Let’s put our adversarial hats on, shall we? Say you were a malicious hacker, and you wanted to target the top managed service providers (MSPs). How would you do it? Where would you start?
Well… a good fisherman goes where the fish are.
Through the rush to remote work and the COVID pandemic, we live in a new world that relies on remote events and virtual conferences. You know the ones I’m talking about—you register with your business email and your job title in order to talk shop with like-minded folks.
Imagine that: one online location where everyone in the industry has willingly offered their contact information, all to network and grow their community.
That sure sounds like a treasure trove for hackers.
Most organizations have spent the past year scrambling to virtualize their events and expand their webinar calendar. As a result, these platforms haven’t been built with the best security in mind.
Keep reading to learn about the zero-day vulnerabilities we discovered in multiple virtual event platforms used in the MSP and Fortune 500 communities, as well as some insights into supply chain attacks and vendor accountability.
What Vulnerabilities Did Huntress Find?
We uncovered software flaws and misconfigurations within two of the top five virtual event platforms—the first was webcasts.com, which impacted its integrated customers (such as 6Connex), and the other was VFairs. These flaws include vulnerabilities ranging from information disclosure or PII leakage (such as names, emails, IPs, etc.), to direct access to databases and potentially gaining remote code execution.
We actually discovered these vulnerabilities as attendees of events that were hosted on these platforms. We were there to network and chat with others—just like everyone else—but after some poking and prodding, we stumbled upon some unintended behavior within the event platforms.
As attendees for a webcasts.com event on 6Connex, we were able to join any chat room to connect with other attendees. But we found that we were able to see more about the attendees through their attendee IDs, and ultimately uncovered a huge data dump of all the users who were partaking in the virtual conference. This included a lot of personal data. We’re talking names, company and title, emails, IP addresses, and potentially city, state, phone number and physical address—and not just to us as presenters, but anyone at the event (or any other event for that matter)!
At another event we attended on VFairs, we saw that we could edit our profiles for a better networking experience. But here was the issue: we had the ability to change not only our own profile, but if you peeled back the layers and toggled the ID numbers, we could change anyone else's profile too. This could allow a nefarious actor to perform cross-site scripting attacks, steal user cookies, impersonate them or force their web browser to different locations. And the ability to change a profile picture wasn't limited to a JPEG or image file—you could upload PHP code, opening the door for remote code execution. Additionally, SQL database errors were public and the platform was vulnerable to a time-based blind SQL injection, giving a bad actor direct access to the database. These exploits could allow full access to potentially control the server and website. These vulnerabilities were present in version 3.33 of the VFairs application, and were since patched in version 3.34.
What Major Organizations Are Using or Supporting These Platforms?
The official website for VFairs includes testimonials from Ford, T-Mobile, IEEE, Pearson and others that may be affected. And from our research, we have found many companies and organizations use webcasts.com to host virtual events, including the US Food & Drug Administration, the National Medicare Secondary Payer Network, research labs for COVID-19 updates, Google and more.
Back in September, it was reported that a virtual job fair for the intelligence community hosted on the 6Connex platform exposed job seekers’ identities and social media profiles—but this flaw was just the tip of the iceberg.
Was Any Sensitive Information Stolen or Compromised?
At this point, we can’t predict whether information was actively stolen or compromised by attackers or unauthorized users. But it certainly was possible, and these types of vulnerabilities could very well be present in many other online conferencing platforms.
Are the Event Platform Companies Aware of These Vulnerabilities?
Huntress notified VFairs and 6Connex of these potential vulnerabilities in September and October of 2020. VFairs did not respond to our initial outreach for three weeks, while 6Connex responded the very same day. Both parties were appreciative of the responsible disclosure and explained that they have since patched the vulnerabilities.
But Wait… There’s More
Major recent events like the SolarWinds exploit have put supply chain security at the forefront, but supply chain risk is not limited to government-used IT software. While diving into our research, we also discovered a large SMB supply chain breach that disclosed 250k+ confidential details on SMB mergers and acquisitions, financing and more.
Here’s part of the thread on Twitter before it was instantly removed and the account was banned.
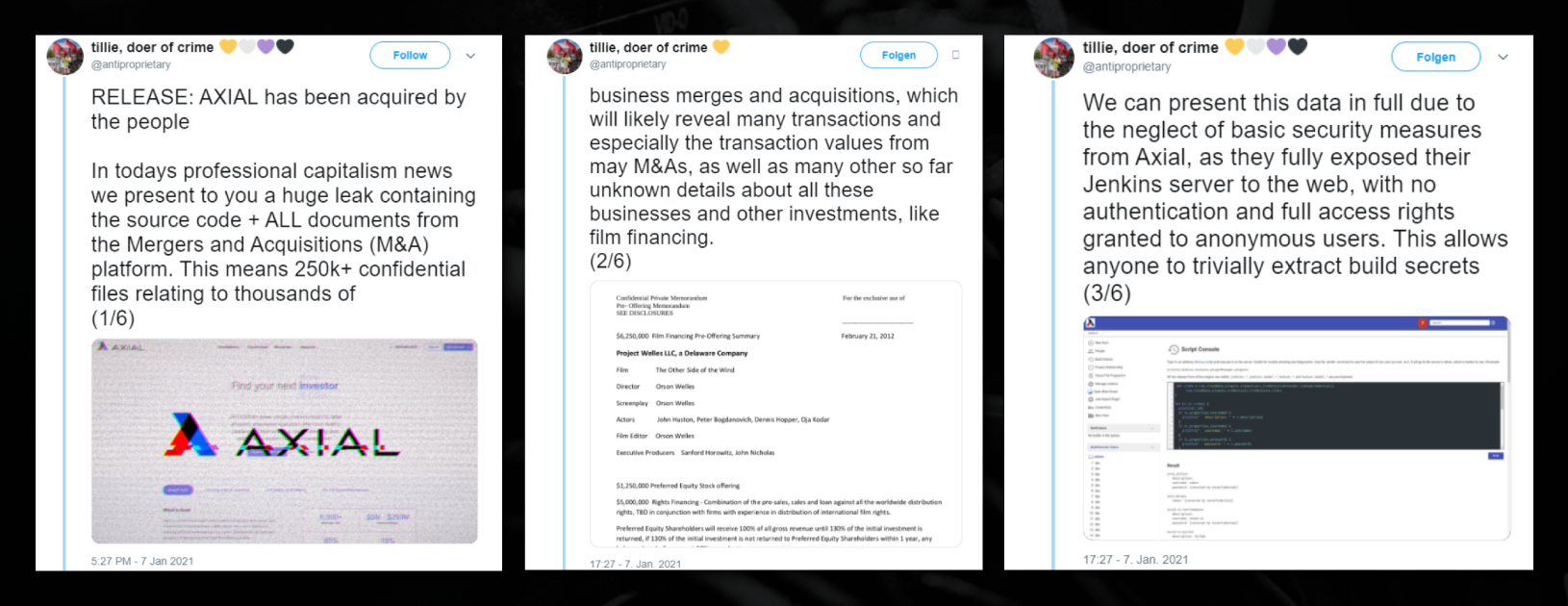
It’s common security practice to vet every aspect of data receiving tools and software to reduce and mitigate risk—but this was not the case here.
As you can see, a huge amount of sensitive and confidential financing information was leaked from Axial, a platform for buying, selling, advising and financing private companies—all due to neglect of basic security measures.
And here’s the harsh reality of why we’re sharing this: unfortunately, these supply chain data breaches happen all the time. But when they only impact the SMB, these types of breaches rarely make headlines.
What Should MSPs Take Away From This?
So what does this all mean for MSPs? Ultimately, this is yet another slap in the face reminding us of the need for vigilance and bare-bone security basics. We aren’t telling you to sign up for events with a throwaway burner email address, fake name and sock puppet accounts—there is genuine value in being a part of the community and collaborating with your peers.
But we are telling you that no platform is immune.
If a new third-party solution, no matter what it may be for, isn’t properly vetted and evaluated against its security posture—then it is not a solution, it is a problem.
How do you stop a supply chain attack? You don’t. It is practically an insider threat that you are blind to and unaware of. The best defense is knowing the product, the pipeline and the process as best you can before you use it, so you can better decide to use it at all. These problems with event platforms could very well have contributed to the spike in MSP-focused phishing attacks we saw in 2019 and 2020—and we are the ones left holding the bag.
As a broader cybersecurity community, we need to take this as an opportunity to step back and consider if we truly care about security.
Do we really care? If we don’t, we might as well throw our hands up, pack it up and go home.
If we do, then we need to start asking ourselves, “are these vendors who ask for my data competent enough to protect it?”
From what we can tell… most are not.
• • •
If nothing else, this shows just how much proactive threat hunting is needed to stay ahead of malicious actors. If it weren’t for our team’s poking and prodding and responsibly disclosing these security flaws to their vendors, any ill-intended attacker could have exploited these vulnerabilities and the fallout could have been disastrous.
The good guys need to step in before the bad guys do. That onus is on all of us—and Huntress is happy to be part of the community that makes for better security, not worse.
Want to learn more about how hackers could have exploited these virtual event vulnerabilities? Watch our on-demand webinar where we spill all the details.

















