

























Welcome to the Huntress Cybersecurity Blog, your go-to spot for staying ahead of hackers and boosting your cybersecurity savviness. Our blog contributors have focused on making cybersecurity education engaging and accessible for everyone.



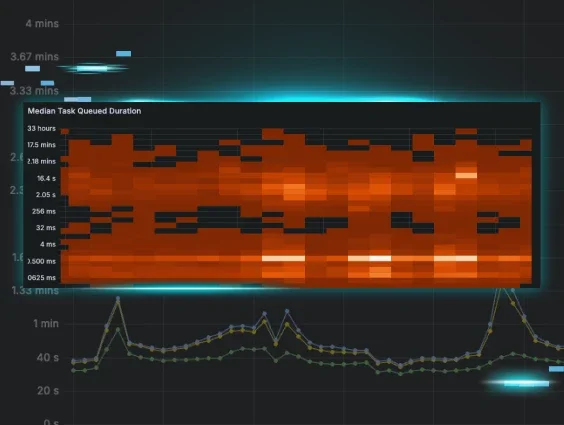
Scalable EDR Advanced Agent Analytics with ClickHouse
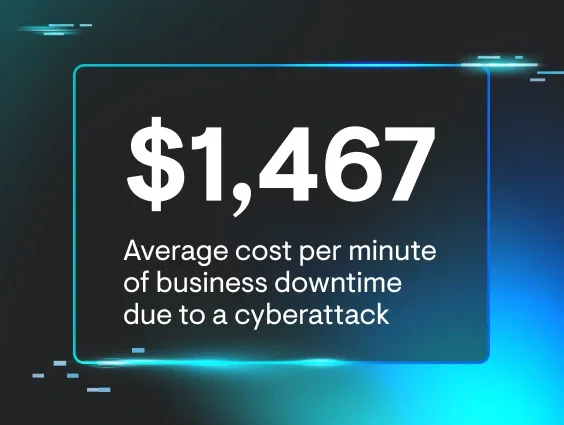
Neglecting Cybersecurity Can Save You Money Now. But It'll Cost You Down the Road.
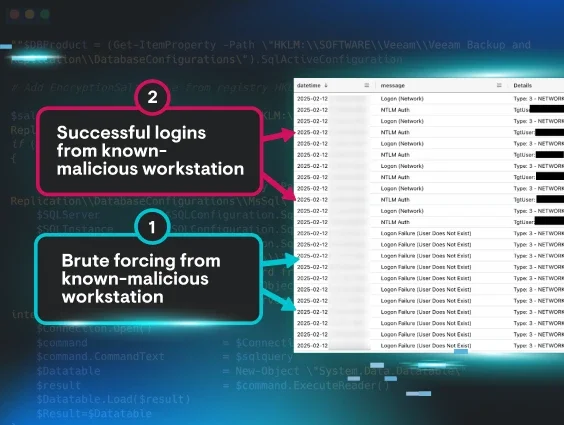
Take Control: Locking Down Common Endpoint Vulnerabilities
The Ultimate Validation: Making a Hacker’s “Do Not Engage” List
Ditching FUD for FUN in Security Awareness Training
Top 10 Worst Places to Store a Password
Untold Tales from Tactical Response
How to Detect and Eliminate Persistent Malware Before It Wreaks Havoc
The 2025 Cyber Insurance Trends Report

90% of IT Professionals Are Confident in Cybersecurity for Remote Work (New Data)

Cybersecurity Threats in Healthcare: The 2025 Huntress Report
How Huntress Achieved a Blazing Fast MTTR (and Why It Matters)
Unwanted Access: Protecting Against the Growing Threat of Session Hijacking and Credential Theft
Infographic: Uncover Tomorrow’s Cyber Threats Today
The Hunt for RedCurl

Get insider access to Huntress tradecraft, killer events, and the freshest blog updates.
