







As you may have noticed, macOS malware is still very much a thing these days.
We covered some of the malware variants that were seen over the last year in our Mythical macOS Malware episode of Tradecraft Tuesday, which brought some of this badness to light. And Patrick Wardle has just released his new book, The Art of Mac Malware, which is a must-have for those who want to learn more on the topic.
With macOS malware continuing to ramp up, it’s become clear that a macOS agent is our next logical step with our next iteration of The Huntress Managed Security Platform.
As we like to say, hackers gonna hack Mac? Huntress gonna hack back. 😉
As attackers continue to keep tabs on the steady growth of the macOS platform, we defenders must be ready. With this, we are putting our Huntress macOS agent into General Availability! This means anyone with a Huntress account has access to it.
Based on all of our research studying various macOS attacker tactics—let alone our roots in hunting for persistence—persistence was the obvious place to start. Persistence is prevalent across many malware families on macOS, as we’ll see later.
As identified by Patrick Wardle in previous research, the most common infection vectors are as follows:
As you can see, some of these aren’t much different from what we see currently in the Windows landscape. We won’t go into all of these but will highlight some of the more common ones.
Phishing emails will always be prevalent since the weakest link often has a bit of the human element. Fake and malicious or trojanized programs are often quite effective as well.
Plus, attackers appear to target users who may not be familiar with macOS in general—for example, by choosing to masquerade as common Windows programs like Adobe Flash Player, as Shlayer did within the last year. Windows users are used to having to update software like Adobe Flash Player or Reader and may be easy prey to malware authors under such guise.
Another way that malware can take advantage of users’ unfamiliarity with macOS features is by crafting malicious URLs that may result in Safari automatically processing the files. Users may be unaware of this default setting of Safari. As a result, files with common extensions are automatically processed and opened when they are downloaded, which could lead to accidentally executing malicious code.
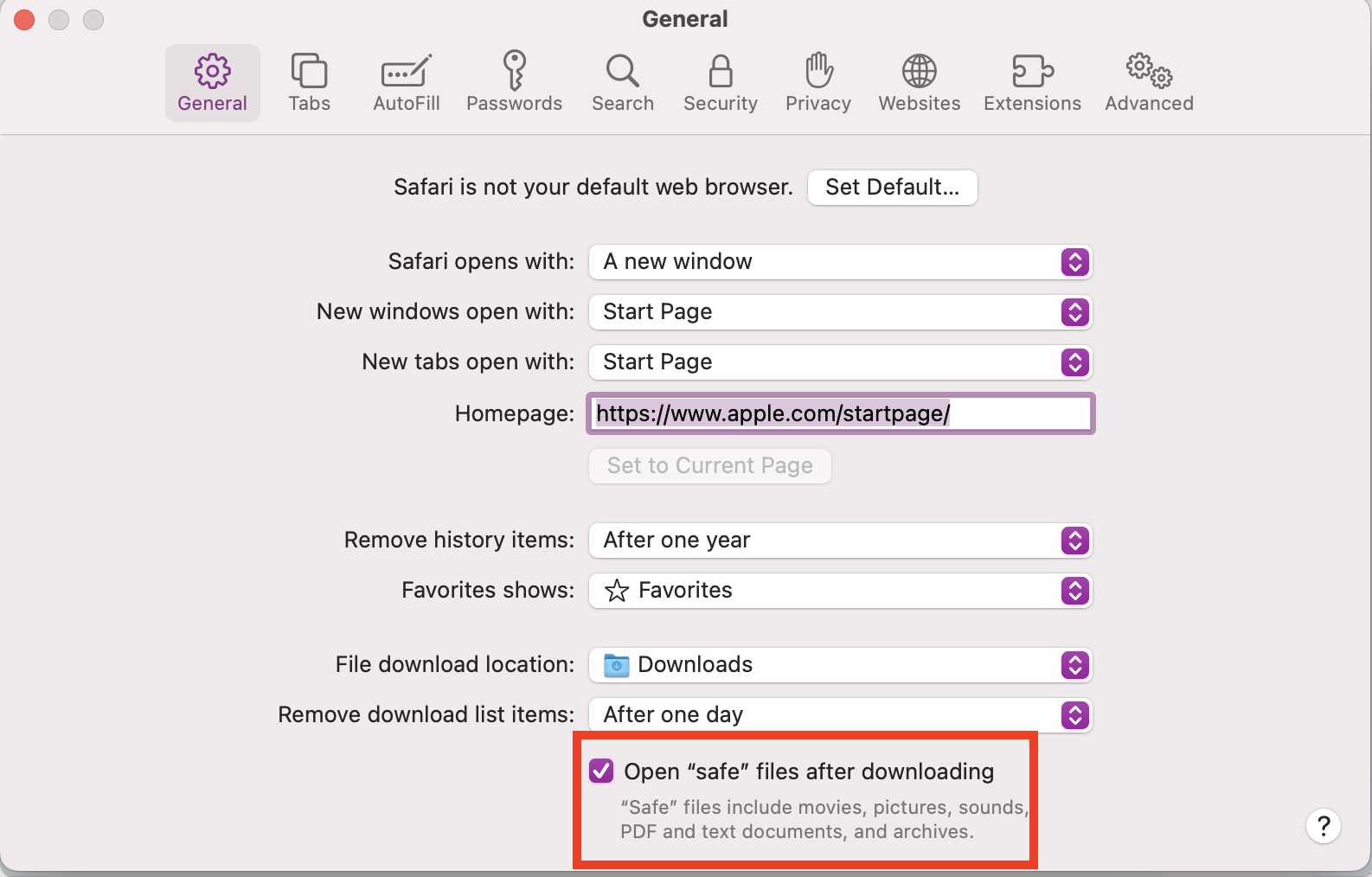
Even when a user has all their security settings correctly configured, there are times when attackers can gain access to the machine by exploiting flaws in software.
Looking at various CVEs for macOS and macOS software for just the last year yields several exploits that could allow an attacker to wreak havoc on the machine. Patrick Wardle found a rather interesting 0-day in Zoom back in August, which is even more relevant in today’s age of working from home. You can see how important it is to keep an eye on your macOS fleet, even when your users are keeping things up-to-date because you never really know what might happen on their machines.
Once malware makes it onto the machine, it will need a way to persist past reboots. The main persistence mechanism used by macOS malware uses LaunchAgents. This is accomplished by adding plist files within the systemwide /Library/LaunchAgents folder or user’s /Users/[username]/Library/LaunchAgents folder (denoted as ~/Library/LaunchAgents in the following table).
Looking at some of the more recent malware samples that appeared within the last year, we can see some of the previous names used. Some of these make an attempt to blend in with other existing plist files, while others visibly stand out to the naked eye.
SysJoker/Library/LaunchAgents/com.apple.update.plistElectroRat~/Library/LaunchAgents/
mdworker.plistSilverSparrow~/Library/Launchagents/init_verx.plist (dynamically named)
CodeSpy~/Library/Launchagents/com.apple.appstore.checkupdate.plist or
com.apple.usagestatistics.plistWildpressure~/Library/Launchagents/com.apple.pyapple.
plistXloader~/Library/Launchagents/com.[random].[random].plistOSX.MacMa~/Library/
Preferences/UserAgent/com.UserAgent.va.plist or
~/Library/LaunchAgents/com.UserAgent.va.plistOSX.OSAMiner~/Library/LaunchAgents/
com.apple.FY9.plistOSX.Convuster~/Library/LaunchAgents/com.ist.up.plist
and /Library/LaunchDaemons/com.ist.up.plist
Several other types of persistence exist, but we’ll cover those other mechanisms in an upcoming blog.
We’ve had several macOS agents deployed in test runs across some customers and have managed to already detect malware. One example we’ve found during this time is Bundlore.
Bundlore is a malicious macOS X adware that bundles multiple different types of adware together and is then installed on the host. This nasty piece of malware proved to be no match for one of our rising stars in ThreatOps, Molly. She quickly dissected its bits and got to the heart of the matter. Keep an eye open for an upcoming blog where she’ll cover all the gruesome details of this case.
Persistence is only the first step into the world of macOS.
Given the growing footprint of macOS endpoints – and correlating attention from attackers – there are a lot of opportunities in front of us to secure endpoints. From additional remediation capabilities such as Host Isolation to widening our visibility for deeper detections, there’s a long way to go from here.
Stay tuned!
Get insider access to Huntress tradecraft, killer events, and the freshest blog updates.
