Recently, the Huntress Security Operations Center (SOC) team spent some time talking about what makes our endpoint detection and response (EDR) solution—and the team behind it—really stand out. Recently, Max Rogers, our Sr. Director of Threat Operations, teamed up with Dray Agha, our Manager of Threat Operations (UK), to discuss how their team does what it does to make sure our community can sleep a little sounder at night.
You can watch the full webinar—or keep reading for three main takeaways.
1. Humans make all the difference
Our 24/7 SOC team follows the sun.
As an analyst is signing off on the United States’ West Coast, our Aussie colleagues are just getting started.
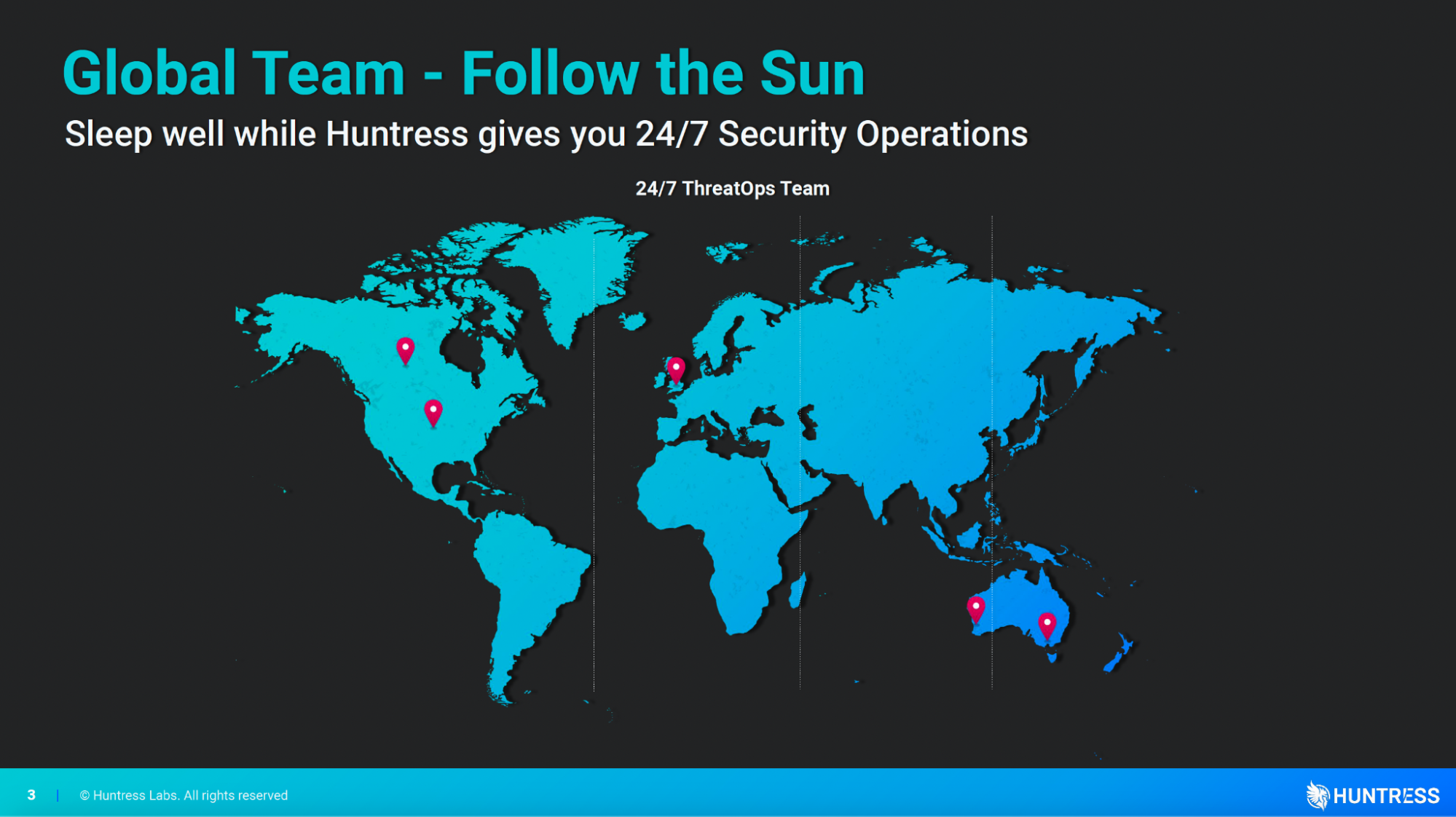
In turn, this ensures that our community has 24/7, 365 coverage of the environments we protect on their behalf.
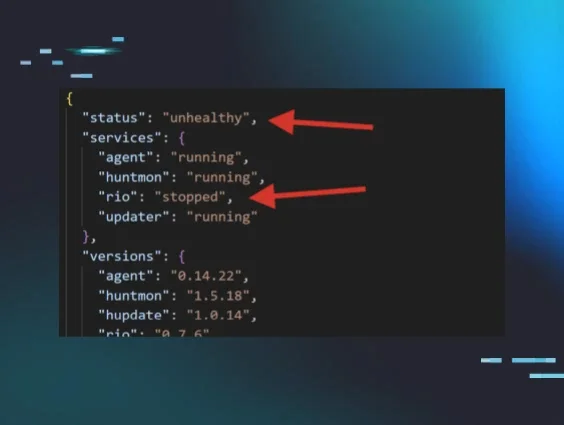
We pride ourselves on the human analysis aspect of our endpoint detection and response platform. We employ a team of expert cybersecurity forensic analysts who manually review security data from endpoints to identify potential security incidents. This human analysis provides our community with an extra layer of security and ensures that potential threats are caught.
It’s worth noting the (really badass) humans we have on our SOC team. They’re highly qualified cyber pros with years of experience at companies like CrowdStrike, FireEye, Red Canary, the National Security Agency, Tanium and Salesforce. We have the best, brightest minds on our team to make sure our partners have the expertise they need to minimize disruptions from threat actors.
We’re also continuing to expand globally—in fact, we just announced that we’re bringing the hunt to Australia and New Zealand. And we’re just getting started. 😉
2. Life before EDR kind of stunk
Before EDR really gained popularity, life in cybersecurity looked similar to what's described in the video below.

We had telemetry on both endpoints and networks to identify threats. We used logs and ticketing systems to detect, triage and investigate. Finally, we moved on to actually responding to the threat—reimaging devices, adding rules and rebooting when needed.
In short, life without endpoint detection and response only gave us half of the full picture once a threat was already active in an environment. Endpoint detection and response takes us a step further back in time with the ability to see what happened in the first place. With EDR, teams can move from being reactive to proactive.
In the webinar, Dray and Max cover a few examples of incidents their team has worked to triage on our partners’ behalves. For example, the 3CX compromise? It kept our SOC analysts a bit…busy.

Their process really is an incredible one to watch unfold. 😊
See what we mean in the videos below.


3. We're better together
We’ve said it before, and we’ll say it again and again: we’re better together.
The cybersecurity community is a strong, closely knit group that works so much better together than in silos between companies.
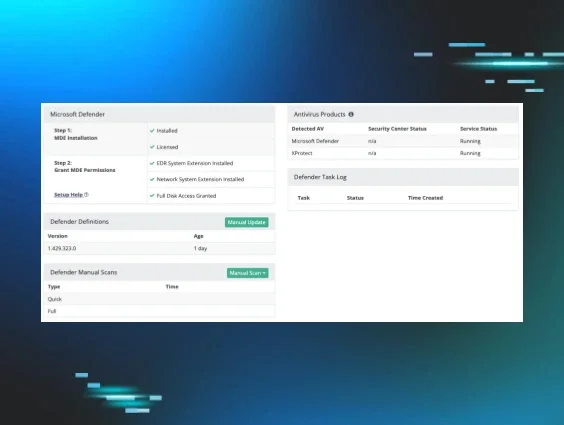
At Huntress, we take that same approach not just with humans, but with our product offerings. For that reason, we make it easy to integrate our platform with the security tools you already know and love—like Defender, the anti-virus free and built-in to every Windows machine.
The Huntress EDR platform is designed to integrate with other security tools. This integration enables you to provide your partners with a comprehensive cybersecurity solution. Our platform's open API also allows for easy integration with other tools, enabling you to customize the platform to meet your customers’' specific needs.
***