







As a managed service provider (MSP), you’re the backbone of your customer’s cyber infrastructure.
Your team knows what it takes to run operations smoothly: a constant flow of new tools, software updates, an ever-expanding knowledge base and an ever-growing support staff.
You’re always ready to jump in and help when something goes wrong. You’re not just an advisor—you’re a problem solver.
But a chain is only as strong as its weakest link.
What happens when your client uses remote access software they mysteriously found?
Annnnd somehow, there’s no antivirus installed yet on their system. (It’s a scary thought, isn’t it?)
These seem like easy mistakes to avoid, but these programs can be tricky to avoid if you aren’t familiar with how they work or how to identify them.
It won't matter how well-trained your team works…
Or how much time they put into their customer’s systems…
If you don't have a strong security foundation in place, your customers will suffer from downtime and revenue loss that affects their success. No amount of overtime will make up for the lost billable hours.
You can’t just work harder. You have to work smarter.
You have to take care of yourself before you take care of others. That’s why we consolidated some of the best daily practices for IT providers and customers during our Back to Basics Security webinar.
Jerrel Howland, CTO of Mytech Partners, encourages you to start now rather than later. This means keeping up with the latest security trends, researching ways to maintain and creating a culture that promotes security awareness among your employees and clients.
Jan Broucinek, Security Operations Manager at Network People, suggests starting with server security. Are you applying patches? Is AV running on the servers? The easiest way to prevent a breach is to lock down the basics.
Tim Weber, VP of Channel Growth at Cyber 74, reassures you that you don’t reinvent the wheel and start all over. Don’t let perfect be the enemy of creating something good. To be great at something, you need to practice.
Cybersecurity constantly evolves; no single approach will protect you from every threat. That said, there are basic steps you can take today to build a strong foundation for your cybersecurity hygiene.
The good news is that you can follow them quickly and easily.
Time and money are intertwined when it comes to building an onboarding experience. And you don’t want to waste either with time-consuming and expensive onboarding fixes.
Your onboarding process should be personal and seamless, built for your client’s immediate needs. You might miss things your client needs later if you don’t ask the right questions.
There are many moving parts to onboarding; you can depend on documentation to help you keep a consistent process. It’s hard to remember every tiny detail, especially regarding complex technical requirements.
Use your documentation instead of relying on your memory. It can be the difference between a smooth onboarding experience and getting stuck in the weeds.
Don’t wait to set up your security platform until the time is right. The best time to start planning your security strategy is while the threats are still theoretical. With security breaches on the rise, it’s time to stop waiting for a mythical time to start setting up your client’s systems.
Security log monitoring and analysis is a never-ending process requiring full-time, dedicated resources. Try manually checking Windows security logs for an hour… it’s impossible. You HAVE to have automation in place.
When something breaks, you need automated, actionable alerts.
Proactively collecting information from all agents and systems creates an accurate picture of what is happening.
In the realm of cybersecurity, no news is not good news.
No news means it’s broken.
The cybersecurity experts are here to help… but whose job is it, anyway?
Cybersecurity is one of the most pressing challenges organizations are grappling with today, given the rise of remote work. Security goes beyond a server—it impacts business continuity, branding reputation and financial performance.
Every team member plays a critical role in keeping an organization secure.
Security is more than just a technical discussion; it’s about resilience and risk management. Everyone needs to understand the threat landscape, recognize the vulnerabilities and take steps to protect systems and data.
Every organization needs to designate someone as the security officer. Someone who:
You’ll want someone who understands technology and can make tough decisions.
Communication is key. You need someone who can talk with all departments.
No more excuses for not having multi-factor authentication (MFA) fully deployed on all your clients.
What’s one good reason for your client not having MFA?
There isn’t one.
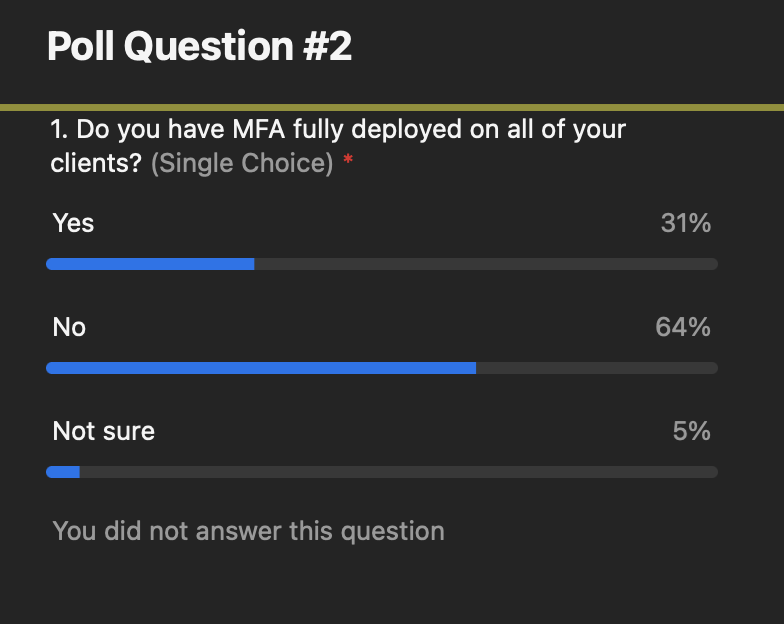
When we polled whether organizations had MFA fully deployed for all of their clients…
31% said yes.
64% said no.
5% were unsure.
MFA isn’t just nice to have. It’s mandatory for your client’s security.
It’s easy, inexpensive and critical for preventing breaches. It’s not something to consider in the future.
It’s easy to get hung up on the perfect solutions, but even a simple SMS-based MFA is better than no MFA.
If your clients don’t have MFA, they won’t be able to get cyber insurance. Their premiums will double. It’s a bad time.
Give your client peace of mind knowing they’re covered.
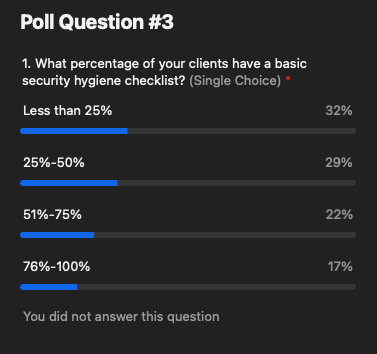
We asked our audience during the webinar, and it turns out that 25% or less of their clients have a basic security hygiene checklist.
It’s not that they’re not taking it seriously…
They don’t know where to start. And let’s be honest: security hygiene isn’t the most exciting thing in the world. It can feel like a lot of work and very technical.
More clients didn’t have a basic security hygiene checklist than did:
Your customers don’t need to understand the complex details behind cybersecurity best practices. Operating a computer and following basic security practices is like driving a car. You don’t need to know how the car works, but you need to know the brake, gas peddle… even the turn signal.
Leave the hard car stuff to the mechanics.
Leave the hard computer stuff to the MSPs.
If you’re new to cybersecurity, you’re in the right place.
Starting can be intimidating. Security isn’t always a one-and-done proposition. It’s about small daily actions that keep your business protected when added together.
At the heart of cybersecurity is simplicity.
The Back to Security Basics Checklist helps IT providers and customers set daily cybersecurity hygiene. Now you and your customers can start on the right foot by setting daily protection so that you’re always covered.
Your checklist gives you an edge in this critical cyber battle for good.
Download your cybersecurity hygiene checklist to establish your daily routine quickly and easily.
Get insider access to Huntress tradecraft, killer events, and the freshest blog updates.
