Threat actors use different means to steal credentials. To steal credentials from a user or endpoint usually requires threat actors to achieve some form of initial access, and this can be done via phishing, brute force, or some other means. Once on an endpoint, threat actors want to extend their reach by obtaining credentials for accounts with greater privileges, or just additional credentials, which can then allow them to reach into other endpoints on the network, moving laterally.
Credential theft: Initial access phase
One means of gaining initial access into endpoints is via phishing; that is, sending a user an email, hoping that the malicious content makes it to the user, and they access that content, as illustrated in Figure 1. This may provide the threat actor with a backdoor into the endpoint, or with the user’s credentials, or some other means of access.
Figure 1: Example of phishing email masquerading as a message from Docusign
Another means of gaining access to endpoints used by threat actors is SEO poisoning and malicious Google ads. Threat actors will look for software packages that users, and in particular system administrators, are searching for and will want to download. Then, they will package that software, which is often a free download, with their malware, and offer it up when someone searches for it. Once it’s downloaded, the user installs the legitimate software they were expecting, but also gets a little surprise they weren’t expecting, one that provides access to the threat actor
Another potential means of initial access is the use of vulnerabilities to exploit accessible services, or by brute force guessing passwords where authentication is required. One example of a vulnerable service was the FOUNDATION accounting software; in this instance, the purpose and use of the software required that it be publicly accessible, and the vulnerability to the software was that embedded credentials became known.
Other examples include Remote Desktop (RDP) and MSSQL server; if these services are exposed and publicly accessible, you can guarantee that at some point, someone (or several someones!!) is going to attempt to gain access via brute force password guessing attacks. This is why it’s important that administrators collect an accurate asset inventory (of systems and applications), and perform attack surface reduction. That way, if a service or application must be running, then it can be configured beyond the defaults to log the appropriate activity so that administrators can quickly respond to brute force attacks.
Credential theft: Post-exploitation activity
Once a threat actor has gained access to an endpoint, either through phishing or brute force, one means of stealing additional credentials is through the use of infostealers, which according to the recent Huntress 2025 Cyber Threat Report and shown in Figure 2, made up nearly a quarter of the threats across all observed incidents.
Figure 2: Frequency of threats, as observed by Huntress analysts
Another means of gaining access to credentials is to run freely available password recovery tools. Administrators may be observed running one or two such tools, in an attempt to assist a user or troubleshoot an issue, but threat actors are more often observed running several such tools in sequence, often via a batch file or script of some kind. In one incident, Huntress analysts observed a threat actor running the batch file !start.cmd, the first line of which contained the following command:
mode con: cols=50 lines=30
This command is used to configure the output to the console, and may not be something that’s observed in regular usage within many organizations. As such, it is provided here as it offers an excellent detection opportunity. Following this line, the batch file ran almost a dozen freely available password recovery tools, including (but not limited to) BulletsPassView, Dialupass, RouterPassView, and WebBrowserPassView. Threat actors may take this “shotgun” approach in an attempt to collect credentials from as many sources as possible, accepting that some may not bear fruit. Or, they may target specific content, attempting to copy off the password stores of specific browsers or other applications known to be in use on the endpoint.
Perhaps one of the most popular and well-known means of collecting credentials from an endpoint once a threat actor has gained access is to run Mimikatz, a freely available open-source tool used to gain access to credentials. Huntress SOC analysts have observed Mimikatz being used during a number of incidents, usually as a result of the threat actor’s use of the tool being detected, leading to quick isolation and remediation of the incident.
Credential theft via Registry hive dumps
A means of obtaining credentials for local accounts on the endpoint is through the use of native utilities, also known as “living off the land binaries” or “LOLBins.” One such utility is reg.exe, which allows administrators to interact with the Registry hives. This utility can be used to “dump” or save copies of the Registry hive files, via a command line such as the following:
reg.exe save hklm\system <path>
This command is then repeated for the Software and SAM Registry hives. Huntress sees a good bit of this activity delivered via lateral movement through the Impacket tool set, but these commands can also be run locally on the endpoint, via command prompt or PowerShell. This is likely due to the fact that the tool set is freely available, and the capability for running such commands across the network is built in, obviating the need to come up with your own means for credential theft.
Huntress analysts have seen other means for collecting Registry hive files. In one incident, the threat actor connected to the endpoint from a previously observed, known malicious workstation via PSExec and ran the following command:
"cmd" /c mklink /D C:\perflogs\Shadowcopy \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy102\
This command had not been preceded by a command to create a Volume Shadow Copy (VSC), but was instead preceded by a command to list the available VSCs. Attackers often abuse this legitimate Windows feature by creating VSCs to access Registry hives, so seeing this other technique is notable. The threat actor was then observed copying the Registry hives to their “ops folder:”
"cmd" /c copy C:\perflogs\Shadowcopy\Windows\System32\config\System C:\perflogs
As observed previously, these commands are then repeated for the Software and SAM Registry hives. Once obtained, a threat actor can run these Registry hives through a password cracking utility, such as Mimikatz or L0phtCrack, to obtain password hashes and perform dictionary and brute force password cracking attacks.
Other techniques
Another way to obtain the necessary information to conduct password-cracking attacks is to use various techniques to identify the Local Security Authority Subsystem Service (LSASS) process and dump the contents of process memory using a command line similar to the following:
%COMSPEC% /Q /c CMd.exE /Q /c for /f ""tokens=1,2 delims= "" ^%A in ('""tasklist /fi ""Imagename eq lsass.exe"" , find ""lsass""""') do rundll32.exe C:\windows\System32\comsvcs.dll, #+0000^24 ^0 \Windows\Temp\u3yb.sql
The above command line uses tasklist.exe to locate the LSASS process and then use the native comsvcs.dll to dump the process memory. An example of another, similar process being detected appears in Figure 3.
Figure 3: Process detection
To make this entire process easier and avoid having to crack password hashes, threat actors can “enable WDigest” using the following command line:
reg.exe add
HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest /v
UseLogonCredential /t REG_DWORD /d 1 /f
This command modifies the Windows Registry and tells the operating system to store credentials in plain text, rather than encrypting them. Setting this Registry value, and then returning to the endpoint some time later—perhaps several days—allows the threat actor to collect credentials in plain text, obviating the time it takes to crack passwords. This is an approach that Huntress analysts have observed previously, and has been observed used in combination with other techniques.
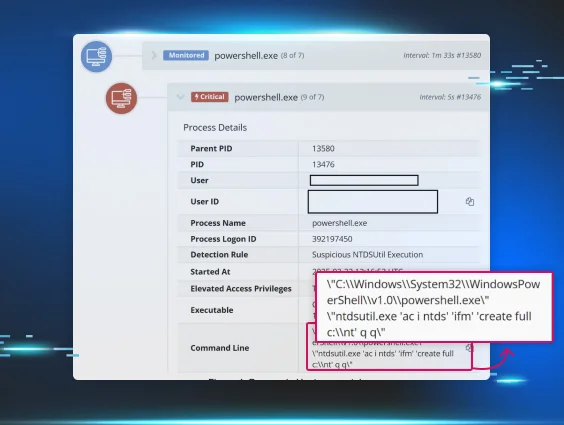
In order to obtain Active Directory credentials, threat actors will target domain controllers and attempt to obtain a copy of the NTDS.DIT file by using a command line similar to the following:
ntdsutil "ac in ntds" "ifm" "cr fu "<path>\ntds.dit" " q q
An example of another iteration of this command in the Huntress portal, along with it’s process parent, can be seen in Figure 4.
Figure 4: Process in Huntress portal
A similar approach to the one noted above—copying files from a Volume Shadow Copy—has also been observed with respect to the NTDS.DIT file.
Finally, it’s not unusual for threat actors to employ multiple means of credential theft. In a recent incident, Huntress analysts observed the threat actor accessing an endpoint via a previously compromised account. The threat actor then enabled the Guest account, added a new account to the endpoint, ran Mimikatz, and then installed Grzegorz Tworek's NPPSpy, configuring the endpoint for a “man in the middle” attack to collect plain text passwords.
Conclusion
In order to inhibit or even obviate a threat actor’s activities, it’s important to detect and respond to them as early in the attack cycle as possible. One way to do this is to understand what a threat actor’s activities might “look like” and understand ways in which these activities might be addressed. For example, organizations can look to security awareness training to address phishing attacks. And they can create an accurate asset inventory, and then follow that with attack surface reduction in order to address other types of attacks. Once these steps have been taken, organizations should strongly consider monitoring for unusual activity and changes to endpoints.