







Protecting your business from growing cyber threats is never a one-and-done task. Threat actors are always looking for new tactics to accomplish their goals, and account takeover (ATO) can be very profitable for them.
ATO happens when a threat actor gains unauthorized access to a user’s account credentials and takes over the account to commit malicious activity, such as fraud or data theft.
Your usernames and passwords are essential to protecting your business’ data and online accounts. But when they get into the hands of bad actors, stolen credentials allow attackers to gain unauthorized account access—that’s what’s known as an account takeover attack.
Account credentials can be purchased off the dark web or acquired through social engineering, data breaches, and phishing campaigns. Attackers can even deploy bots that automatically test password and username combinations on sites known to contain personal, customer, or business data. And once in, they can carry out other nefarious activities.
If you’ve ever received an email from a “friend” that just didn’t seem right or sounded a little off, maybe asking you to reply to an odd request or to click on a link, you’ve probably come into contact with an account takeover scheme.
Account takeover attacks are designed to allow cybercriminals to gain unauthorized access to a victim's online account and steal information—like financial account details or personally identifiable information (PII)—or make unauthorized purchases. And ATOs are occurring more frequently.
For example, 2023 saw a 354% year-over-year increase in account takeover attacks. Whatever form they take, ATOs pose significant risks to businesses like yours, including financial losses, data breaches, and reputational damage, putting customers, clients, and executives at risk.
It doesn’t matter your size, location, or industry. Once cybercriminals have access to account credentials, they’re in control—stealing personal, corporate, or financial information. Even AARP reported on the problem, stating that in 2023 ATO fraud resulted in nearly $13 billion in losses.
Bad actors gamble on finding easy targets. For them, it’s a little like playing the roulette wheel in Vegas. With enough spins, cybercriminals hit paydirt.
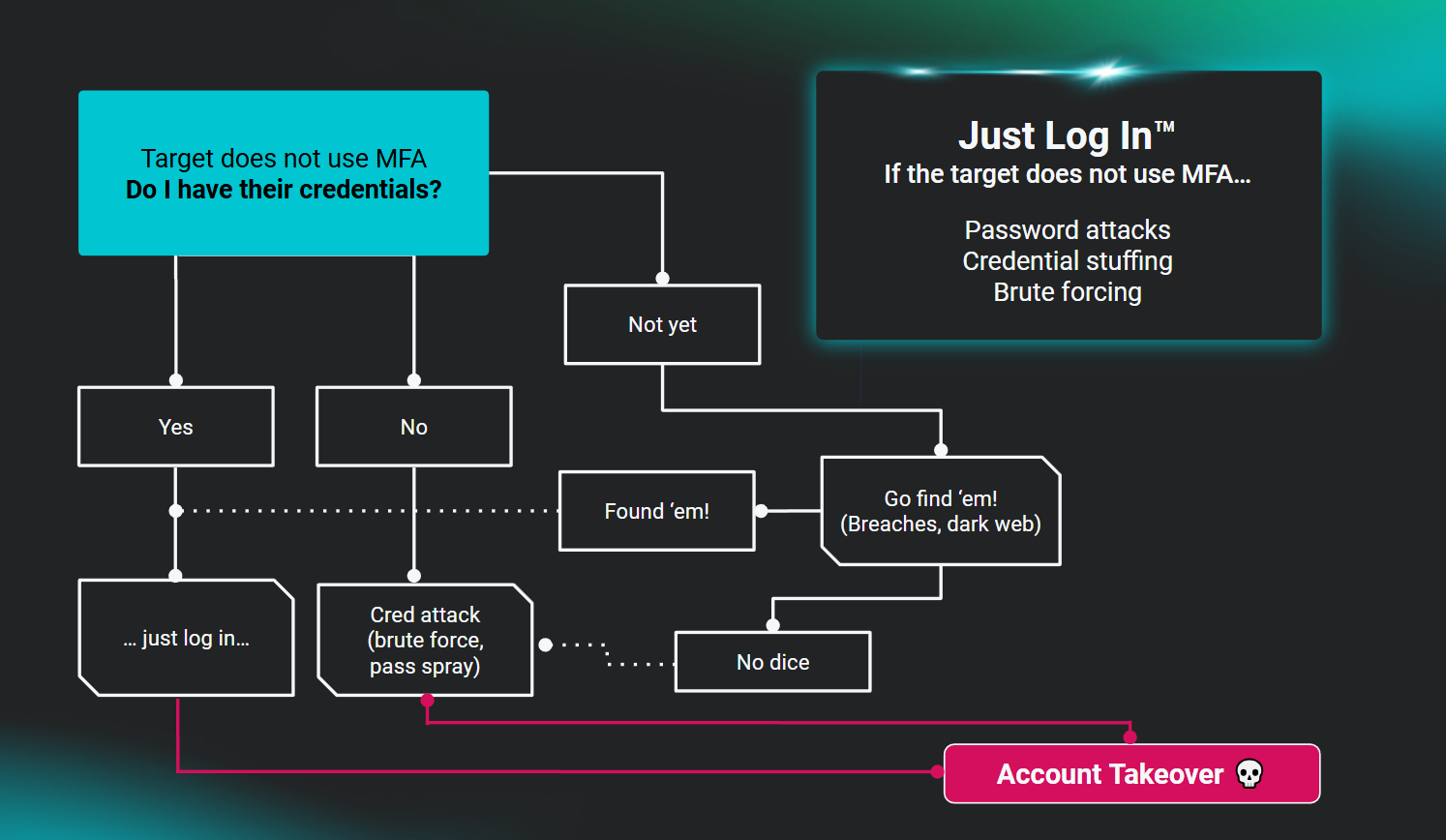
An ATO typically begins with some form of credential theft. And once they’re in, that’s when exploitation happens. They can siphon funds, steal personal data, dump malware, or carry out further attacks using the compromised account. Attackers can easily infiltrate your organization’s email system or network, or access sensitive data like confidential customer information. When they have control of one account, it’s easier to launch more attacks using these methods:
Account takeover fraud can lead to loss of customers, business, reputation, and money. Potential consequences include:
Account takeover is a growing concern for businesses and individuals. However, using a combination of best practices, businesses can detect ATO fraud and take action to prevent further damage. Malicious hackers are actually quite lazy, so the more access barriers you build around your known security attack surface, the greater the chance they're going to look elsewhere for an easier target.
Let’s start with the first thing to do. Change passwords frequently and don’t reuse them. Though it's recommended to regularly modify passwords and use unique credentials for all accounts, users often overlook these basic security hygiene best practices. For over 56% of ATO victims, the same password of the affected account was used on their other accounts, putting those accounts at risk. Strong password policies make it difficult for attackers to guess or use other ways of obtaining individual system accounts. Use strong and unique passwords for each account. Avoid reusing previously used passwords or their variants since these might already be compromised.
Set up multi-factor authentication (MFA). It’s one of the most effective ways to prevent ATO. Requiring multiple forms of authentication, such as a password and a fingerprint, facial recognition scan, or authenticator application, makes it more difficult for attackers to gain access to accounts.
Your employees are key to building and maintaining a resilient security posture and protecting your business from ATO. Establishing regular security training and awareness programs help educate your employees about the risks of ATO, and how to identify potential threats. Security awareness training equips users with the knowledge to recognize phishing attempts and stop credential theft that could lead to ATO.
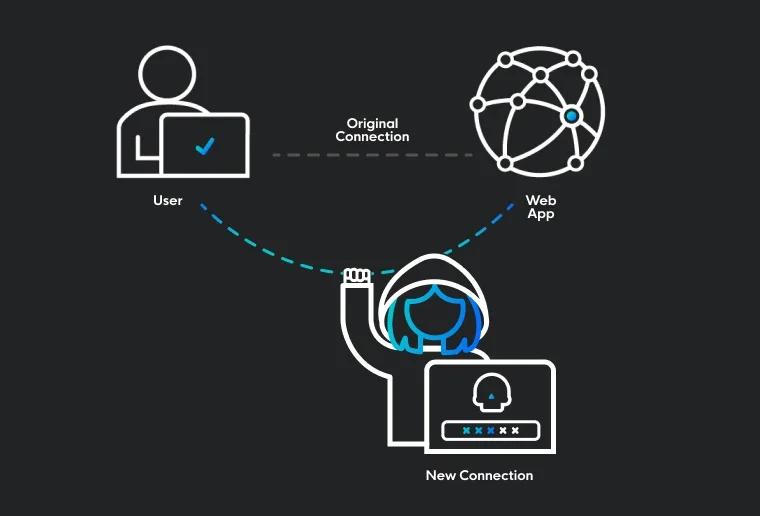
Identity threats have become the new attack perimeter, leaving organizations vulnerable to account takeover. Whether it’s unwanted logins, session hijacking, credential theft, or malicious inbox rules, continuous monitoring makes it harder for intruders to exploit your systems through unauthorized access, misuse, or theft of digital identities.
Real-time and continuous monitoring of your organization’s account activity helps you identify potential ATO fraud and take action to prevent further damage by:
Endpoint security or identity-management tools are no longer just for big enterprises. Bad actors are looking for any opportunity regardless of size. As attacks from multiple sources have increased, these solutions protect your business from cyber threats like ATO. Securing your endpoints is as important as using strong passwords and setting up MFA. When alerts are automatically monitored, detected, identified, and remediated, attackers are stopped before they can get a foothold.
ATO is a growing threat, but you don’t have to tackle it alone. An identity threat detection and response (ITDR) solution can significantly reduce your risk and protect your business from malicious hackers.
Huntress Managed ITDR makes it simpler to secure your identities and safeguard your environment. Learn how we can help keep your business safe—schedule your demo today.
Get insider access to Huntress tradecraft, killer events, and the freshest blog updates.
