







Security awareness training is easy to think about as a passive item. You go buy a training platform or SCORM files for your LMS, assign the annual training, set it to nag your people to watch the video, and you’re done.
While that approach certainly will fulfill some of the compliance requirements to perform annual security awareness training, is it actually improving the security posture of your organization?
Humans are both our biggest cybersecurity risk and our best detection engine. While humans and their identities are the target for initial access on most modern breaches, they are also far more capable of detecting ‘weird’ stuff than security tools. The proper security awareness training program minimizes the risk posed by your employees while also improving their response times when they detect something is off. Spending the extra time to bolster the human detection capabilities is some of the best ROI you can achieve in the security space.

At Huntress, we train our human detection capabilities in two ways:
First - Monthly security awareness training. Every month our staff receive new training to watch, using our very own Security Awareness Training product. This is to keep security front of mind and ensure a base level of security acumen across the workforce. We use these to reinforce good cyber hygiene while also educating our staff on the tactics used by adversaries. (Want us to manage those monthly trainings on your behalf? Check out our managed learning option)
Second - Monthly (or more frequent) phishing simulations. We do these frequently and celebrate individual failures. Tracking the organizational failure rates and adjusting the phishing lures you use accordingly builds resilience.
Social engineering is an attack on the psychological traits we have as humans: an innate desire to be helpful, trusting of strangers, and a fear of getting in trouble. Attackers leverage techniques of fear, intimidation, urgency, empathy, compensation, or authority in order to spike an adrenaline response to their message. Their goal is to spike your ‘fight or flight’ response so you don’t stop and logically think about an email.

Attackers take advantage of the psychological traits we have the same way they exploit vulnerabilities on a server. They find a vulnerable asset and exploit that vulnerability in order to gain initial access to a system.
Simulated phishing has the same desired outcome as vulnerability scanning your servers. We want to know where there are weaknesses so we can address them. Said differently, we are enumerating our human attack surface.
Phishing simulations have three goals:
1. Exposure therapy
By regularly using the same psychological exploits social engineers use, we lessen their impact and reduce the likelihood of an adrenaline response.
In order to increase organizational resilience, you should rotate the tactics used in your monthly simulations each campaign.
2. Identify your most vulnerable
Some of your users will be more susceptible to social engineering attacks either due to a heightened sense of trust or a lack of technical knowledge required to inspect an email for legitimacy.
A single failure is a learning opportunity in and of itself. Celebrate when someone fails and owns their failure; they are going to be far less likely to click next time. However, a series of failures is an indication the user needs individualized help. Spend your time training your repeat clickers, not the one-offs.
3. Measure your organizational reporting
Phishing attacks can be combated quickly, when alerted upon. We can revoke emails from inboxes, send awareness announcements, and more. But it all depends on how quickly a campaign is reported.
I treat a campaign that is reported before the first click as a massive organizational success, regardless of the click rates on the rest of the campaigns. If you find users are failing your test before the test is reported, it's time to remind the organization how to report suspicious content.
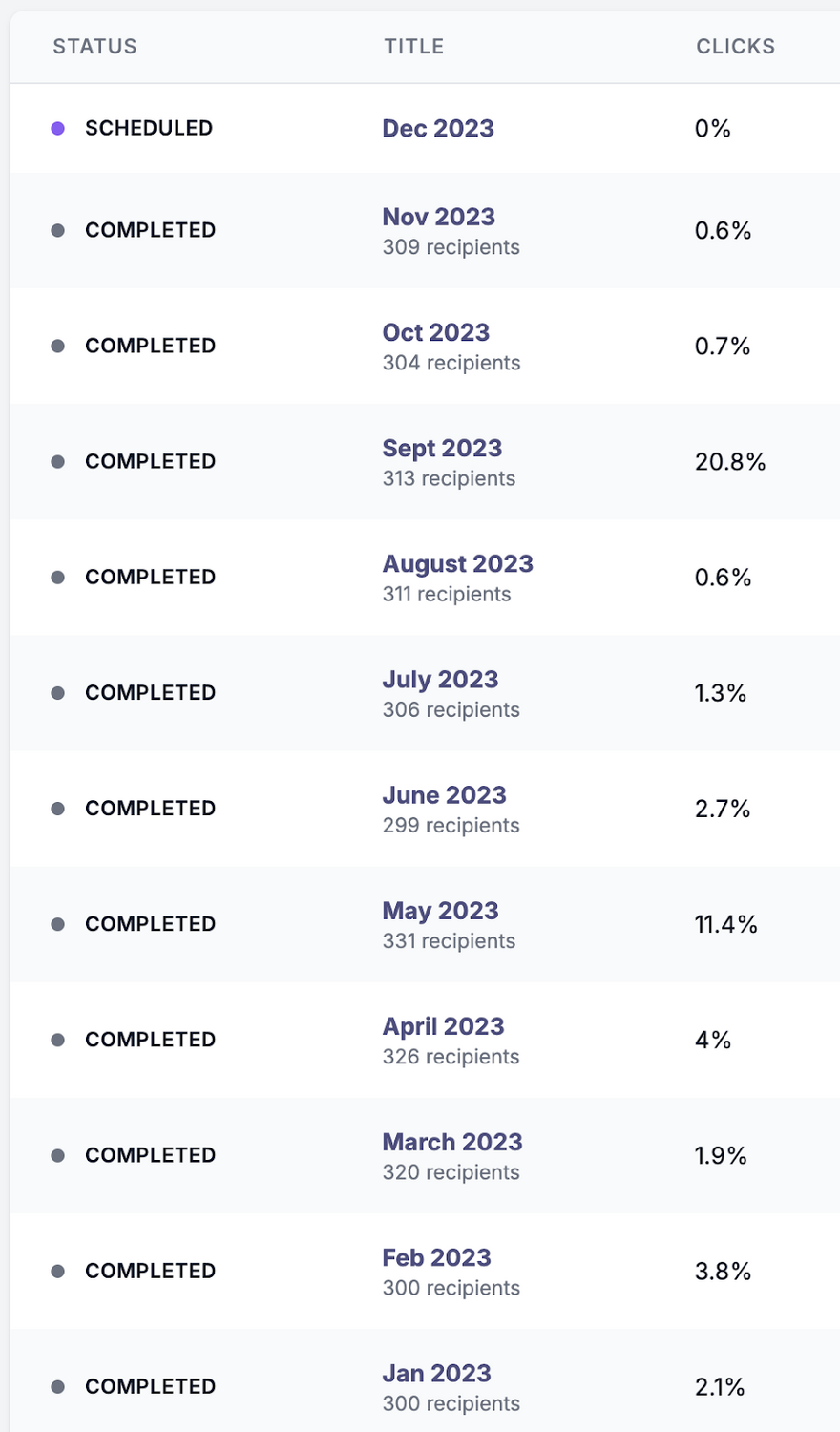
At Huntress, we phish our employees every single month. These are our actual results since January.
You will notice there are a few months where we had spikes in the click rate. These spikes are what we are after. As our click rates decreased from the prior month, I increased the difficulty of the emails.
Looking at our click rates, there is an interesting trend I want to point out. After a month where a large percentage of employees clicked the lure, there was a sharp decline in the following months. This is why we want to get our employees to fail. By failing the test, they become more aware of their vulnerability and pay better attention—at least for a few months, according to this data.
For the sake of keeping this brief, I want to talk through my strategy for the first two months of the year.
In January, our phishing emails went out mid-week during regular business hours. This got ~2% of our employees to click the link in the email. I used a generic lure of the promise of payment for completing some easy task—a survey, a feedback call, or a Covid-19 stimulus. This was an excellent outcome. It showed our organization had a good baseline ability to detect phishing emails when the sender was not expected.
February needed a harder scenario and we needed to test a different tactic. The February campaign also went out mid-week, but this time, it spoofed our internal conferencing tools. ~4% of our employees clicked the link. Still under the 5% I aim for, our employees know to look at the sender of emails. We also did not see a single re-clicker; no one who failed in January failed in February. Awesome. We also had our employees dropping screenshots of the phishing email all over Slack; the organic dissemination of the threat was quick to de-fang the simulation.
Every month, I aim to vary the tactics I use. I do not want our employees to expect the same phishing email every month, as it drives complacency. So when planning your phishing campaigns, think like a hacker with inside information.
I want to end with a call for empathy toward your employees who do click.
When an employee fails a phishing test, they often react with either shame or anger. Many will send messages or call with explanations as to why they failed, or just send messages of “sorry.” Do not reprimand these failures. These are opportunities to discuss what they could have done differently in the future and remind them that we do these tests specifically to increase awareness.
Get insider access to Huntress tradecraft, killer events, and the freshest blog updates.
