Examining the Impact of Ransomware on the Healthcare Sector and New HHS Guidelines


























Cybersecurity education should be accessible and actionable, not jargony. Welcome to your hub for mastering the fundamentals and beyond. Get education and advice from our experts to deepen your knowledge and stay ahead of cyber threats—made for all levels.




Examining the Impact of Ransomware on the Healthcare Sector and New HHS Guidelines

How a Pharmacy Cyberattack is a Warning Sign for Healthcare’s Cybersecurity Vulnerabilities
Top 10 Worst Places to Store a Password
Untold Tales from Tactical Response
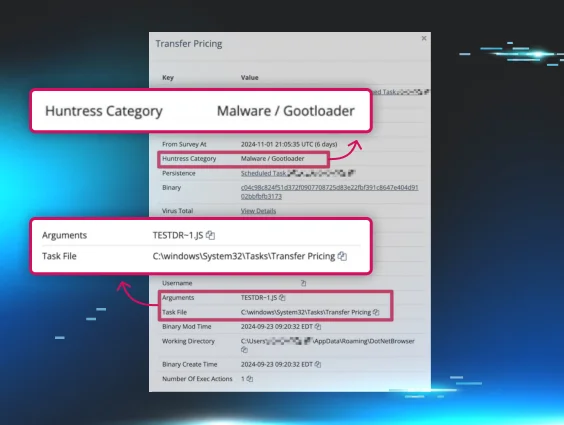
How to Detect and Eliminate Persistent Malware Before It Wreaks Havoc

Infographic: Uncover Tomorrow’s Cyber Threats Today
The Wall Street Journal Says SAT Programs “Do More Harm than Good.” Are They Right?

Huntress 2025 Cyber Threat Report: Proliferating RATs, Evolving Ransomware, and Other Findings

Never Just One Termite: Six Months of Researching OAuth Application Attacks
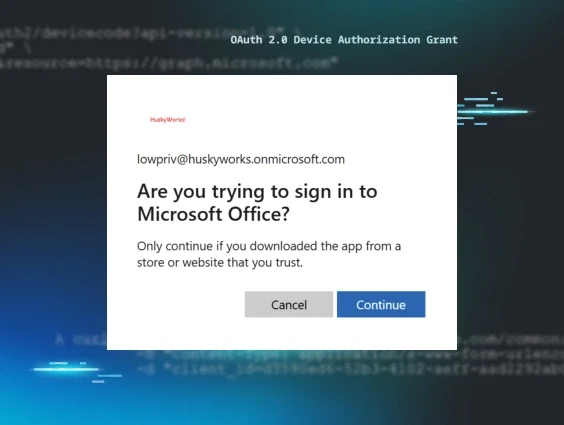
Oh, Auth 2.0! Device Code Phishing in Google Cloud and Azure

Why Every Business Needs Endpoint Protection in 2025
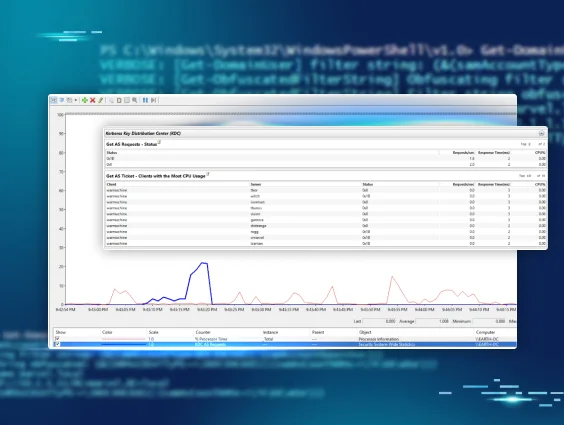
PerfMon! What Is It Good For?
Account Takeover: What It Is and How to Protect Against It
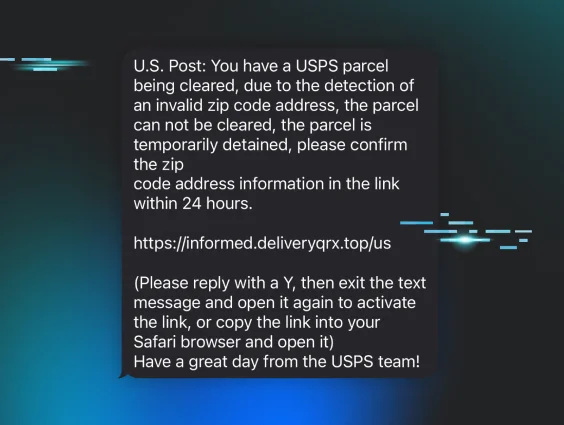
Exploring Package Tracking Smishing Scams
From Mandates to Assurance: How Managed SIEM Helps Decode Compliance Across the Globe
