

























Welcome to your go-to destination for cybersecurity resources and education. Dig in and find a range of materials made to empower users of all levels with the knowledge and tools to defend against evolving cyber threats.



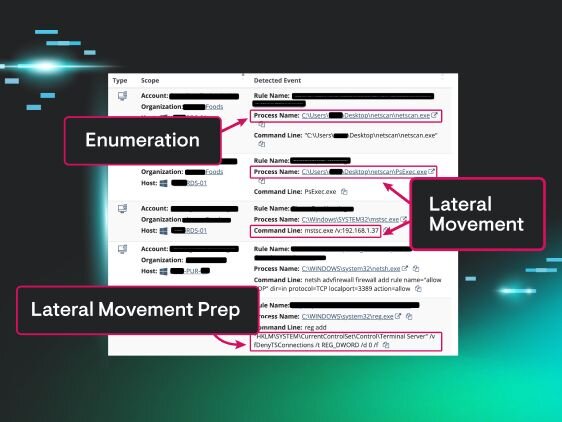
They Want Credentials, Control, and Chaos. We Shut Them Down.
Before Ransomware Strikes: Attack Playbook
From Curricula to Huntress: The Past, Present, and Future of Managed SAT

The Huntress Product Showcase: Q2 2025
2025 Cyber Threat Report for Technology
2025 Cyber Threat Report for Government
2025 Cyber Threat Report for Education
2025 Cyber Threat Report for Healthcare
2025 Cyber Threat Report for Manufacturing
Top 5 Identity Threats You Can’t Afford to Ignore

Transforming Your Approach as a Technology Solutions Partner
The Straightforward Buyer’s Guide to EDR
What is ITDR?
Stealthware: The Rise of Malicious OAuth Apps in Microsoft 365
Traitorware: How Hackers Abuse Legitimate Apps to Hijack Microsoft 365



Book a personalized demo to look at Huntress under the hood, explore the dashboard, and ask questions to our experts.
