







On September 10, 2023, MGM Resorts and gambling operations in Las Vegas faced widespread disruption and loss of IT functionality. The action was subsequently linked to an entity referred to as “Scattered Spider,” an increasingly brazen and troublesome criminal threat actor. More significantly, subsequent reporting after the MGM incident revealed that another Las Vegas casino and hotel entity, Caesars Entertainment, was similarly victimized, potentially by the same group (but with no disruptive effect), at some time prior to September 7, 2023.
Notably, in both the MGM and Caesars events, most available information indicates that initial access and subsequent actions were enabled via social engineering of IT personnel. While details are still emerging from this event, with some reporting indicating the Caesars intrusion was a different group, Scattered Spider operations frequently leverage targeting individuals via social engineering mechanisms to capture credentials, enabling subsequent impersonation of the victim.

As previously discussed, targeting identities, especially through personal devices and accounts or in cloud environments, represents a recent and especially troublesome technique for defenders to counter, as demonstrated in the Las Vegas events.
While information on the two Las Vegas intrusions is still emerging (as of this writing), the link to Scattered Spider as, at minimum, an initial access broker enabling follow-on ransomware operations appears quite firm. While some initial reporting identified the ransomware entity ALPHV (also referred to as BlackCat) as responsible for the MGM event, previous reporting has linked the two entities with Scattered Spider actions overlapping with ALPHV observables. Unfortunately, the precise relationship between these (likely) distinct entities remains unclear.
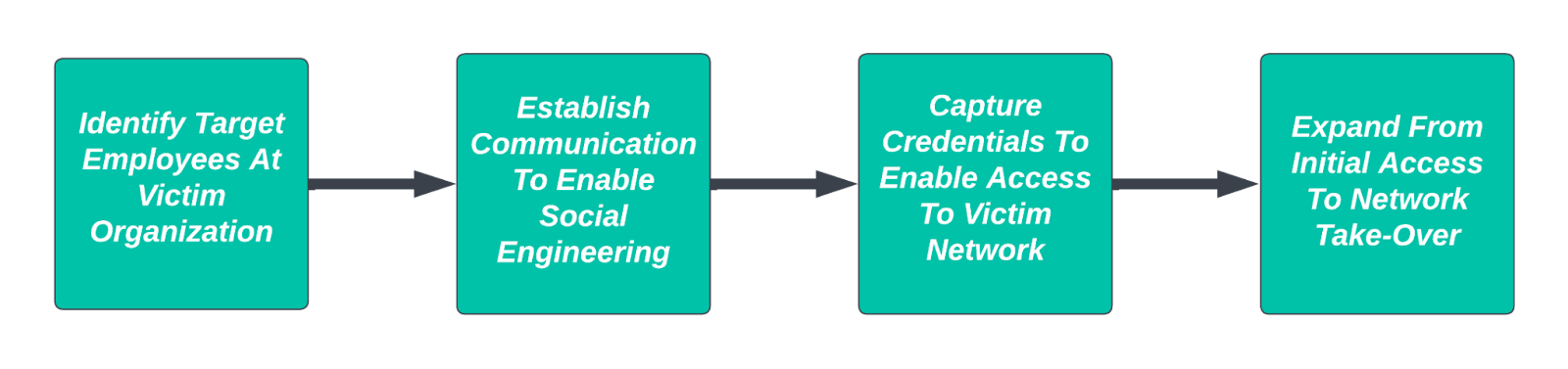
Irrespective of criminal group relationships, reference to Scattered Spider activity and social engineering mechanisms to enable the intrusion allow us to identify likely mechanisms for initial access. Specifically, Scattered Spider operations are historically correlated with the following types of identity-based actions:
Once Scattered Spider obtains access, a variety of techniques—from installing legitimate RMM tools for malicious purposes to more exotic mechanisms such as “Bring Your Own Driver” efforts or various tools and exploits—enable follow-on activity and lateral movement. Some of these items reflect traditional issues in identifying the malicious use of legitimate software, an increasingly common trend across both state-sponsored or -directed activity as well as cybercriminal operations.
Yet irrespective of follow-on actions, in nearly all known Scattered Spider instances, initial access still relies on targeting victim personnel at a very individual level in a way that evades or goes beyond typical security controls.
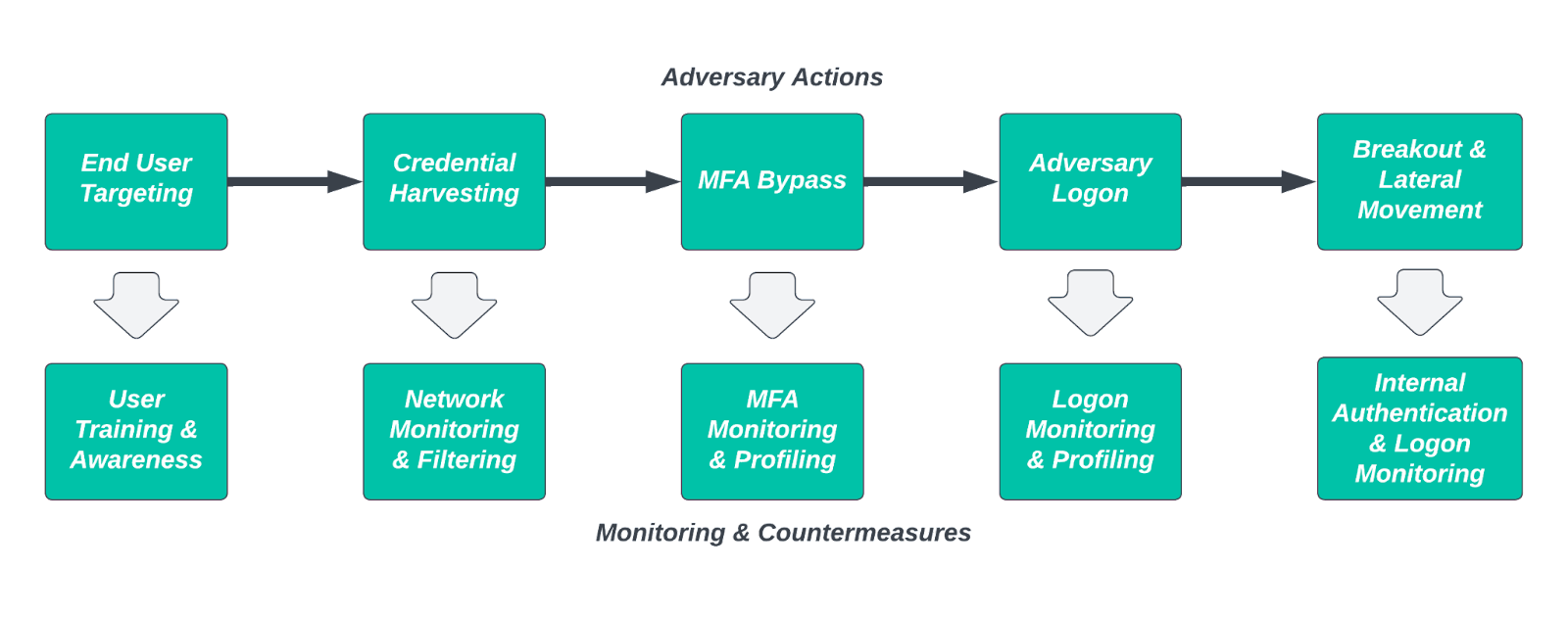
Threat actors and their associated behaviors are in constant coevolution with defender actions and capabilities. As defenders have gained increasing visibility into monitored environments and deployed various tools to identify clearly (or likely) malicious activity within these networks, adversaries have adapted. The trend toward living-off-the-land binary (LOLBIN) use or RMM abuse reflects one aspect of this action-detection arms race, and is an item requiring signal correlation and pattern recognition to address.

But alongside actions taking place within monitored environments, threat actors are moving beyond the network boundary to begin their intrusions where security teams typically lack visibility or monitoring capabilities. Scattered Spider’s actions, ranging from smishing attempts to SIM swapping on victim personal devices, reflect this shift. Rather than tackle a victim’s defenses head-on, the threat actor circumvents them entirely by essentially hijacking the identity of a legitimate, trusted employee of the victim entity.
In this environment, detection and response opportunities become far more complex and daunting than traditional security controls and countermeasures, where some assumption of a firm “boundary” exists between the internal network environment and the untrusted external internet. From an internal monitoring and hardening perspective, various “zero trust” security approaches and architectures become helpful, but do not enable visibility into the areas adversaries increasingly operate.
Instead, organizations must extend the monitoring perimeter to include, where possible, the services and infrastructure adversaries seek to subvert. Identifying logging or other data sources associated with third-party services or cloud applications is a vital first step. Actually monitoring and reviewing these items—and ideally correlating them with observations within the traditional network environment—is the next stage in defending against identity-focused intrusions.

Ideally, organizations incorporate these external application logs into existing security monitoring practices, or leverage a third party to perform this monitoring and alerting for them. Gaining visibility into critical identity-focused environments, such as cloud-based services and applications, is a necessary first step in even gaining awareness that something may be amiss.
Once the perimeter has been extended, then organizations can look towards implementing detections and controls to counter adversary activity.
In the case of Scattered Spider actions, applying methodologies such as user logon profiling (e.g., geographic and logical location profile for typical logon activity), monitoring for actions highly correlated with account takeover or abuse activity, or identifying and correlating instances of MFA fatigue with other observables all become vital actions. Follow-on controls can include security awareness and management when such activity takes place, leading to preventive actions or countermeasures such as disabling accounts or isolating assets “touched” by the potentially compromised identity.
There is a temptation to look at events such as the MGM and Caesars intrusions as illustrating humans as “the weak link” in security operations. While somewhat popular, this view is outdated and ignores the reality of a distributed, often remote workforce operating at speed. Users and the networks they operate within must be set up for success, instead of placing all onus for defense on individual user actions in an increasingly crowded and fast-tempo environment.

Establishing enhanced monitoring of behaviors associated with user identities and the application of identity trust is necessary to extend security coverage to areas threat actors increasingly target.
Obviously, this action is not as easy as simply saying, “users should take more training on social engineering,” but if applied robustly and accurately, a combination of monitoring and defense against user identity abuse will be far more effective in countering adversaries. Identifying critical external identity providers, authentication mechanisms, and similar functions thus becomes a needed function in modern IT and security operations. Hardening these items and monitoring them for abuse is not merely a luxury item—but rather a baseline necessity for the current state of operations.
Identity is increasingly targeted by adversaries as a mechanism to evade or circumvent security controls. While it may be tempting to shift blame to individual user actions, various breaches from state-directed actions to criminal operations rely on this type of abuse and, in many cases, eventually succeed irrespective of training or user awareness. To counter this threat, organizations must recognize the threat posed by identity-focused attacks, such as what appears to have taken place in Las Vegas, and implement appropriate visibility and controls to layer defense against them.
If you’d like to learn more about Huntress’ experience in thwarting identify-focused attacks, read our blog series starting here.
Get insider access to Huntress tradecraft, killer events, and the freshest blog updates.
