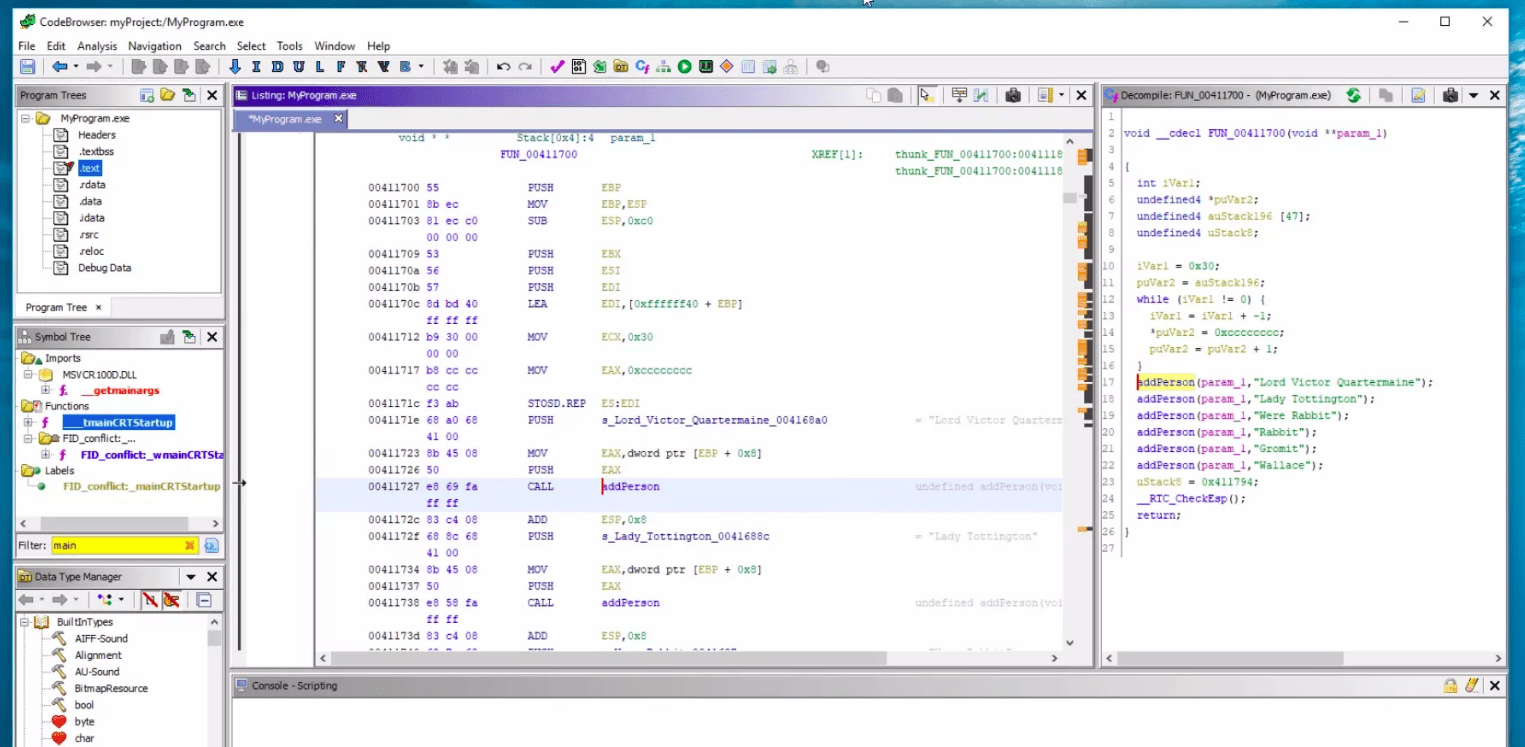
The most commonly used disassemblers are Ghidra and IDA Pro. These handy tools read the machine code of a program and attempt to translate the instructions into a higher-level programming language of your choice. The better disassemblers provide features like control flow analysis that will guide you through the steps the malware is taking and prevent you from jumping all around on your own.
Dynamic debuggers have similar functionality as a developer's integrated development environment. They allow you to execute the program and pause throughout at your will to inspect the state and see variable values or other useful information. Generally, sticking with Ghidra or IDA Pro is a good choice since they have the capability to do both disassembly and dynamic debugging.
Sometimes you'll run into challenges when attempting to understand what the source code is doing, like when a program is written in Golang, which hampers most disassemblers because it’s not built on top of the C programming language. Fortunately, there are other options for dynamic evaluation of a piece of malware:
Hackers don’t want to make it easy for us to understand their code. The less investigation, the better for them. You’re likely to find a few techniques used to prevent pesky reverse engineers from discovering the secrets of their source of income, including:
Reverse engineering isn’t as simple as just throwing tools on a box and detonating your malware. It is a methodical approach.

You need to identify the malware and determine what type of analysis will work best. Then, look for the first thing the malware does when execution starts. You will encounter unexpected challenges along the way, and you will need critical thinking and rapid problem-solving skills to help work your way through the nuances of each sample. Just like all aspects of cybersecurity, mastering reverse engineering requires time and discipline. It can take hundreds of repetitions to learn how to differentiate from what is normal or not, but by utilizing safe practices and having a little patience, you can get there!
Get insider access to Huntress tradecraft, killer events, and the freshest blog updates.
