







EDR, MDR, XDR…oh my. The number of acronyms in the cybersecurity industry could make for a nicely seasoned alphabet soup. The last thing we need is another one, right? Wrong! As I read once in a Reddit thread: “An acronym a day keeps hackers away.” Yes, poster, well put.
Call it a security solution, a product category, a cybersecurity approach, or an analyst buzzphrase—identity threat detection and response (ITDR) is the latest acronym you can’t escape. And you won’t want to.
First introduced by Gartner in a 2022 press release and later featured in its Hype Cycle for Endpoint Security, 2023, ITDR was developed “to describe the collection of tools and best practices to defend identity systems.” Since then, digital identities have become even more ubiquitous in our everyday lives. The ITDR market, projected to grow from $12.8 billion this year to $35.6 billion in 2029, has appropriately followed suit. Today, ITDR as a cybersecurity category has evolved to more broadly describe solutions focused on protecting identities and credentials and responding to identity-related attacks.
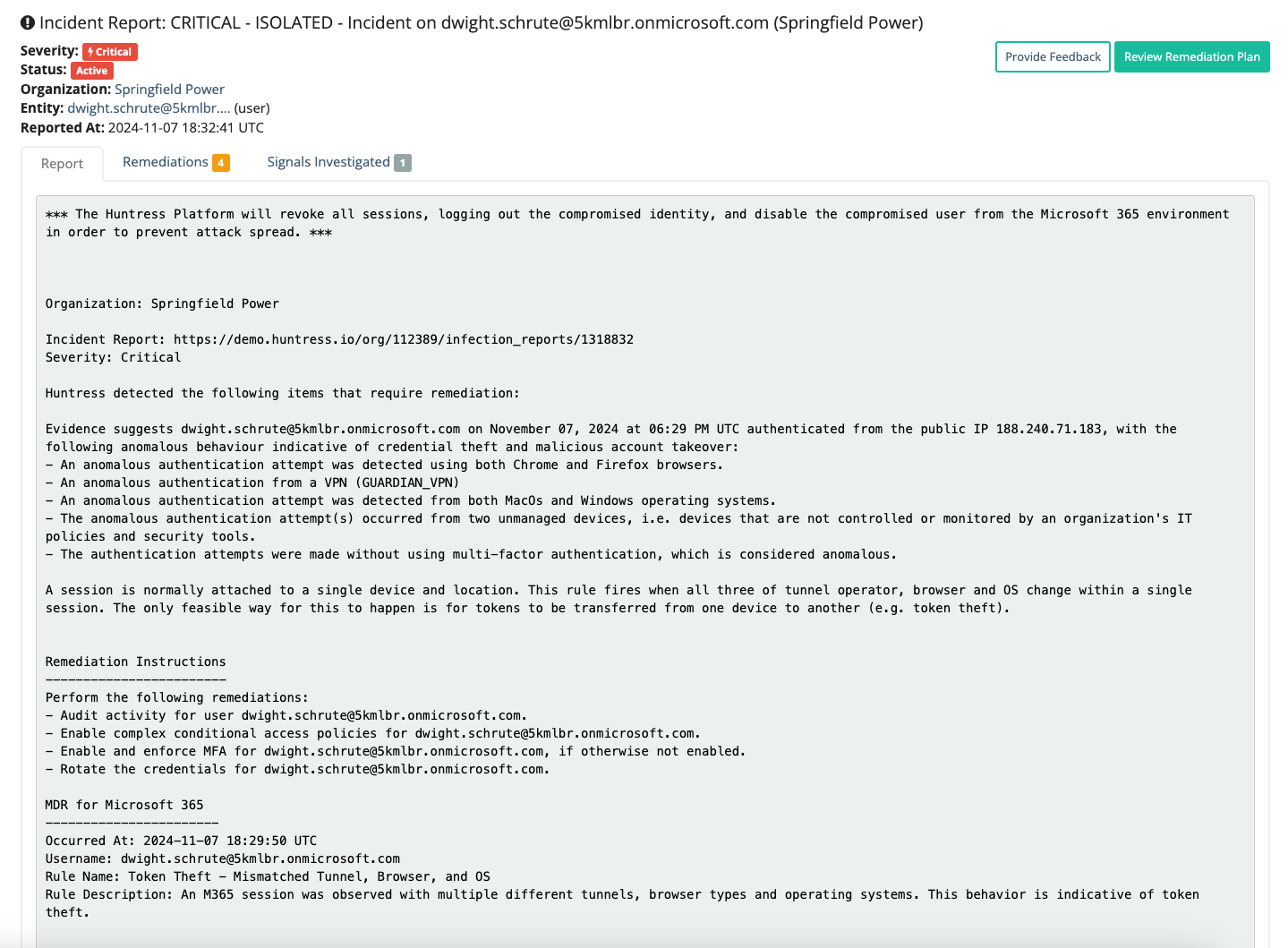
But, WTF (..and that’s frick, folks. Get your mind out of the gutter) is ITDR? Imagine a watchtower constantly scanning for unauthorized access, misuse of credentials, and any sneaky behavior that could put your business at risk. ITDR doesn’t just monitor—it identifies threats in real-time and takes swift action to neutralize them.
Think of it this way: while traditional security solutions focus on keeping the bad guys out, ITDR ensures that even if they manage to sneak in, they don’t get far. It’s about protecting what matters most—your people, their access, and, ultimately, your bottom line.

As businesses continue to move to the cloud, they’re juggling a complicated mix of on-prem infrastructure, cloud apps, and remote workspaces, creating a tangled web of interconnected systems. The result? A bigger attack surface and more entry points for bad actors. According to the 2024 Verizon Data Breach Investigation Report, stolen credentials—a common identity vector—have appeared in almost one-third (31%) of breaches over the past 10 years. The Huntress Security Operations Center (SOC) alone detects more than 2,000 suspected credential attacks every week.
All it takes is one set of valid employee credentials for an attacker to waltz into your business, snoop around, escalate their access, and cause havoc. Whether they're locking you out, shutting down services, wiping out data, or nuking resources—it’s game over.
ITDR involves monitoring, identifying, and mitigating threats related to unauthorized access and misuse of identity credentials within an organization. This includes using both human and technological measures to detect anomalies and respond effectively to potential security incidents, ensuring the protection and integrity of identity systems and data.
While there can be different flavors of ITDR (pre-compromise vs. post-compromise), ITDR solutions usually have the following key aspects:
In short, everyone.
No organization is safe from identity-based attacks. With attack surfaces spread across multiple locations, accounts, and devices, all it takes is one person, one compromised credential, or one weak app for hackers to bust through the doors and wreak havoc on your entire digital infrastructure.
That’s why ITDR has become a must-have in any solid cybersecurity game plan for all organizations—regardless of size or industry. Because identities have become the primary targets of attackers looking to gain unauthorized access to sensitive systems and information, organizations can employ an ITDR solution to protect themselves from identity-related threat vectors like session hijacking, credential theft, account takeover, and business email compromise (BEC).
ITDR solutions come in many flavors—and finding the right flavor depends largely on the security maturity of your organization. Some factors to consider:
Wait, Huntress has an ITDR solution? Heck yeah, we do! What you might’ve known as MDR for Microsoft 365 just got a major upgrade and a new name—Huntress Managed ITDR. We’ve added Unwanted Access, a slick new capability that helps you outsmart hackers by shutting down their go-to moves like session hijacking and credential theft. Oh, and by the way, we’ve crossed the milestone of protecting over a million identities (and we’re just getting started).
Our new ITDR category isn’t just a shiny label—it’s a clearer reflection of where we are and where we’re heading. Stay tuned, because there’s a lot more to come. 🚀
Get insider access to Huntress tradecraft, killer events, and the freshest blog updates.
