







Having an antivirus program is like having a lock on your front door—it’s a basic step and foundation for your overall security posture. However, they are only the start. The rapidly evolving cyber threat landscape demands a proactive and multi-layered approach to safeguarding critical assets and data.
While traditional, standalone antivirus solutions play a crucial role in detecting known malware, their limitations in detecting sophisticated and evasive threats call for additional reinforcement.

The first computer viruses in the 1980s were very predictable. They took advantage of how programs ran and inserted themselves in the middle of the process, hijacking an instruction in the program and forcing it to run its own code instead. No other program worked like the viruses in those days, and the first antivirus programs in the later half of the 80s took advantage of their unique methodology, easily rooting out anything that followed this process.
Ironically, the first antivirus programs were heuristic, or behavioral, in nature. However, as software became more complex, this became less sustainable for the technology at the time.
What followed was signature-based antivirus software. When a security team discovered a new type of malware, they would capture its unique fingerprints and place them in a database. Oftentimes, this was in the form of a hash, although other types of indicators do exist. Programming was still niche and required skill and patience at the time, which meant that even malicious programs didn’t change those fingerprints much over time and without a larger effort. Yet, just as technology has evolved, so has malware.
Nowadays, malware can change its look in real time by making small changes to its code. This can even happen without any interaction from the bad actors. Furthermore, malware can even be smart enough to try things to see if they work and adapt when they don’t—all on the fly.
An example of this is polymorphic malware. This is malware that’s designed to look different every time it runs but still produces the same result (as shown in Figure 1). An abstract example of this can easily be seen in math. For example, 4-2 and 1+1 will give you the same result, but the equation will look different from the outside.
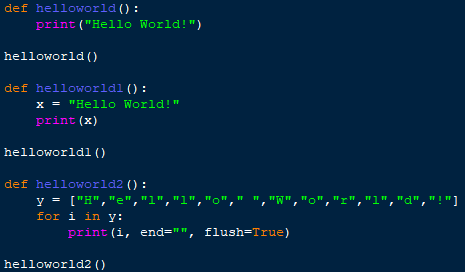
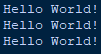
Figure 1: An example of how different functions yield the same result in Python
Because of this adaptability, signature-based detections only go so far. That isn’t to say that you shouldn’t have them; they are definitely a good deterrent and a solid fence for your protection. However, there are ways to get around fences. They can hop over them, tunnel under them, or even look for an open door. The same is true of malware.
Relying solely on AV leaves potential entry points unguarded. Just as it’s important to have more security features than a fence around something you want to protect (locks, surveillance, dogs, etc.), it’s important to have the same considerations when it comes to digital assets. This is where endpoint detection and response (EDR) comes in.

Rather than solely relying on predetermined patterns, EDR focuses on behavior. Think of it as a security camera that’s monitoring what’s going on in your house at all times. EDR is tuned to detect anomalous activities and patterns that might indicate malicious intent. This real-time behavioral analysis is a game-changer, helping catch threats that can slip past traditional signature-based methods.
When paired, AV and EDR form a formidable team. The real power, however, comes from having a team of experts who are constantly monitoring your security footage and can step in when needed.

The battle isn’t just against malware; it's also against time and bandwidth. Security teams are often stretched thin, grappling with time and resource constraints and the overwhelming task of monitoring endpoints and analyzing alerts. This alone can stretch teams to their limits—that’s why Huntress is built to solve for this problem.
At Huntress, we’ve got a 24/7 SOC team who can review, analyze and investigate suspicious activity, essentially keeping their eyes on all those security cameras for you. And we go beyond just surveillance. With Huntress Managed Antivirus, we integrate with Microsoft Defender, a built-in antivirus that's already in your Windows license.
This integration enhances the effectiveness of both solutions, allowing the Huntress SOC to take charge of incident investigation and response when Defender raises an alert. Our analysts possess a deep understanding of cyberattack tactics, techniques, and procedures (TTPs), allowing them to conduct in-depth investigations to differentiate genuine threats from false positives. In the event of a confirmed threat, our expert team devises targeted response measures to swiftly isolate affected endpoints, contain the threat, and provide remediation procedures (which in most cases can be automated to save the user valuable time).
Now let’s take a look at this power coupled with a managed EDR solution. Managed EDR, combined with expert threat analysis, offers businesses an advanced cybersecurity defense that surpasses the capabilities of standalone antivirus software. Huntress Managed EDR is how you can reap the benefits of these advanced insights while still being able to manage and leverage a built-in antivirus.
Huntress Managed EDR utilizes various detection techniques to identify anomalies in endpoint behavior. Unlike conventional antivirus tools that rely solely on signature-based detection, EDR solutions excel at spotting newer exploits and polymorphic malware by analyzing anomalous activities beyond known indicators. Expert threat analysts play a crucial role in fine-tuning these detection mechanisms and continually reviewing the latest intelligence to stay ahead of emerging threats.
Additionally, our Managed EDR provides our SOC with comprehensive visibility into endpoint activities through detailed telemetry data. This data encompasses process execution, registry changes, and antivirus detection information (when coupled with Microsoft Defender). Armed with this granular information, our SOC team gains a clearer picture of the attack surface, enabling them to identify threats, persistence and privilege escalation attempts. This level of visibility enhances the understanding of the threat landscape, facilitating faster and more accurate response.

Furthermore, Huntress employs proactive threat hunting to detect stealthy or persistent threats that evade signature-based detection mechanisms. Threat hunters comb through endpoint data, actively searching for Indicators of Compromise (IOCs) and unusual patterns that may indicate advanced threats. This proactive approach enables our security teams to identify and neutralize potential threats before they cause significant damage.
In today's complex and ever-changing cybersecurity landscape, relying solely on traditional antivirus solutions leaves organizations vulnerable to sophisticated attacks. Huntress Managed EDR, supplemented by an expert team of threat analysts, offers a robust and dynamic cybersecurity defense that proactively identifies, investigates and mitigates potential threats.
The fusion of advanced threat detection, deep endpoint visibility, proactive threat hunting and working with an existing antivirus solution makes Huntress a crucial component in modern cybersecurity architectures.

Get insider access to Huntress tradecraft, killer events, and the freshest blog updates.
