







Since our inception, Huntress has had a guiding principle to protect the 99%. This ethos has led us to create products, features, and functionality that look to prevent issues and stop problems that plague small and medium-sized businesses (SMBs) globally.
While we don’t have a crystal ball that will tell us exactly where attackers will strike next, what we can do is look at where SMBs are most at risk and anticipate the types of threats that seek to exploit them. Business email compromise (BEC) is one such threat.

BEC attacks are becoming more prevalent across businesses of all sizes. In fact, the FBI’s Internet Crime Complaint Center found that BEC is a $50 billion problem. So, to combat this ever-growing and expensive threat, we released Huntress Managed ITDR, our answer to modern-day business email compromise attacks that plague SMBs day in and day out.
When looking into BEC from the lens of an attacker, there is a fairly linear process for getting the end result—either financial gain for the threat actor or gaining personally identifiable information (PII) to be sold or used at a later date. The BEC attack chain typically looks something like this:
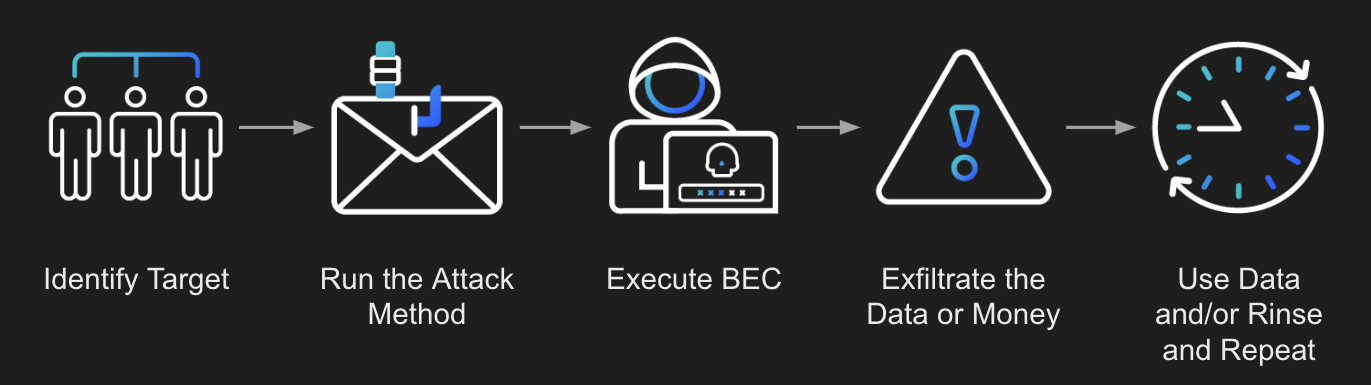
As you see in the above graphic, the process starts with identifying a target. This is done by using either publicly accessible means like social media to find out information about the target, or through information previously gathered from the organization through reconnaissance or purchased information from the dark web. Using the information gathered, a very personalized attack can take place, playing on the emotions or psychology of the target to get them to act quickly and ignore red flags.
With the target lured in, the BEC attack itself can start. This usually involves attempting to gain the target’s information or credentials. Once they have that, they can forge their digital identity to trick other victims into redirecting payments or offering up more sensitive information.
So, how do we protect against something that preys on the human element? We use that human element to our advantage instead.
At Huntress, we use a best-of-both-worlds approach when battling attackers: powerful software backed by human expertise. Using years of practical cyber knowledge, we’ve built automated detectors that comb through all the information we get from Microsoft—such as user, tenant, and application data logs—to ascertain whether or not a process or event seems malicious. These detectors work to minimize the initial noise and billions of data points we receive from Microsoft. Anything we deem suspicious gets filtered down to threat signals for our 24/7 SOC team to scrutinize.

With their top-notch experience and passion for ruining an attacker’s day, this team will dive into anything that doesn’t look and/or feel right, pulling apart information to help confirm whether or not we’ve uncovered a truly malicious event. Once a threat is confirmed, our SOC analysts can isolate an identity from the rest of the tenant to stop any further malicious activity. We also create a customized action plan to help our partners remediate any found threats or undo any compromise that has taken place, as well as ensure the environment is fortified against future attacks.
Some examples of the attacks that we are already looking for and detecting within Microsoft 365 tenants are:
This attack looks to take real emails, normally containing payment information, credentials, or something similar, and move them into either a hidden area of the user’s mailbox. Obfuscating emails or sending them to an external mailbox that the attacker owns clears all traces of the email coming in or being sent out. With this attack, users are very seldom aware that it’s happening—and it’s all happening using Microsoft built-in capabilities to automate email processing in the mailbox.
When an attacker gains access to a Microsoft 365 tenant, one of the first things they are going to want to set up is persistence within that environment. The simplest way of doing this is to create an account within the environment that is inconspicuous in nature; this way, they always have access back in even if their initial access account were to change their password. Once the new account is online, they can elevate that account to have global Admin permissions and truly have the keys to the kingdom, being able to change anything, add rules, and cover their tracks.
These are just two out of countless types of BEC attacks that we at Huntress are able to look for, and we’ve seen some amazing success against some of these terrible attack types. You can read up on those in these blogs:
Business email compromise is not going away. The world is becoming more reliant on email services like Microsoft 365 and attackers know this. Their methods for gaining access are becoming harder to detect using tools that rely on systematic processes and procedures. Without a human-led and fully staffed Security Operations Center (SOC) taking a look into anything that could potentially be an attacker's tradecraft, things can and will be missed. When thinking about how we can protect against BEC moving forward, the answer is Huntress is how.
Get insider access to Huntress tradecraft, killer events, and the freshest blog updates.
