

























Welcome to the Huntress Cybersecurity Blog, your go-to spot for staying ahead of hackers and boosting your cybersecurity savviness. Our blog contributors have focused on making cybersecurity education engaging and accessible for everyone.



Say Hello to Mac Malware: A Tradecraft Tuesday Recap
Why App Allowlisting and Zero Trust Solutions Alone Won’t Save You

CVE-2025-30406 - Critical Gladinet CentreStack & Triofox Vulnerability Exploited In The Wild
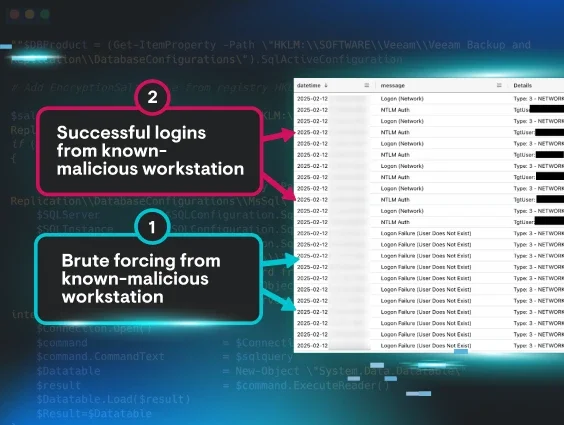
Brute Force or Something More? Ransomware Initial Access Brokers Exposed
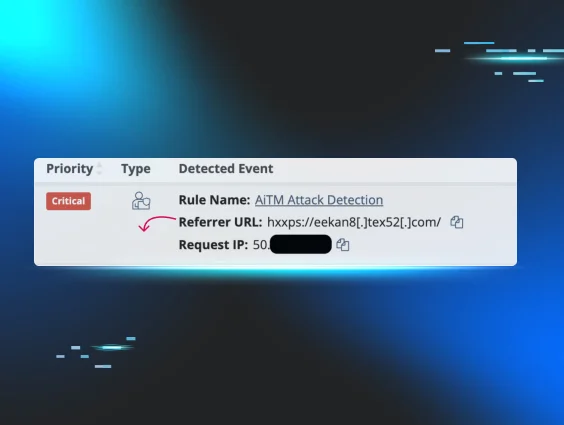
Identities Are the New Perimeter: Endpoints Are Only the Beginning

CrushFTP CVE-2025-31161 Auth Bypass and Post-Exploitation
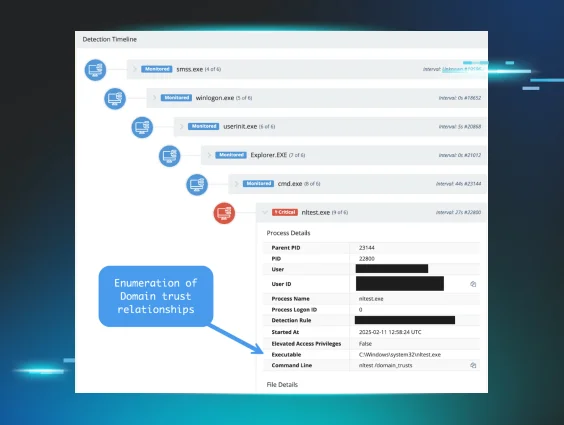
Cyber Hygiene Fails That Invite Hackers—and How to Shut Them Down
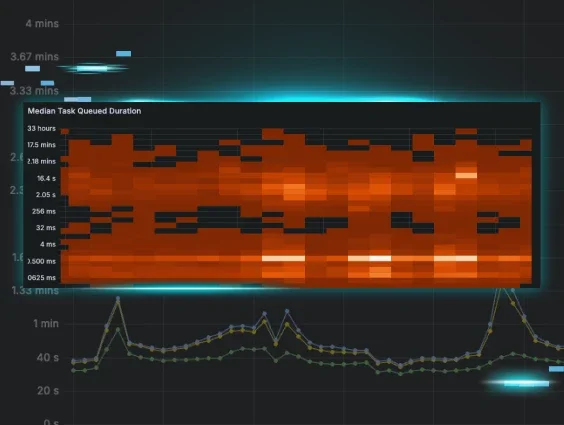
Scalable EDR Advanced Agent Analytics with ClickHouse
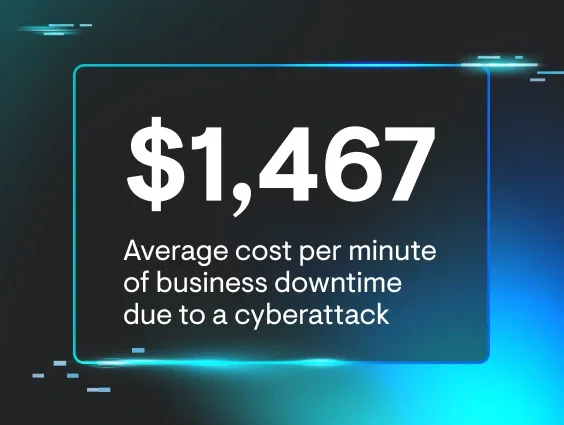
Neglecting Cybersecurity Can Save You Money Now. But It'll Cost You Down the Road.
Take Control: Locking Down Common Endpoint Vulnerabilities
The Ultimate Validation: Making a Hacker’s “Do Not Engage” List
Top 10 Worst Places to Store a Password

Get insider access to Huntress tradecraft, killer events, and the freshest blog updates.
