







Within the ThreatOps department at Huntress, we actively hunt for malware and adversary activity. We look for persistent footholds: the tell-tale sign and smoking gun at the crime scene that truly indicates there is evil on a machine. Most often, these persistence mechanisms lie in autoruns—things like scheduled tasks, services or startup programs.
In other cases, some footholds could be attached to separate programs and executed alongside them. Image File Execution Options, or IFEO, debuggers do exactly this—when one application is invoked, another specified application runs. The intent of this is to really run a debugging tool, but the functionality can be abused to kickstart malware or any other malicious code.
IFEO debuggers are one persistence mechanism we monitor within the Huntress platform. We categorize persistence mechanisms into what we already know and what appears to be a new discovery. In fact, within our dashboard, we have a dedicated section labeled “Hunting” where every single autorun across every single managed host is dumped into if it is something we have never seen before. Our ThreatOps analysts “go hunting” and dig through these findings to uncover new malware.
But this is not a story about new malware we found. This time, we are showcasing a novel defensive trick we saw in the wild.
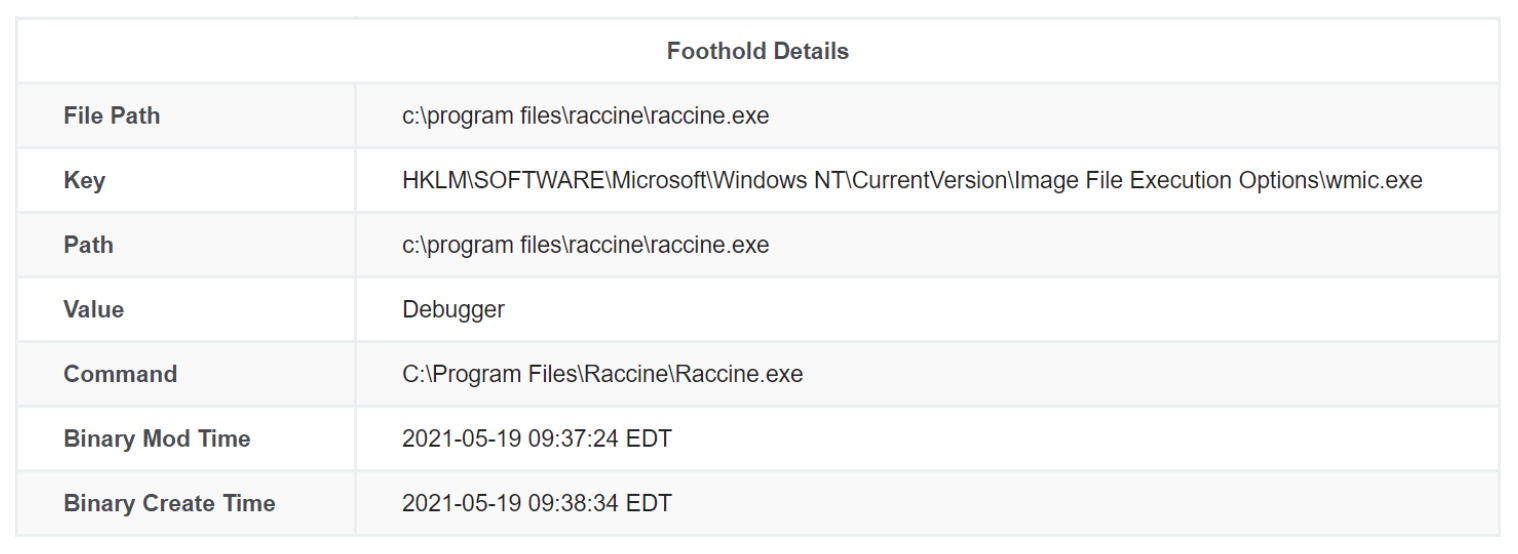
Suspicious autoruns are easily identifiable when the filename or path is full of random letters and numbers, but sometimes a static and defined name is just as interesting. This foothold caught our eye: “What is raccine.exe?” Could that be some clever name for a RAT (remote access Trojan)?
We could see the use of the IFEO debugger technique, which is not normal for software, so this piqued our interest. But this looked to be a program living in a sane directory. It resides in Program Files like a legitimately installed application. So what was this?
And so began our process of what Huntress ThreatOps analysts do best: hunt. We started to examine the program a bit more. Initially, it looked very suspicious—it apparently had been attached to a handful of native Windows programs as an IFEO debugger, not just wmic.exe.
After an extremely cursory analysis (seriously, just the `strings` command was all it took) we could tell the software was in fact called “Raccine,” and we had tracked down a version number.
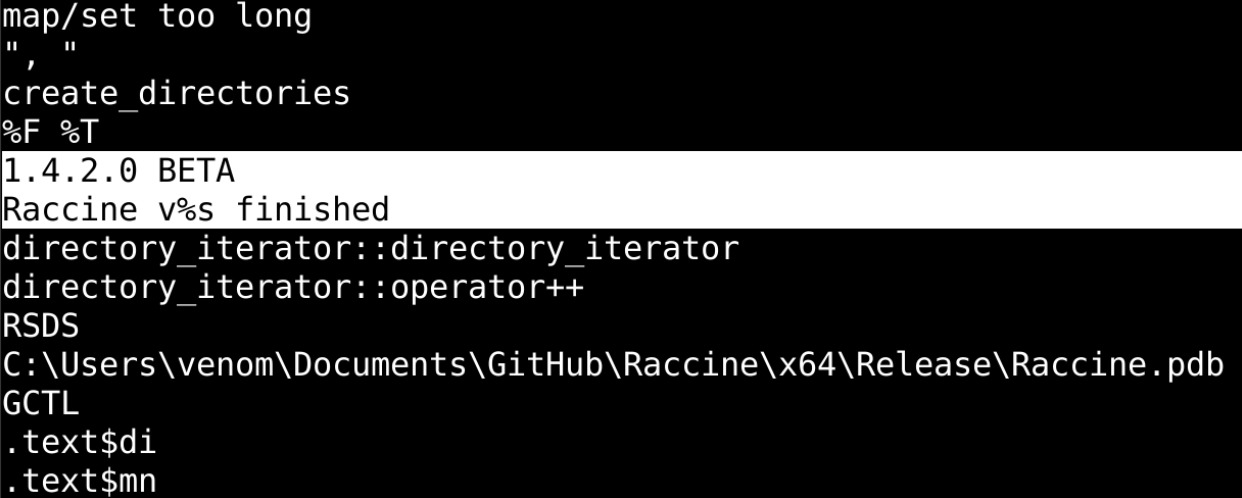
We also saw an IHDR PNG file header in the strings output, so we ran foremost to carve out other files. That led us to this image, seemingly a logo:

At this point, with a determined software name and version number, we figured we could likely do our own homework and research to see if this was a program known on the internet. With the logo image, we did a reverse image search to find any pages that included this picture.
Thankfully, this wasn’t hard to find.
As it turns out, Raccine is a known, public and open source utility developed by security researcher Florian Roth.
Raccine is maintained and developed in the public GitHub repository. It acts as “a simple ransomware protection.”
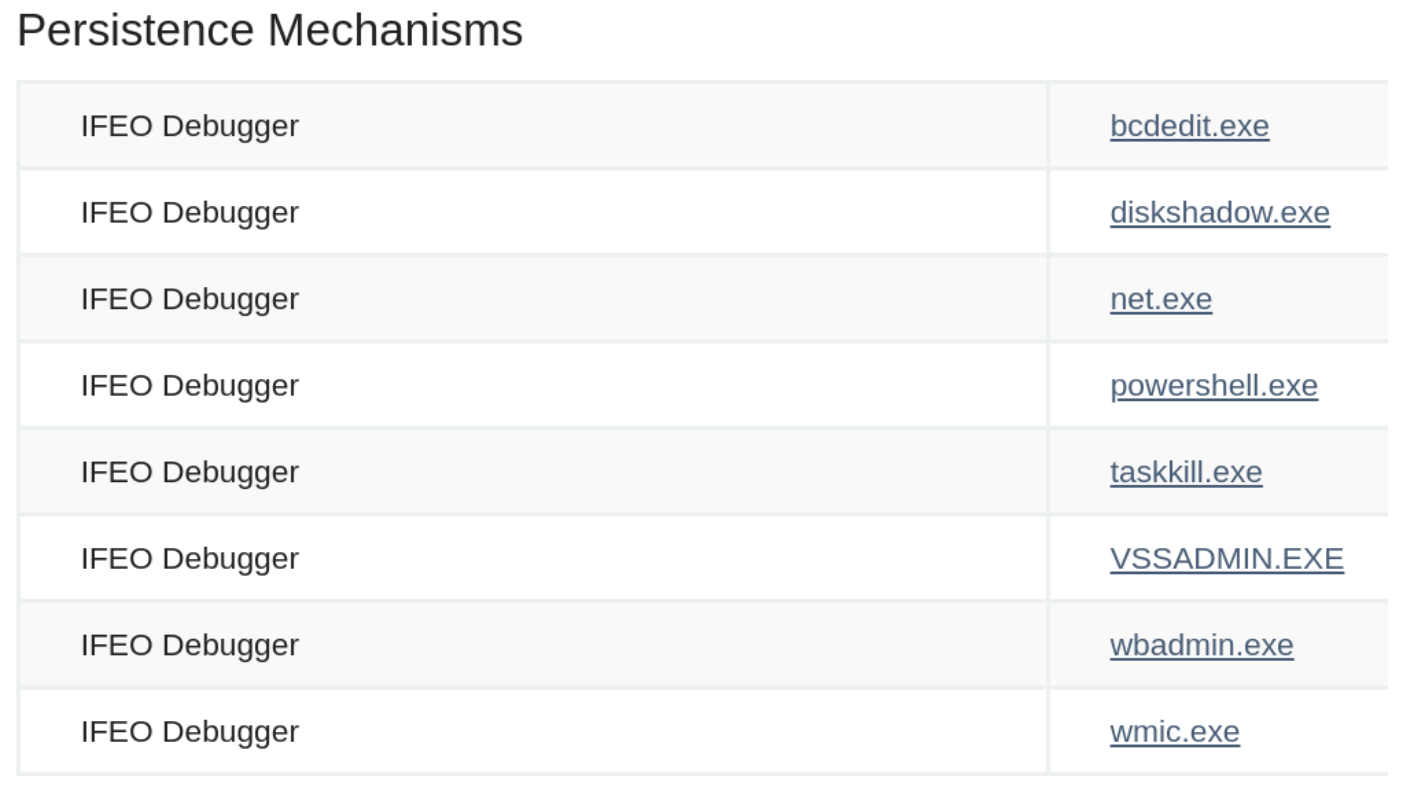
The README of the repository explains the function of the tool is to monitor for ransomware activity, like deleting shadow copies using native Windows programs like vssadmin.exe. If Raccine detects this or another unsafe syntax, it prevents the execution and stops all running parent processes...effectively neutering active ransomware or other malware.
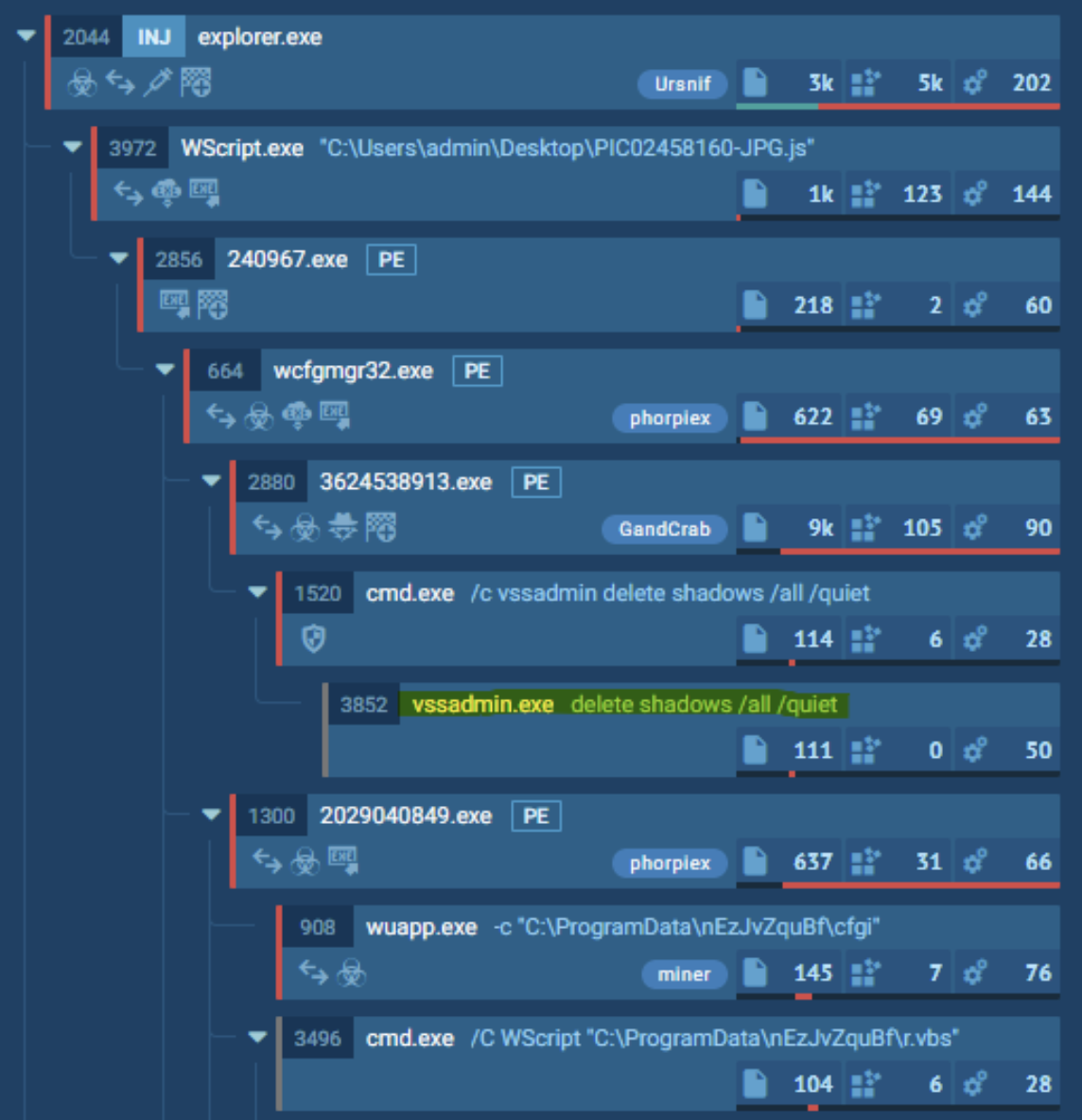
The Raccine repository includes a screenshot of a process tree shown in any.run, showcasing how ransomware might delete shadow volumes with vssadmin.exe.
How does it work? Well, by hooking onto IFEO debuggers, just as we saw in action! This is a novel technique considering the methodology is generic and simple, it does not clobber original system files and it does not require an additional executable or service.
For another visual representation of how effective this technique can be, check out the developer’s previous tweet showcasing screenshots comparing malicious activity with and without Raccine.
Raccine uses YARA rules that can be adjusted and fine-tuned to one’s needs, but the repository goes on to showcase how this can stop the infection of Emotet, RagnarLocker, Ryuk and more. It looks for malicious combinations of diskshadow, wbadmin, powershell and bcdedit, just as we found in our original screenshot.
Details in the official GitHub repository explain that Raccine can be automatically installed by a Batch script. It can be deployed via Group Policy, and it dumps information into a standard log file as well as the Windows Eventlog.
If you are interested in this utility, we encourage you to check the official source on GitHub and follow the maintainer, Florian Roth. Huntress is not affiliated with this tool or researcher, but we sincerely admire the ingenuity. It was a welcome surprise to see it out in the wild.
The repository poses a warning and reminds you to use the tool at your own risk. Commands that you may run manually, or potentially legitimate backup processes, could be blacklisted and get nerfed by Raccine. Your use of the tool is solely at your own discretion.
Note that many malware families are familiar with the Raccine utility, and some even try to remove or circumvent it. As always, there is no silver bullet or magic wand to stop cyber attacks—security is, and likely always will be, a cat and mouse game.
At Huntress, we tout the mantra, “our offense is your defense.” That idea stems from our roots, with our founders previously working in the intelligence community as cyber operators, and the understanding that knowing the adversaries means knowing how to best protect against them. We want to level up defenders, but we can also work to hinder the attackers.
Sometimes the same clever tricks and techniques that the offense uses can be pitted against them to stop them in their tracks. We use technology to make hackers earn every inch of their access—and finding another effort in this fight was a treat.
As ransomware runs rampant and malware makes a mess, Raccine may be a small solution to a larger problem. Looking through the pages on the repository and following conversations on Twitter, however, we see an incredible community effort from researchers sharing new ideas on detection, prevention, hardening and more. These are all strides to improve security as a whole.
Stumbling across this within our partner’s environments really made us smile. Innovations like this and proactive defense are some of the best ways to keep our world safe.
Get insider access to Huntress tradecraft, killer events, and the freshest blog updates.
