







Tl;dr: To support CMMC compliance, Huntress released a new Sensitive Data Mode, which blocks SOC access to potential CUI files, without compromising analysts’ ability to effectively detect and remediate threats. Read on for a deeper understanding of CMMC compliance and how Huntress helps.
Increasingly sophisticated cyber threats have placed greater demands on the security of organizations, particularly those in the supply chain for the Department of Defense (DoD). The Cybersecurity Maturity Model Certification (CMMC) was introduced to set a new bar for compliance and risk management.
But navigating CMMC compliance—particularly as it has gone through several updates—can feel daunting. It’s essential to understand how tools like Huntress can fit into a compliant and secure framework.
Launched in 2020, CMMC 1.0 was built around five distinct maturity levels, each requiring external audits. Vendors supporting organizations subject to CMMC also had to demonstrate compliance, either through their own CMMC audit or by obtaining FedRAMP authorization. These high standards created substantial hurdles, particularly for smaller vendors, due to limited resources and high costs.
By 2021, the framework evolved into CMMC 2.0, reducing the number of levels to three. This shift streamlined the landscape while still maintaining robust compliance measures. Importantly, external audits became mandatory only for organizations at Level Three and select Level Two entities. However, vendors serving CMMC-applicable organizations were still held to strict compliance requirements within the 1.0 rules.
The 2024 CMMC Final Rule introduced noteworthy changes, especially in vendor requirements. Vendors storing, processing, or modifying Controlled Unclassified Information (CUI) remain obligated to meet full CMMC compliance or FedRAMP authorization. However, vendors that act solely as Security Protection Assets—tools that provide security without directly storing, processing, or transmitting CUI—are no longer required to undergo the same external assessments. Instead, the compliance responsibility shifts to the organizations using these tools to ensure that the security capabilities their vendors provide are adequate to meet the CMMC objectives.
The CMMC framework identifies Security Protection Assets as third-party solutions that provide security functions or capabilities to the contractor’s CMMC Assessment Scope.
Huntress is classified as a Security Protection Asset, as we can help CMMC-bound organizations remain secure through our offerings:
Security Protection Assets—like Huntress—are to be evaluated based on their security capabilities, and aren’t subject to separate compliance audits themselves.
When managing cybersecurity in a CMMC-compliant environment, certain capabilities are required for handling files containing CUI during threat detections. For example, retrieving files for malware investigations could unwittingly expose sensitive information.
Recognizing this challenge, Huntress built our new Sensitive Data Mode—a configuration designed to strike the perfect balance between effective threat investigation and compliance requirements.
Here's what the new mode delivers to help you support CMMC compliance:
Huntress now enables organizations to block our Security Operations Center (SOC) from accessing files likely to contain CUI during investigations. Huntress blocks high-risk file types (e.g. documents, spreadsheets) from being retrieved during investigations. This measure reduces risk and protects compliance.
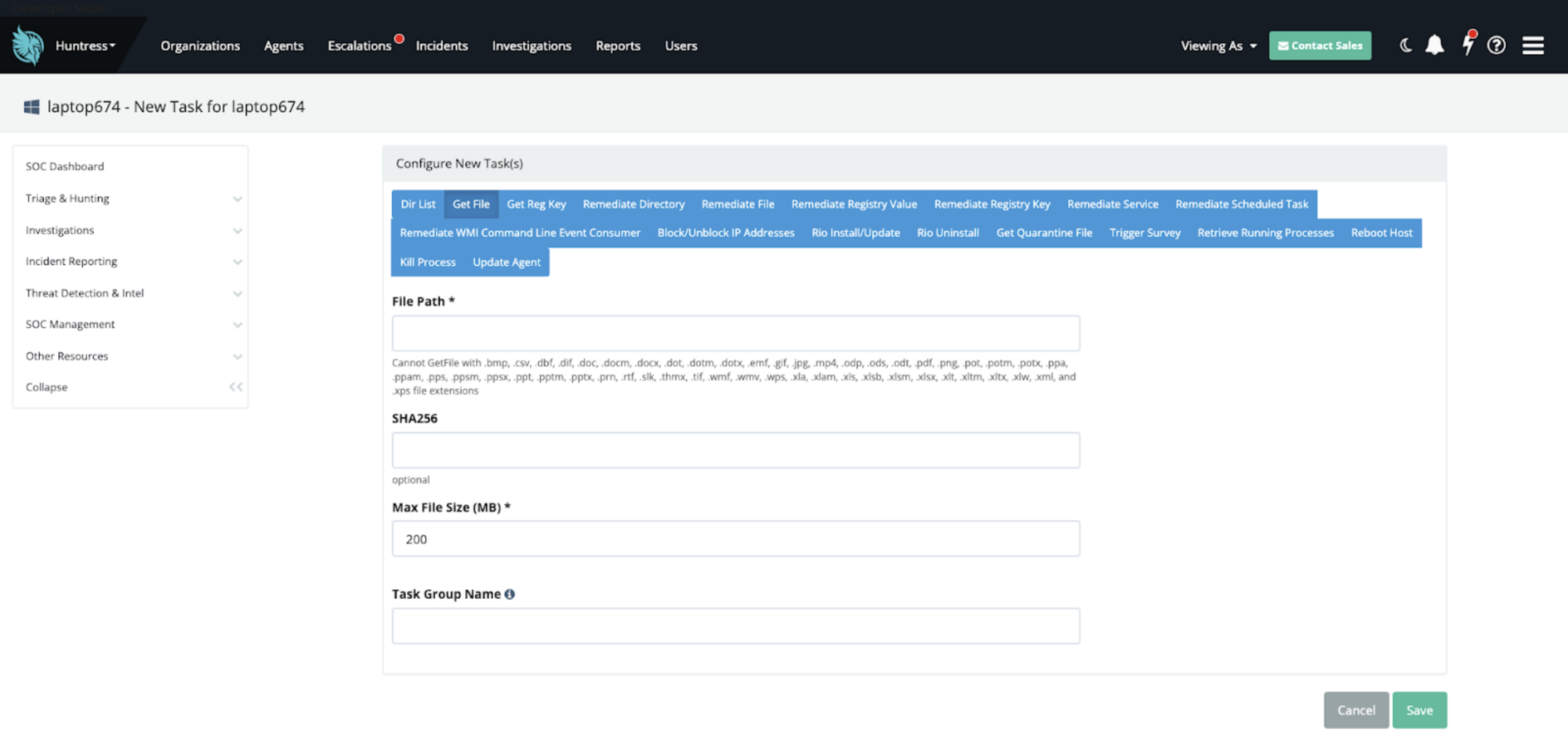
Huntress analysts can still retrieve and analyze executable files, scripts, or other non-sensitive file types often associated with malicious activity. This means we can continue to deliver critical incident reports at 99% accuracy—without compromising compliance.
Sensitive Data Mode is available now and can be configured upon request by contacting support.
Want to see how Huntress can strengthen your security in a CMMC-compliant environment? Download our CMMC Security Framework Checklist.
And be sure to book your demo with Huntress today.
Get insider access to Huntress tradecraft, killer events, and the freshest blog updates.
