







In a recent episode of Tradecraft Tuesday, Huntress' UK ThreatOps Center Manager Dray Agha and Senior Incident Responder Harlan Carvey discussed the need to leverage an accurate asset inventory as a first step in reducing an organization’s attack surface.
These two activities, often underappreciated, serve as a linchpin in the broader strategy of fortifying an organization's defenses. Additionally, they set the stage for getting meaningful alerts from security information and event management (SIEM) or endpoint detection and response (EDR) monitoring, reducing the overall impact of an incident and making incident response and recovery a much smoother process.
The first, most critical step in attack surface reduction is an asset inventory; after all, if you don’t know what you have, how can you protect, monitor or respond to potential threats in your environment? Understanding which and how many systems are under your purview, and who manages and has access to them, is the first step to scoping, protecting, and monitoring the systems and applications that you own.
Asset inventory applies not just to physical or virtual systems, but also to the applications and servers installed on those systems.
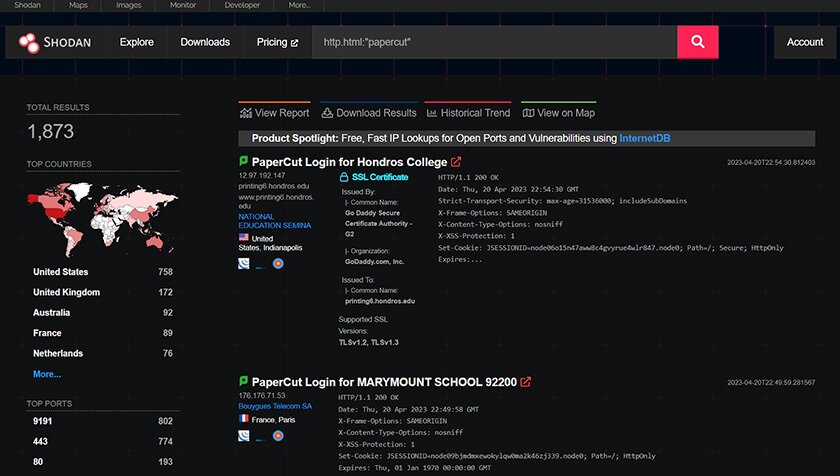
The first half of this year saw a number of issues arise with respect to installed applications, such as the PaperCut print management software, the 3CX VoIP Desktop Application and the MOVEit file transfer software. Part of a regularly maintained asset inventory program would ideally include a comprehensive listing of applications such as these, which systems they are installed on and their respective versions and patch levels.
For small businesses, it’s not unusual that some businesses will transfer to managed service providers (MSPs), or sign up for an MSP after having been established for some time. There may be long-standing, legacy means for remote access to endpoints, and that access may have been compromised.
Recently, the Huntress team observed several instances where legacy TeamViewer installations had been used to install cryptocurrency mining software. While cryptocurrency miners themselves may not seem significant, the fact that remote access was achieved via a legacy application that was compromised and left accessible should be particularly concerning.

Attack surface reduction can overlap considerably with asset inventory, as systems, applications or services found amongst the “assets,” but not required for business operations, should be removed, reducing the attack surface.
Stepping further into attack surface reduction, basic IT hygiene principles apply, in that if something must be run as part of a business function or process, do so as securely as possible. Ensure the system is offering only those services necessary to meet/service the function, ensure that the function is understood and that the necessary compensating controls and monitoring are in place.
Beyond patching, administrators can take additional steps to further reduce the attack surface of endpoints through configuration control of endpoints and applications. In February 2022, Microsoft announced that they were going to change the default behavior and block macros in MS Office files downloaded from the Internet.

Shortly after the announcement, some threat actors shifted to sending disk image (files with *.iso, *.img, *.vhd file extensions) files as email attachments, or embedding those files within archives, while others continued phishing attacks using macros in MS Office document attachments. Toward the end of 2022, “weaponized” OneNote files were observed being sent as email attachments. In March 2023, Huntress published a blog post with free copy-and-paste PowerShell code that can be used to reduce the attack surface for those three means of initial access, inhibiting or even obviating the attacks altogether.
Why does all this matter, and how does any of this effort make a difference?
Creating an accurate, comprehensive asset inventory of both systems and applications, followed by taking appropriate attack surface reduction steps, can go a long way toward increasing your ability to detect and respond to a threat actor much earlier in their attack cycle, inhibiting or even obviating the impacts of the attack. These basic IT hygiene steps not only enable more effective monitoring, but they can also lead to a significant reduction of false positive alerts, as well as reducing alert fatigue experienced by many security teams and SOC analysts.
Interested in learning more? Watch our Tradecraft Tuesday episode on-demand here.
If you’re not registered, be sure to join us for next time! Register now.
Get insider access to Huntress tradecraft, killer events, and the freshest blog updates.
