







On December 13, FireEye discovered that SolarWinds Orion products (versions 2019.4 HF 5 and 2020.2 with no hotfix or 2020.2 HF 1) were being exploited by malicious actors. The supply chain attack trojanized SolarWinds Orion business software updates in order to distribute malware that has been referred to as both SUNBURST and Solorigate.
This post was last updated on December 15, 2020 at 05:36 pm E.T.
Our technical findings can be found at the bottom of this article.
As far as we know at time of publishing, this does not affect SolarWinds N-central or SolarWinds RMM. Our team is actively digging into this — you can follow along here.
The answer is, well, both. The Orion update versions released between March 2020 and June 2020 have been tainted with malware, which FireEye was first to name SUNBURST. Microsoft has separately named this malware Solorigate and added detection rules to its Defender antivirus.
Here’s what it looks like from an attack chain perspective:
Initial Access: Attackers were able to silently add malicious code to SolarWinds’ software updates for Orion users. These updates were trojanized to contain a backdoor that reaches out to third-party servers (specifically a DLL) — enabling the attacker to gain a foothold in the network through routine or automatic updates.
Persistence: Once the trojanized DLL is successfully loaded, threat actors now have access to the environment, enabling the ability to scan the system, exfiltrate data, and/or steal credentials. Because this was signed with an official SolarWinds certificate, it appeared to be a legitimate and a trusted update — bypassing standard AV or endpoint detections.
Post Exploitation: The malicious DLL beacons out to command and control (C2) infrastructure to receive additional commands and payloads. Initial C2 traffic blends into the normal network activity, masquerading as the Orion Improvement Program (OIP) to look like legitimate SolarWinds operations.
Additional research by Microsoft indicates that in some instances, attackers were able to gain administrative access and even compromise SAML token signing certificates — allowing the attacker to forge SAML tokens. Forged SAML tokens may potentially give access to any privileged resources that trust that SAML token signing certificate.
Action: At the moment, it is unclear what the motivation or the end goal is of the attacker. Most evidence suggests this is an extremely narrow and targeted nation-state activity as opposed to a wide-spread attack.
This appears to be the work of a highly skilled actor. The campaign may have begun as early as Spring 2020 — and it’s still ongoing.
What’s interesting is that the backdoor DLL was actually digitally signed by SolarWinds, therefore could be evaded by AV and most endpoint products. Microsoft has since added detections for this malicious DLL using the legitimate certificate. Defender will now automatically flag the backdoored application.
In addition, other endpoint security tools are quickly taking action and building updates to help detect and mitigate this threat. Earlier this morning, only 1 out of 67 antivirus engines listed the SUNBURST backdoor (SolarWinds.Orion.Core.BusinessLayer.dll) as malicious.
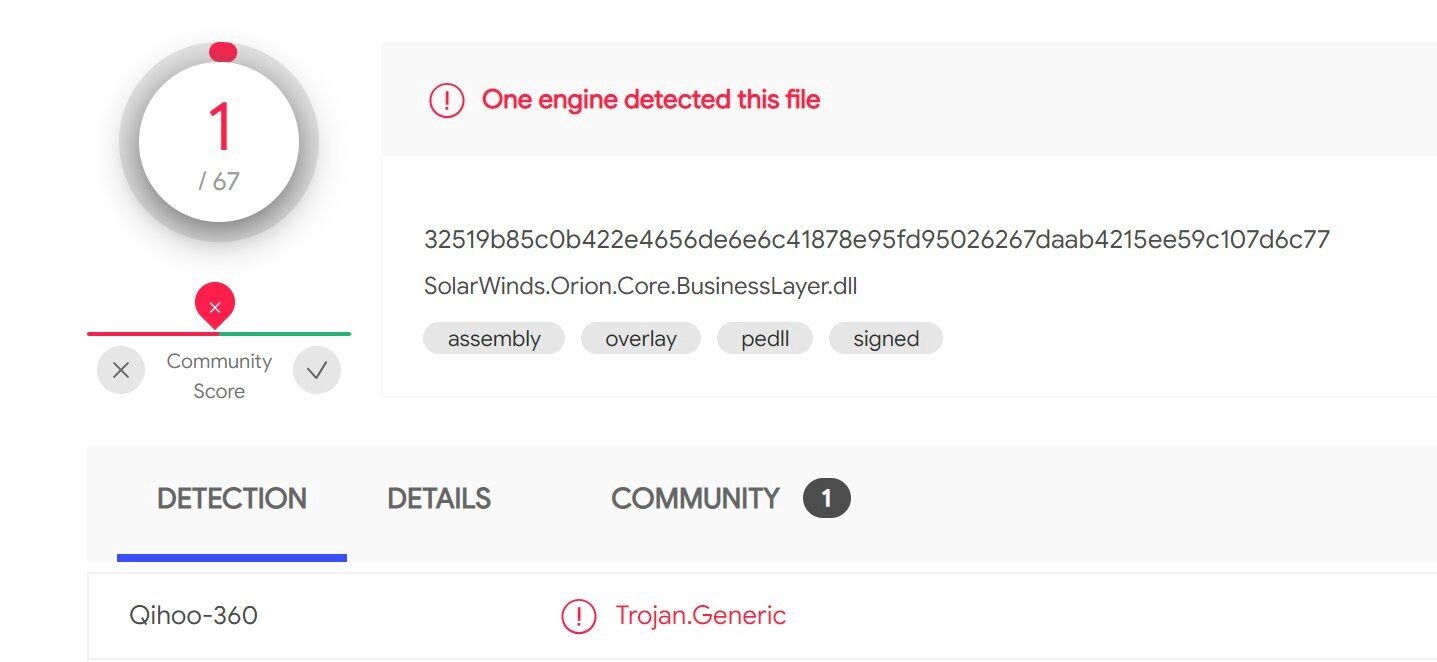
Screenshot from VirusTotal taken around 12am ET on December 14, 2020
At time of publishing, that’s up to 44 out of 70, and the number should continue to increase as more vendors add detections for this threat.
We are actively monitoring this threat to confirm whether or not there are any ties to SolarWinds N-central or SolarWinds RMM. So far, we have only seen evidence of this threat tied to SolarWinds Orion.
In addition, we have created Huntress Monitored Files to identify which endpoints have the backdoored files (SolarWinds.Orion.Core.BusinessLayer.dll) and to help uncover other future binaries that are currently unknown.
For users of our Managed AV beta, we are able to see if this Microsoft Defender threat was detected. At the time of publishing, we have not seen any instances detected.
Here are some resources we recommend reading:
So you want to roll your sleeves up and hunt, too? We have seen the SolarWinds.Orion.Core.BusinessLayer.dll present in multiple potential locations on the filesystem. Sharing is caring — so happy hunting!
Get insider access to Huntress tradecraft, killer events, and the freshest blog updates.
