







For medical professionals, data saves lives. For hackers, data drives profits. When one has the data, however, the other does not. This ongoing battle for access keeps healthcare providers on their toes. Cybercriminals are relentlessly trying to grab everything from your patients’ protected health information (PHI) to your email credentials to your organization’s financial records. And while the explosion of endpoints across the industry has made it easier for you to access the data you need, it’s also made it easier for hackers to do the same.
This proliferation of digital endpoints across healthcare—from electronic health records (EHR) to telehealth services to mobile health apps—has undeniably led to greater efficiencies and improvements in remote and in-person care. But these advancements have also expanded attack surfaces, giving threat actors more opportunities to access and exploit your devices.

Healthcare organizations and their staff must maintain awareness of all devices. Whether due to negligence or deliberate theft, the loss of mobile phones, tablets, laptops, USB drives, and other interconnected devices can have disastrous outcomes. A missing device doesn’t just mean lost hardware—it means sensitive data has potentially fallen into the wrong hands.

Imagine a doctor sitting in a coffee shop, casually stirring her morning espresso, reviewing patient charts on her laptop. After a few sips, she receives an urgent call, telling her she needs to get to the hospital right away. She grabs her coat and rushes out of the cafe, but in her haste, she doesn’t just leave her drink behind but also her laptop. When she realizes her mistake an hour later, she hurries back to the shop, only to find cold coffee and no computer.
The choice the doctor makes next is critical. Ignoring the loss leaves sensitive data exposed to anyone with malicious intent. But if she reports the lost laptop, IT can disable the device and prevent unauthorized data access. This is important because even if the doctor somehow gets her laptop back, its data could’ve already been compromised. For instance, an attacker may have:
Put simply, threat actors want data because it’s currency. It can be extorted for a heavy ransom, sold online to the highest bidder, or exploited for identity theft. Though stemming from an honest mistake, the repercussions for the doctor and her practice can extend beyond financial burdens, including:
An insider threat can be either accidental or intentional. An accidental leak of data can result from simple negligence. Intentional threats, on the other hand, involve individuals seeking to steal data for profit or purposefully inflicting damage upon your organization.
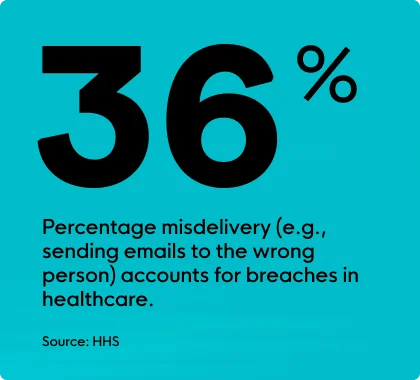
Suppose you’re a dedicated nurse, always putting your patients first, but you’re a bit distracted one morning. It happens to the best of us. You mistakenly tap the wrong keys and misspell a patient’s email address. The name looks right at a glance, but the email goes to the wrong recipient. As a result of a seemingly small error, you disseminated personal data to a complete stranger. This was an honest mistake, and you didn’t commit the act with any intention of causing harm. This is an example of an accidental insider threat, and though it can be chalked up to simple human oversight, the consequences can still be serious. If the recipient acts with malicious intent, they might:
But insider threats aren’t always accidental. Malicious insiders with legitimate access to your systems may intentionally steal data for a fast profit. Imagine a disgruntled nurse—he’s feeling overworked, underpaid, and unappreciated—stealing copies of patients’ medical records, making copies of them, and selling them online, where each record can fetch up to $1000 a pop. Insider threats are especially nefarious because they’re premeditated by people you might know and trust, yet you may not realize their intent to cause harm and compromise patient safety.
Whether the data loss is accidental or intentional, the outcome can be equally disastrous. Both types of loss highlight the need for robust security measures, employee training, and strict access controls to protect sensitive information in healthcare settings.
According to the Department of Health and Human Services (HHS), the most common errors in healthcare data security are:
In healthcare, the sheer number of people involved—full-time employees, contractors, and more—means it's easy to lose track of who has access to sensitive information and how that information is handled. This makes the industry particularly vulnerable to insider threats, and they’re amplified if your organization has:

Being vigilant is always the best step when securing sensitive data. Of course, mistakes can happen. And worse yet, no matter how aware we might be, those with malicious intent may still sneak by and get away with theft.
In any high-stress environment, people will make mistakes. But keeping security top of mind can mitigate risks. That’s why a robust security awareness training (SAT) program is essential. It can better help everyone across your organization identify potential threats and understand the serious consequences of data loss. By keeping your people vigilant and proactive, your healthcare organization can protect sensitive data and maintain the trust of your patients.

Huntress Security Awareness Training is a unique solution that fuses vibrant animations with science-based learning principles to help improve your organization’s security posture. Through story-driven episodes focused on data protection, Huntress SAT helps drive meaningful behavioral changes for you and your colleagues. Notable episodes include:
Real cybersecurity practitioners from the Huntress Security Operations Center (SOC) design each episode, fashioning them around the latest hacker tactics they observe in the wild. So as new threats face the healthcare industry, Huntress SAT will adapt to them, keeping you and your staff one step ahead.

The data within your systems is a goldmine for cybercriminals. If it falls into the wrong hands, the consequences can be catastrophic—ranging from financial ruin to severe reputational damage and, worst of all, compromised patient care. That’s why your team must stay vigilant against potential cyber threats.
With our 24/7 SOC and swift threat neutralization, Huntress’ managed solutions are tailored for health providers. In fact, we already secure more than 10,000 healthcare organizations. Given our track record of protecting millions of endpoints globally, we help you prioritize what matters most—patient safety.
Get insider access to Huntress tradecraft, killer events, and the freshest blog updates.
